Anthem Tryhackme Walkthrough: Exploit a Windows machine in this beginner level challenge. This task involves you, paying attention to details and finding the ‘keys to the castle’. This room is designed for beginners, however, everyone is welcomed to try it out! Enjoy the Anthem.
In this room, you don’t need to brute force any login page. Just your preferred browser and Remote Desktop.
Please give the box up to 5 minutes to boot and configure.
Reconnaissance
Starting with an nmap scan .
nmap -sS -sV -A <IP>
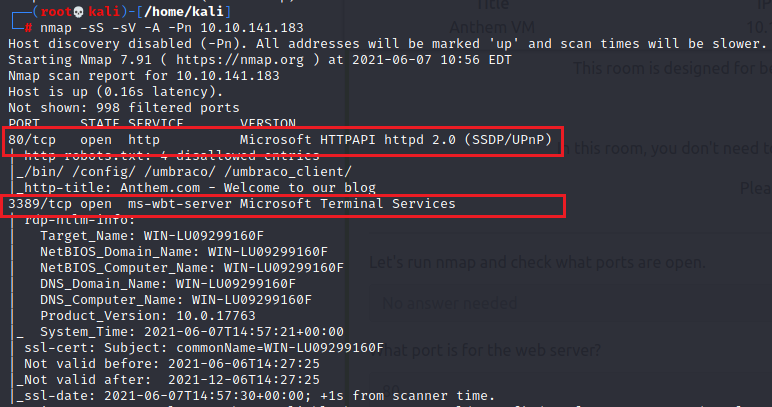
We discover 2 open ports 80 and 3389. There is port 80 open so it means there should a website.

Let’s see what the website has for us.
We can find our first couple of flags just by looking through the pages and checking the page source. Along with that sets run dirbuster to find the web directories.
Checking robots.txt
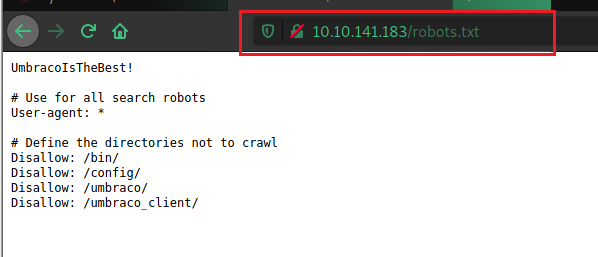
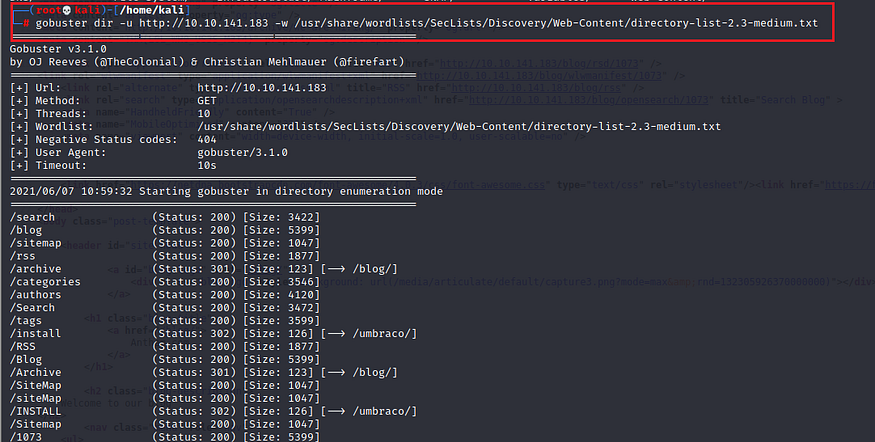
Here can have some juicy stuff and another flag.
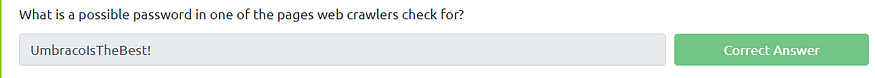
So we know UmbracoIsTheBest! is a possible password for some login

On one of the pages, we see this poem.
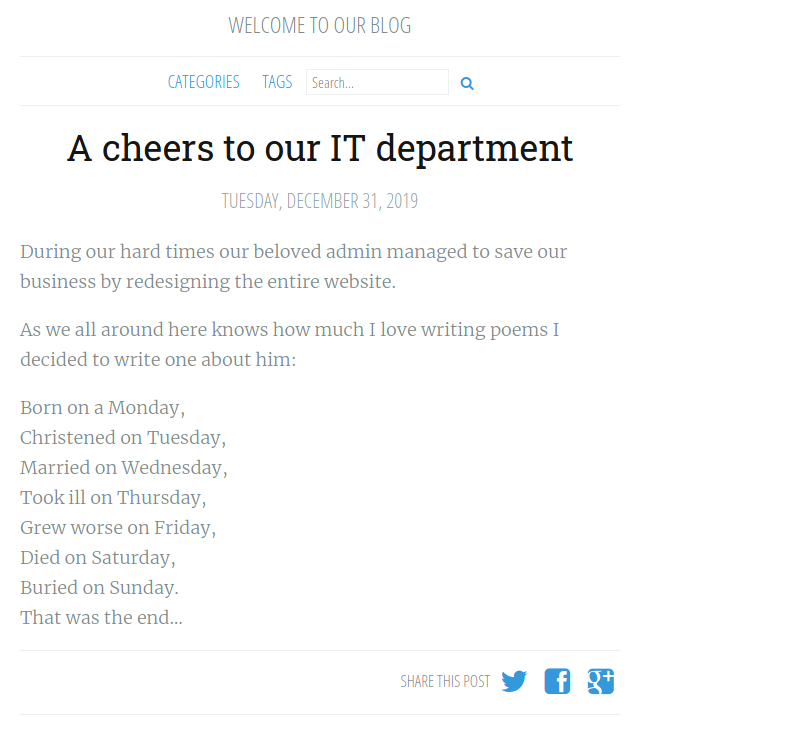
On further googling, we find that the author of this poem is Solomon Grundy
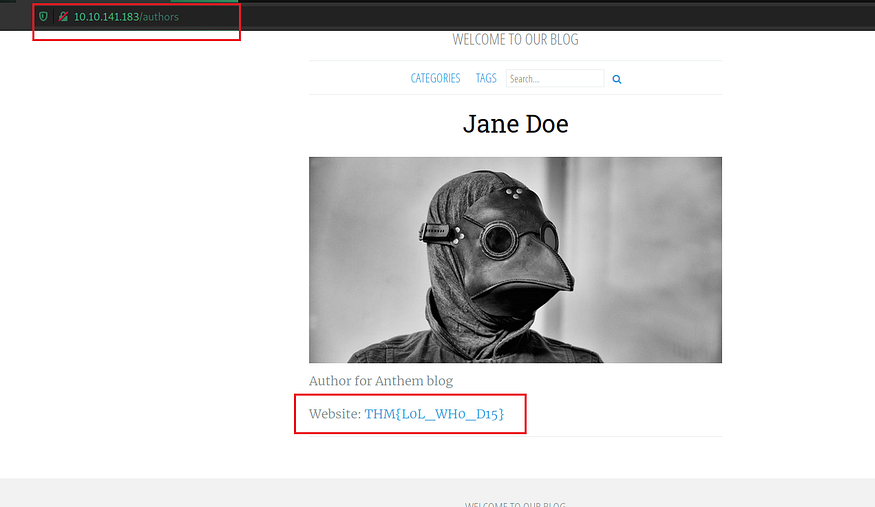
On one of the pages, we saw the email id of Author Jane Doe as JD@anthem.com
So it made sense that the email id for Solomon grundy would be also SG@anthem.com
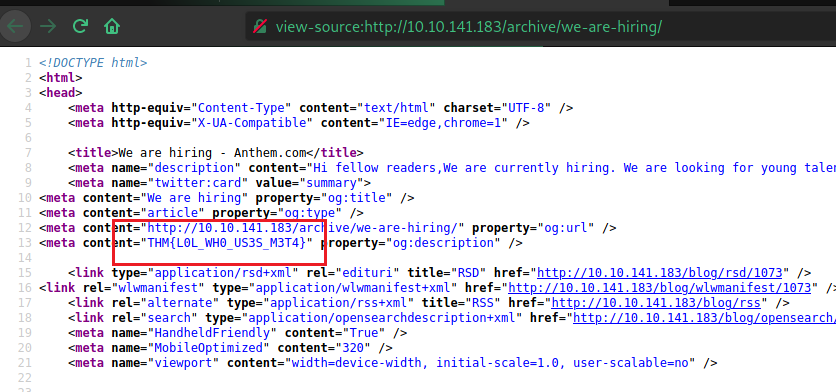
Checking the source code
http://<IP>/archive/we-are hiring/ > view source code

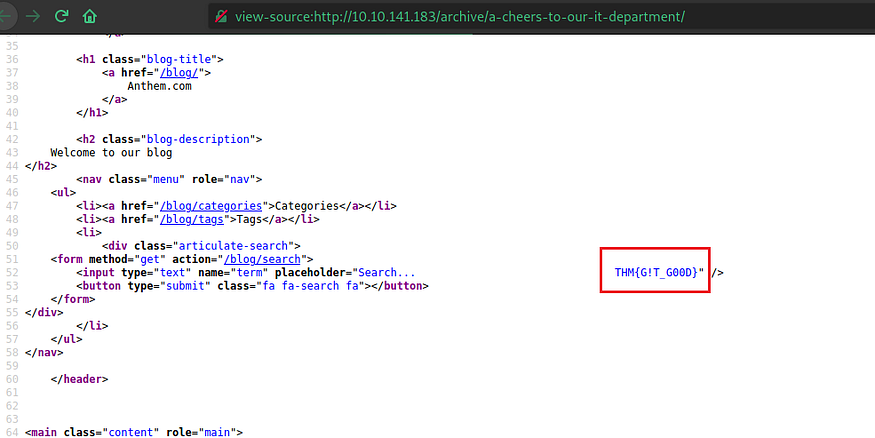
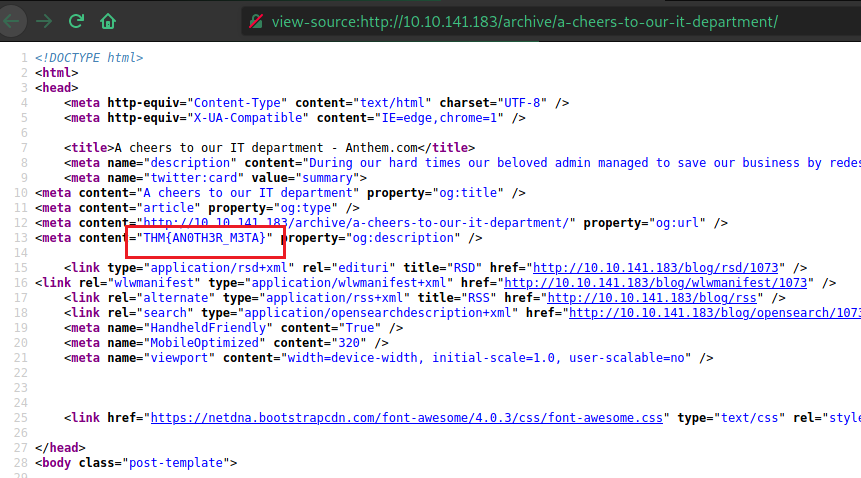
http://<IP>/archive/a-cheers-to-our-itdepartments/ > view source code
http://<IP>/authors/jane-doe/

http://<IP>/archive/a-cheers-to-our-it-departmenst/ > view source code
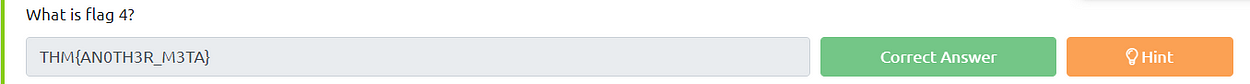
Finding the main flags
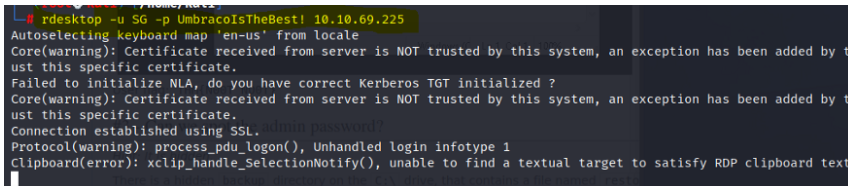
As we already know that we have a remote desktop port 3389 open, we use the already found credentials to log in.
Username — SG
Password — UmbracoIsTheBest!
rdesktop -u SG -p UmbracoIsTheBest! <IP>
Here we have our user flag.
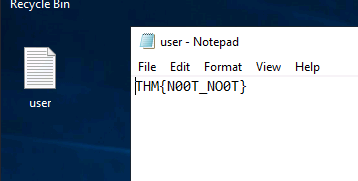
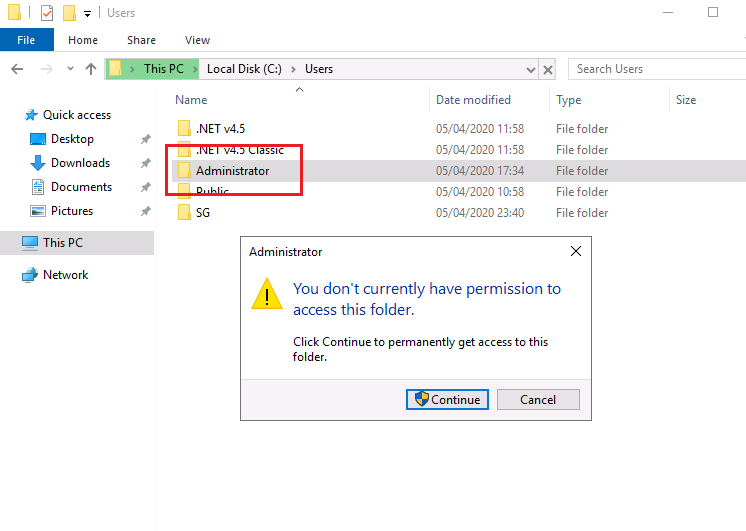
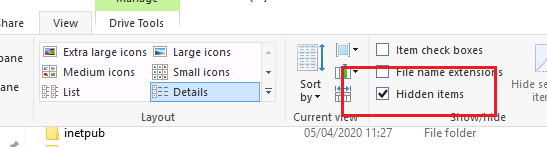
Now our root flag is hidden. There is a backup folder that has the password required to access the Administrator folder. Enable hidden items folder to view it.
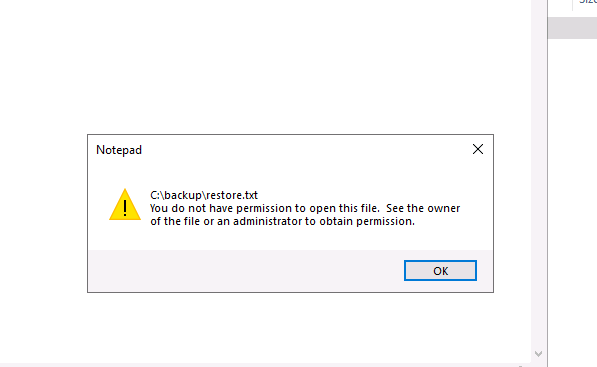
Inside the backup folder, we have a restore.txt file that we do not have permission to open. For that, we need to change permissions for this file.
select restore.txt > Right click > properties > security > edit >type SG and click check nanes> ok>apply.
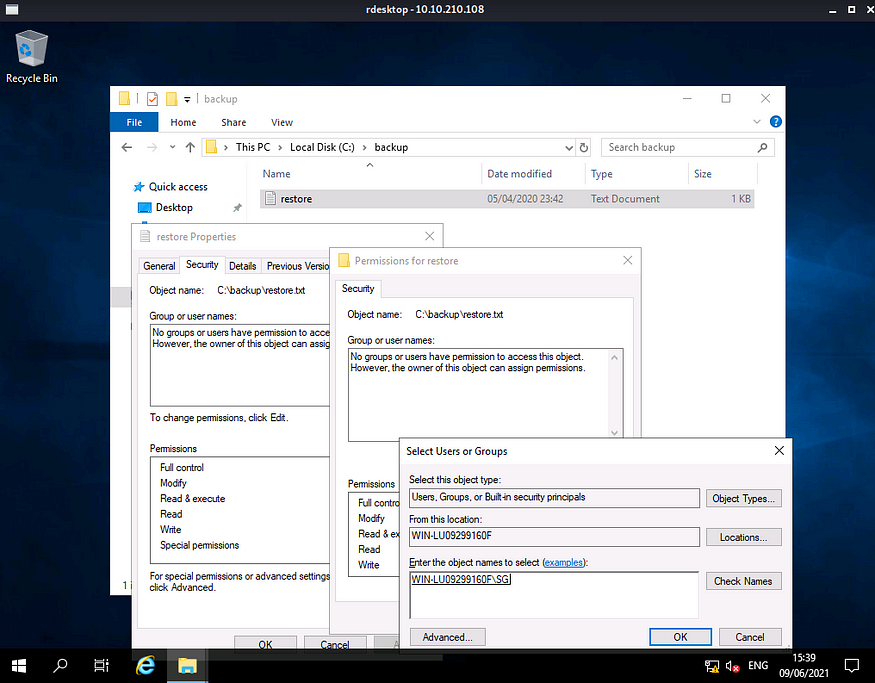
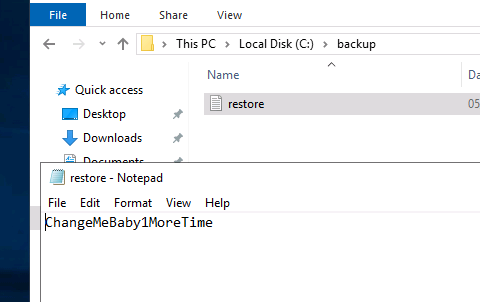
Now we can easily open the file and see the admin password
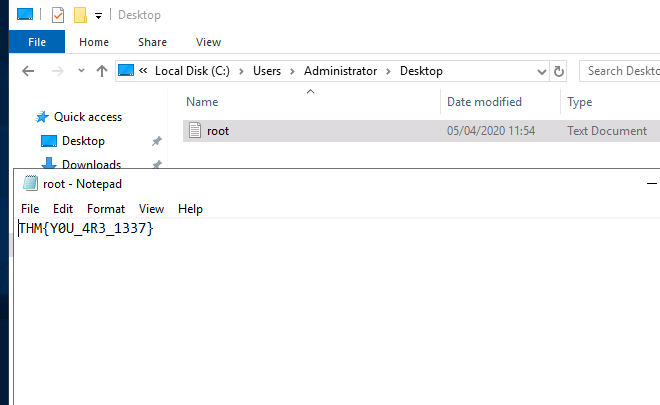
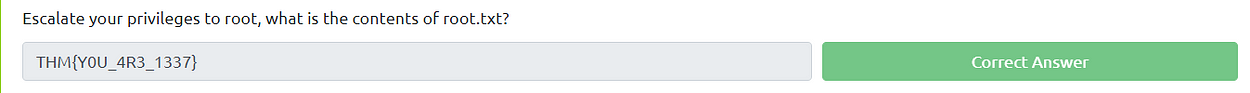
Using this we access the Administrator folder and get the root flag.
And we finished the room, leaves some claps if you found this helpful.
Read Also | Brooklyn Nine Nine Tryhackme Walkthrough











